|
|
We recommend you start small, maybe scan and report on one or two IPs. Review the reports, fix the vulnerabilities found, re-scan the IPs to verify your fixes, and rerun your reports. Once you have this process down you'll feel more comfortable scanning larger sets of IPs.
The simple answer to what to report on is this: any IPs in your account that have been scanned for vulnerabilities. IPs may include any devices on your network: routers, switches, hubs, firewalls, servers (all common operating systems), workstations, databases, desktop computers, printers, and wireless access devices.
Vulnerabilities must be identified and eliminated on a continuous basis because new vulnerabilities are discovered every day. For example, Microsoft releases advisories and patches on the second Tuesday of each month – commonly called ‘Patch Tuesday’. We recommend you schedule your scans to run automatically (daily, weekly, monthly) and create reports with at least this the same frequency. That way you'll always have the current vulnerability information for your hosts. You can even set up report schedules so your reports are launched automatically (daily, weekly, monthly).
You can choose to be notified via email each time a report completes. The email gives you a summary of the results and a secure link to the report. Select User Profile below your user name, go to the Options section and select Report Notification. You'll notice additional email notifications you can opt in to.
The scan settings you choose at scan time (option profile, authentication etc) impact how we conduct scans and which vulnerabilities are detected. We save scan results per scan within your account for your reference. Once scan results are processed we also save the vulnerability data per host - this makes it possible for us to include the latest findings in your reports. Keep in mind your reports will include the most recent vulnerability data we've found for each host, unless you create a custom report (template based) with host based findings. Learn more
Tip - We recommend you use consistent scan settings. This gives you the most accurate picture of your host security and vulnerability trends over time.
Check out: Patch Reports | Scorecard Reports | High Severity Report | Executive Report | Technical Report | Authentication Report | PCI Reports
Go to VM/VMDR > Assets > Host Assets to see the IPs you can scan for vulnerabilities and report on. If the IPs you want to report on are not listed then add them (or have your manager add them and assign them to you) and then scan them. One way you can tell if an IP address has been scanned is to do an asset search. Go to Assets > Asset Search, enter the IP and click Search. Your IP address will appear in the search results if it has been scanned. Just click it and you'll see host information including its current vulnerabilities.
Asset groups are user-defined groupings of host assets (IP addresses). You can group hosts by importance, priority, location, ownership, or any other method that makes sense for your organization. When you report on an asset group, only the hosts in the group are included. This allows you to limit the scope of your reports to a particular group of hosts or a subsection of your network, making the reports more manageable. Learn more
Asset tagging is another method for organizing and tracking the assets in your account. You can assign tags to your host assets. Then when launching scans and reports you can select tags associated with the hosts. This dynamic approach is a great way to ensure you include all hosts that match certain criteria, even if your network is constantly changing as hosts are added and removed. For example, scan and report on all Windows XP hosts or all hosts with Port 80 open. There are multiple ways to create tags, for example you can create tags from asset search (go to Assets > Asset Search) or by using the AssetView application. Learn more
Yes. If you've scanned IPv6 addresses, we'll display the IPv6 address in place of the mapped IPv4 address whenever possible. IPv6 addresses appear in vulnerability reports and the host assets list (after the mapped IP) for example. You'll need to have IPv6 Scanning enabled in order to perform IPv6 scans - please contact Support or your Technical Account Manager. Want to get started with IPv6 scanning? Learn more
To see security risk scores in your report, you'll need to create a scan report that: 1) is template based (go to Reports > New > Scan Report > Template Based), and 2) includes Host Based Findings, which is defined in the template.
We'll show a security risk score for the overall report (in the report summary) and a score per host (in the detailed results).
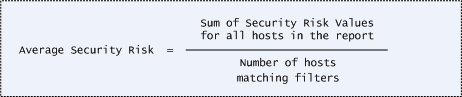
Score for overall report - This is the average security risk for all hosts in the report (all hosts matching filters). This is calculated as the sum of all security risk scores for all hosts in the report divided by the number of hosts.
This formula is used for calculating the average security risk for the entire report.

Score per host - The score for each host is either the average severity level detected on the host OR the highest severity level detected on the host. The calculation method used is based on the subscription setting at Reports > Setup > Security Risk. Only Managers can change the subscription setting. Note that all vulnerabilities and potential vulnerabilities are included in the security risk calculation per host. (Are you an Express Lite user? If yes, the average severity level is always used.)
What if I my report isn't sorted by host?What if I my report isn't sorted by host?
The security risk value displayed in the Detailed Results section of the report is the security risk for all hosts that match the sorting method (host, operating system, asset group, etc).
For example, if you sort by host you see the security risk for each host. If you sort by operating system you see the security risk for all hosts with the operating system. If you sort by asset group you see the security risk for all hosts in the asset group. The same methodology applies to the other sorting methods.
Don't see the score per host?Don't see the score per host?
Edit your scan report template and be sure to select Text Summary under Display > Detailed Results to show the score.
We'll show a business risk rating for asset groups in your scan reports. You'll need to create a scan report that: 1) is template based (go to Reports > New > Scan Report > Template Based), 2) has asset groups selected for the report target, 3) scan results selection is set to Status or Status and Trend, and 4) detailed results are sorted by asset group. The asset group's business impact level and security risk are factors used to calculate the business risk rating. A Manager can configure the method for calculating business risk in reports by going to Reports > Setup > Business Risk. (Express Lite users cannot edit the settings.)
What happens when security risk falls between two values? A linear interpolation between the two values is calculated.
Business risk for security risk 4 = 36
Business risk for security risk 3 = 16
Business risk for security risk 3.4 = 16 + [0.4 * (36-16)] = 24
Business risk for security risk 5 = 100
Business risk for security risk 4 = 64
Business risk for security risk 4.7 = 64 + [0.7 * (100-64)] = 89.2*
(*Note business risk will appear as 89 since the decimal is dropped)
Our reports are template based so you can easily change report settings and rerun reports to get different views of your vulnerability data and security risk. You can configure existing report templates and create new ones. Learn more
Add search lists to your vulnerability scan report template to filter the report to specific QIDs (static search list) or to QIDs that match criteria that you specify (dynamic search list). In your scan report template, go to the Filter section and select Custom under Selective Vulnerability Reporting. Then add custom search lists from your account or import search lists from our Library. Not sure how to create custom search lists? Just go to Reports > Search Lists > New.
While creating the New Scan Report Template (Reports > Template > New > Scan Template), you can choose the status (New, Fixed, Re-Opened, Active) to filter the vulnerabilities. These filters are only applicable when Host Based Findings is selected in the template (on the Findings tab).
You can easily create reports including vulnerabilities based on their published date using search lists. Learn more
It's possible that multiple kernels are detected on a single Linux host. By default we'll report all vulnerabilities found on all Linux kernels. Want to list vulnerabilities found on non-running kernels? Choose the "Display non-running kernels" option. Want to filter out vulnerabilities found on non-running kernels? Choose the "Exclude non-running kernels" option. Only 1 option may be selected at a time. Apply these options to your scan reports, patch reports and scorecard reports.
Don't see these options?Don't see these options?
A Manager must first opt in to the New Data Security Model by going to Users > Setup > Security. After opting in be sure to run vulnerability scans on the hosts you would like to report on.
How can I identify the running kernel on my host?How can I identify the running kernel on my host?
The running kernel on each Linux host is reported in Information Gathered QID 45097.
When selected, vulnerabilities found on a port/service that is not running are excluded from your reports. This filter applies only to certain QIDs. Apply this filter to your scan reports, patch reports and scorecard reports.
Which QIDs does this filter apply to?Which QIDs does this filter apply to?
This filter applies only to certain QIDs. Click the View QIDs link
in the template to see the QIDs. You can also find them in the KnowledgeBase.
Go to VM/VMDR
> KnowledgeBase and choose the search option "Non-running
services". You'll see  next to each QID applicable to this filter.
next to each QID applicable to this filter.
We may detect software on a host that is considered vulnerable, however there’s a specific configuration present on the host that makes it not exploitable. When selected, we will exclude vulnerabilities that are not exploitable because of the host configuration. Apply this filter to your scan reports, patch reports and scorecard reports.
Which QIDs does this filter apply to?Which QIDs does this filter apply to?
This filter applies only to certain QIDs and configurations. Click
the View QIDs link in the template to see the QIDs. You can also find
them in the KnowledgeBase. Go to VM/VMDR
> KnowledgeBase and choose the search option "Not exploitable
due to configuration". You'll see  next to
each QID applicable to this filter.
next to
each QID applicable to this filter.
This option appears in scan report templates, under Filters. Select this option to exclude Microsoft patch QIDs that are superseded by another Microsoft patch QID recommended for the same host. A missing patch is identified by a QID like any other vulnerability.
Using search lists? For a custom vulnerability report using search lists, please note that the results from supersedes logic may be altered by the limited scope of QIDs included in the report due to search lists. Learn more about how search lists affect report output
Notes:
- This filter is only honored when Host Based Findings in selected in the template (on the Findings tab)
- This filter only applies to Operating System (OS) level patch QIDs
For scan reports in XML format - You may choose to exclude the <GLOSSARY> tag and this will reduce the size of your reports. Whether or not this tag is included depends on if you've selected any of the "Vulnerability Details" sub options in the scan report template like Threat, Impact, Results, etc. These options appear on the Display tab in the template.
- the <GLOSSARY> tag will be excluded from the XML format if none of the “Vulnerability Details” sub options are selected
- the <GLOSSARY> tag will be included in the XML format if any one of the “Vulnerability Details” sub options is selected
Your scan(s) must be complete. You'll know this when the scan status shows "Finished" on the scans list.
And scan results must be ready. We'll merge (process) your scan results into your account after the scans finish. This process involves indexing the scan findings per host. Watch for the solid green circle ![]() next to your scans in the scans list to know whether the scan results are processed. Then you're ready to launch reports - and the vulnerability data from the processed scans will be included.
next to your scans in the scans list to know whether the scan results are processed. Then you're ready to launch reports - and the vulnerability data from the processed scans will be included.
We maintain the industry's most comprehensive Vulnerability KnowledgeBase with more than 26,000 vulnerabilities across hundreds of applications and operating systems. We scan for vulnerabilities in a broad range of categories, including: back doors and trojan horses, brute force attacks, CGI, databases, DNS and Bind, e-commerce applications, file sharing, FTP, firewalls, General Remote Services, hardware and network appliances, mail services, SMB/Netbios Windows, TCP/IP, VMware, VoIP, web servers, wireless access points, X-windows and more. Go to the Search option in the KnowledgeBase to see a complete list of vulnerability categories.
Our engineers develop vulnerability signatures every day in response to emerging threats. As soon as these signatures pass rigorous testing in our Quality Assurance Lab they are automatically made available to you for your next scan. No user action is required. In addition, you can sign up to receive daily or weekly vulnerability signature update emails, detailing the new vulnerabilities we're capable of detecting.