Scan your systems to identify vulnerabilities and understand your security posture. By automating your scans, you'll get an up to date vulnerability posture in real-time.
Are you ready to scan?
There are some steps you'll want to take in your account to get ready for scanning like install scanner appliances, identify hosts to scan, configure and enable authentication, and customize scan settings in option profiles. See Steps to Take Before You Scan.

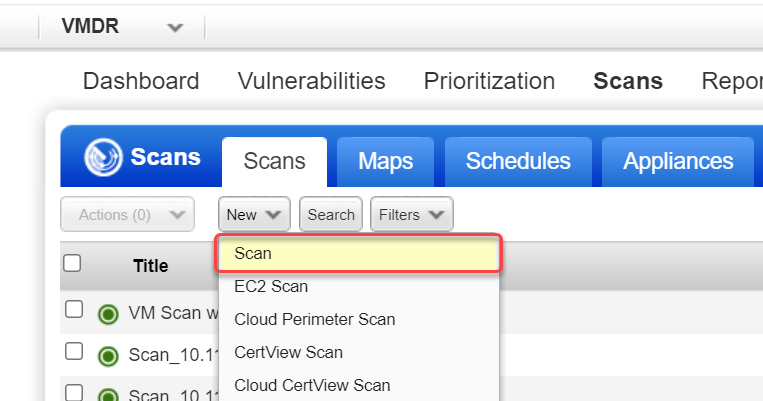
In the Launch Vulnerability Scan window, the first section you'll see is the General Information section. This is where you give the scan a title and select basic scan details like which option profile to use, which scanner to use, etc. Each option is described below.
Title - Give your scan a title to easily identify it later.
Option Profile - Select an option profile for this scan job. The option profile has scan settings like which ports to scan, which QIDs to scan and whether to use authentication. The option profile designated as the "default" profile for the subscription is recommended. You can use the default or pick another option profile from the list. Get help choosing an option profile
Processing Priority - If you have an important scan that you want to be processed before other scans, then you can prioritize it. Choose from nine priority levels with the highest priority being "1 - Emergency" and the lowest priority being "9 - Low". Scans with no priority will be processed after scans with priority. Get help choosing processing priority
Network - (Visible only when the Network Support feature is enabled for your subscription.) Select the network you want to scan. The Global Default Network is selected by default but you can choose a user-created network from the list.
Scanner Appliance - (Visible only when you have Scanner Appliances in your account.) If this option does not appear, then your scans will use external scanners automatically.
Click here to see your Scanner Appliance optionsClick here to see your Scanner Appliance options
Select one of these options on the Scanner Appliance menu:
- Choose "External" to use our cloud scanners to scan IPs on your network perimeter.
- Choose a single scanner appliance from the list by name or use the "Build my list" option to select multiple appliances to scan IPs on your internal network.
- If you plan to scan asset groups, you can pick "All Scanners in Asset Group" and we'll distribute the scan across appliances in each group. Learn more about "All Scanners in Asset Group"
- If you plan to scan asset tags, you can pick "All Scanners in TagSet" to use scanner appliances with the same tags assigned as the scan target. Learn more about "All Scanners in TagSet"
- If you have the Network Support feature enabled, you can pick "All Scanners in Network" to use all appliances in the network you're scanning.
- Choose "Default" with asset groups as your scan target and we'll use the default scanner appliance defined in each asset group. Choose "Default" with IP addresses as your scan target and we'll use our External cloud scanners.
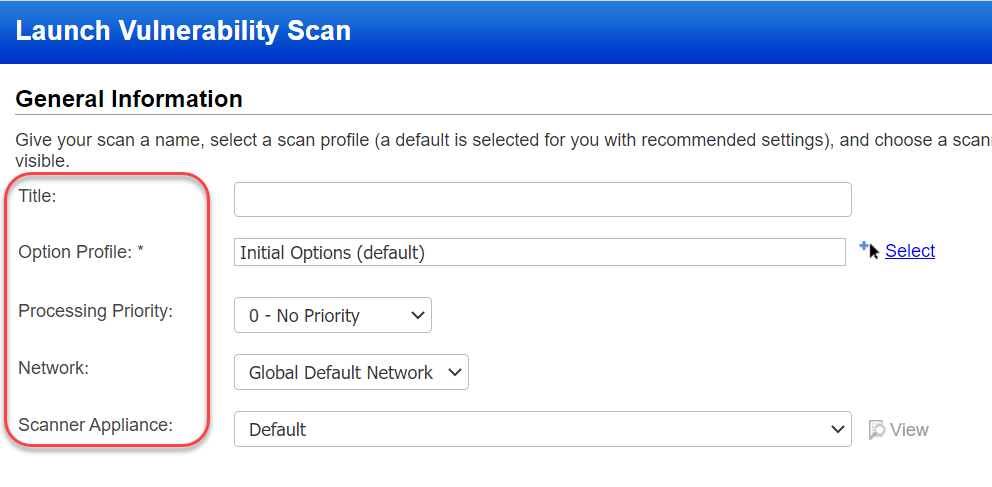
You can choose target hosts from Assets (IPs, asset groups, FQDNs) or from Tags.
Choose Target Hosts from "Assets"
Select the Assets option to specify the scan target using any combination of IP addresses, asset groups and FQDNs.
Asset Groups - When you scan asset groups, we'll scan all the IPs in the asset groups. Enter the asset groups you want to scan by name, or click the Select link to pick from a list of asset groups in your account.
IPv4 Addresses/Ranges - Enter the IPv4 addresses/ranges you want to scan. Use commas to separate multiple IPs and ranges. Optionally, click the Select link to pick from a list of IPs and ranges in your account.
Exclude IPs/Ranges - We won't send any scanning traffic, including ICMP, TCP and UDP probes, to hosts that are excluded. Enter the IP addresses/ranges you want to exclude from the scan. Use commas to separate multiple IPs and ranges. Optionally, click the Select link to pick from a list of IPs and ranges in your account.
FQDN(s) - (Visible only when the DNS Tracking feature is enabled for your subscription.) When this feature is enabled, you'll see the FQDNs input field where you can enter a comma separated list of Fully Qualified Domain Names to scan (e.g. www.abc.com, www.xyz.com). Enter up to 4000 characters. Each FQDN must resolve to an IP address in your VM account to successfully scan it and view the results. The Scan Results report shows the FQDN information in the Report Summary section. Click here to learn how to enable this featureClick here to learn how to enable this feature
To enable this feature, the Manager primary contact goes to Scans > Setup > DNS Tracking and checks the option Enable DNS Tracking for hosts.
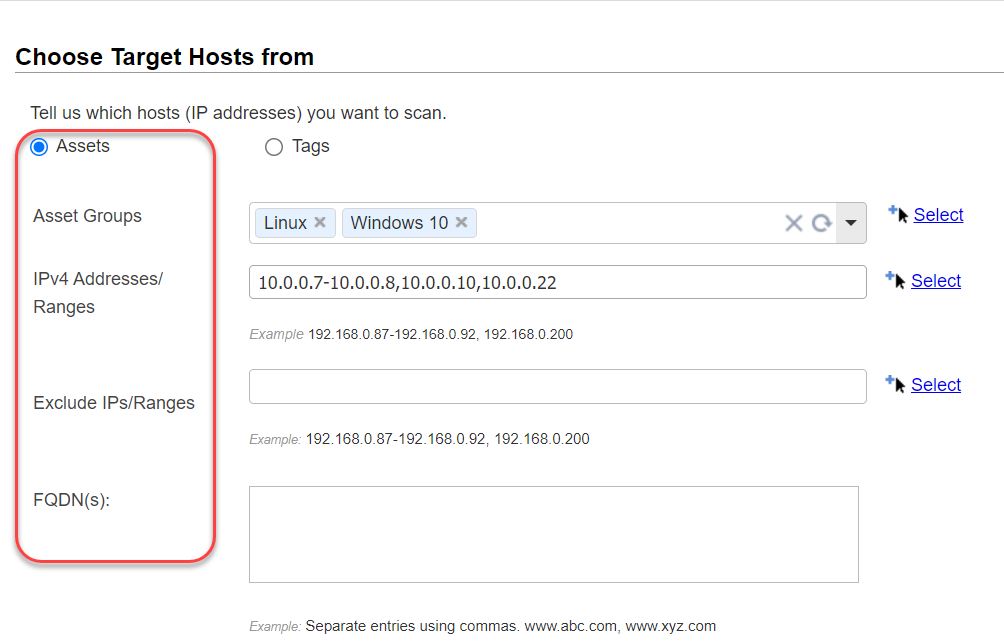
Choose Target Hosts from "Tags"
Select the Tags option to specify the scan target using asset tags.
Include hosts - Add tags to this section for the hosts you want to include in the scan target. We'll scan the hosts that match the selected tags. To find a tag in the tag selector, click Add Tag and then begin typing the tag name in the Search field. Click a tag to select it, then click outside the tree to add the selected tags to the scan.
Do not include hosts - Add tags to this section for the hosts you want to exclude from the scan. We won't send any scanning traffic, including ICMP, TCP and UDP probes, to hosts that are excluded.
Any vs. All - Choose All to include hosts that match all of the tags selected. Choose Any to include hosts that match at least one of the tags selected.
Use IP Network Range Tags For Include - This option lets you scan all IPs defined in a tag with the IP address tag rule even if the IPs don't already have the tag assigned to them. We'll apply the tag to each IP that doesn't already have it. Click here for an exampleClick here for an example
Example: Let's say you have a tag called "My Network" with the IP range 172.31.254.0-172.31.254.25. You've scanned IPs 172.31.254.10 and 172.31.254.20 before and so these hosts have the My Network tag assigned. The other IPs in the range do not have the tag. If you select "Use IP Network Range tags", the entire IP range will be scanned and hosts will be tagged. If you don't select it, only the 2 hosts that already have the tag will be scanned.
Use IP Network Range Tags For Exclude - This option lets you exclude the entire IP range(s) defined in tags with the IP address tag rule.
Temporarily add agent addresses - You need to select this option if your scan target includes agents that may have acquired IPs not in your subscription. Without this option, the scan will not execute and will generate an error due to the addresses not being in your subscription. This option temporarily adds the IP addresses of any agents in your target to your subscription for this scan only. This option cannot be used with the External scanner option. Learn more about hosts with agents
(Optional) Select Send notification when this scan is finished if you'd like an email notification with a custom message to be sent to you and others when this scan is finished.
![]()
From - Select the email address that should appear in the From line of the email. You can choose the Support email or your own.
Email To - Tell us who to notify when this scan is finished. You'll do this by selecting distribution groups. Click Add Group. Then, in the window that appears, select a group in the list to see details about the group, and click Add to list to add the group to the notification. Learn more about distribution groups
Subject Line - Enter text that will appear in the Subject line of the email.
Custom Message - Enter a custom message that will appear in the body of the email.
Once you've provided all the scan information, you're ready to launch the scan. Just click Launch and your scan will be started.

Your new scan will appear on the Scans list. You can let the scan run in the background and then return to this list anytime to check the scan status. You'll see status icons next to each scan in the list to indicate if the scan is Running, Finished, Paused, etc. Select any scan row and view the Preview pane below the list for more scan summary details. Learn more about scan status
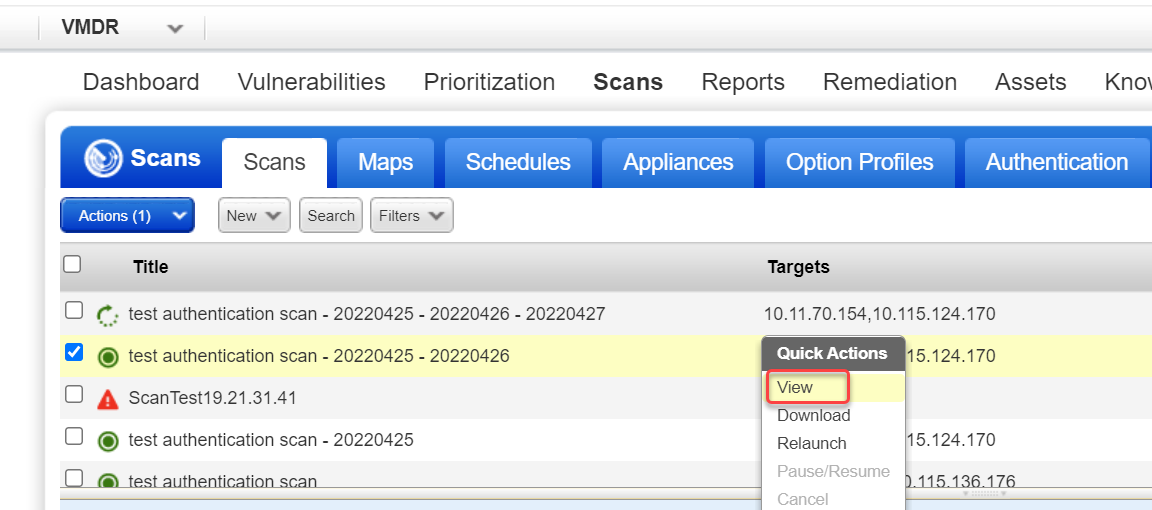
When your scan is Finished, select View from the Quick Actions menu to see the detailed scan results. Download scan results by selecting Download from the Quick Actions menu. Learn more
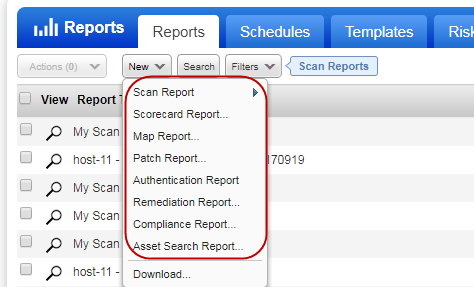
Your processed scan data will be available in your account and you can run reports for different views of your data. We offer several reporting options. Go to Reports > Reports > New to see the options available. Learn more about reporting
Interested in more scanning capabilities?
Schedule Scans | Amazon EC2 Scanning | Cloud Perimeter Scan | CertView Scan | Cloud CertView Scan | IPv6 Scanning | Scan by Hostname | Agentless Tracking | Windows Share Enumeration | Password Brute Forcing | Authoritative Scan Option | Scan OVAL Vulnerabilities | Client Scans (Consultant User)