|
|
Your service level and account settings determine whether you can manage web applications. Your account settings might limit you to some applications or certain permissions (view, create, edit, delete). Learn more
On the Detections List tab (Detections > Detection List) we list all vulnerabilities detected by scans on your web applications. This allows you to review them without running reports. Tip - Use the search and filter options to sort and locate detections you want to take actions on. Learn more
The catalog is a staging area for web applications discovered by scans in the VM application (Web Applications > Catalog). Each catalog entry shows a discovered web application along with tracking information. By adding catalog entries to your subscription you'll make the web applications available for scanning. Learn more
You can create maps using the VM application. As new maps are completed in your account, they will appear on the Maps tab. A map provides full information on your domains (DNS records and topology) and identifies active hosts located in your Internet/Intranet perimeter, depending on the map request. Learn more
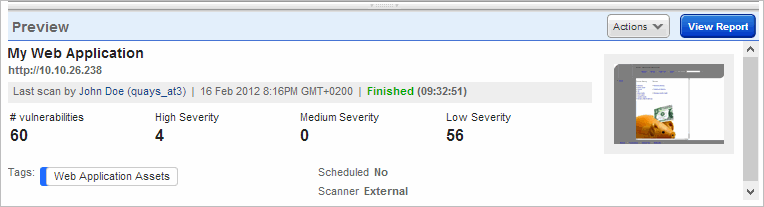
The preview pane appears under the web applications list when you click a row in the Web Applications list. The preview displays the web application name and URL. If the web application has been scanned, you'll see user who launched the scan, the date and status of the most recent scan, and vulnerability detection information. Click any of the detection elements (# vulnerabilities, High Severity, Medium Severity or Low Severity) to display the Detections list filtered for your selection. Show me
Get an up-to-date view of the security of a web application by viewing the sitemap (go to Web Applications, select your web app and then View Sitemap from the Quick Actions menu). You'll get a list of all pages/links scanned with views on the links crawled, vulnerabilities and sensitive content detected. You can drill down to see nested links and explore the security of different parts of your application. Learn more
Option profiles provide the settings for web application scans - crawling, sensitive content detection, vulnerability detection and password brute forcing. When launching or scheduling a scan, you'll need to choose an option profile. If you don't have a WAS option profile in your account, we've provided one called "Initial WAS Options" with the recommended settings for web application scanning. Learn more
Some web applications require authenticated access to the majority of their functionality. Authenticated scanning can be configured for HTML forms like login pages and server-based authentication (HTTP Basic, Digest, NTLM, or SSL client certificates). We also support OAuth2 for Swagger/Open API file authentication. You can either combine form and server authentication or OAuth2 and server authentication for an authenticated scan. Learn more
Yes. You can use Qualys Browser Recorder to create a Selenium script and then record and play back web applications functions during scans. For each web application in your account, you can create scripts to configure authentication and crawling. Learn more
You choose a crawl scope option in your web application settings to determine the scope of scans for that web application. You can limit crawling to the URL hostname, content at or below a URL subdirectory, the URL hostname and a specified sub-domain, or the URL hostname and specified domains. In case of authenticated scan, ensure that you always put the login link as the first link. Learn more
Exclusions lists are configurable at a global level (across all web applications in your subscription) as well as per web application. You can implement customized exclusion lists for your web application and ignore the global settings while creating or editing a web application.
You can use exclusion list to tell us which links to scan and which to ignore for all web applications in your subscription. For a production web application, it's best practice to add pages with certain functionality to exclude list that if executed would have undesirable results, such as possibly sending out too many emails, potentially submitting a "delete all" button, or disabling/deleting accounts.
Exclusion lists are allow lists, exclude lists, POST data exclude list, logout regular expression list and parameter list. Learn more
What if I use a exclude list and a allow list?
What if I use only a exclude list?
You can configure case-sensitive name sorting of your data list. Go to Configuration > Global Settings. By default, the Case-Sensitive Name Sorting is enabled. To change the setting, click Edit. You can then toggle and configure the sorting to enable or disable as per your need. Click Save to save your changes. You can sort names of scans, schedules, option profiles, search lists, and so on.
You can tag web applications to organize them according to function, location or any criteria you want. Want to define tags? It's easy - just go to the CyberSecurity Asset Management (CSAM) application.
For example, you might use tags to organize web applications by divisions they belong to. And if there's a tiered structure to those divisions, you can nest the tags in a hierarchy that mirrors that structure. You can also use tags to run web application reports. If you choose a parent tag as the report target, the report will include all web applications matching that tag and its child tags.
Tell me about user access to tags
The Find option in the Quick Actions menu gives you four options. You can find all scans, schedules, detections or Burp issues for a selected web application. Just mouse over the web application, select Find from the menu and choose your option. We'll show you your chosen list filtered for the web application you selected.
Purging a web application removes all the web application scan data from your subscription. Findings from previously completed scans will not be included in new reports. Note that scan results are also removed from account upon web application purge.
We recommend you run the optional Web Application Security Status Report when purging web applications. (You'll need the Create Report permission to run this report.)
Remove web assets removes the selected web applications from your WAS license. Taking this action has permanent impact to your account. Learn more
Choose "Remove from my subscription" if you want to remove the selected web application(s) from all modules in your subscription. Learn more
We've integrated malware detection into web application scanning. This is an easy way to combine web application scanning and malware detection to ensure that your Internet facing web sites are free from web application vulnerabilities and malware. Web site malware is typically found only on Internet facing web applications. Learn more
Yes, you can launch or schedule a scan from the list. Just hover over a web application and select Scan or Schedule from the menu and then choose Discovery or Vulnerability. Use the wizard to add your settings.
You can easily create a report on one or more web application right from the web applications list. Simply select web application check boxes and choose View Report from the Actions menu. We'll take you directly to the Reports section and display your report.
Yes, many settings including option profile, authentication records, crawl settings and more can be edited for multiple web applications. Just select any number of web applications from the list, choose Edit from the Actions menu and use the wizard to edit your settings.
Is your web application protected by WAF? If yes, you can enable the ScanTrust feature to enhance scanning and reporting capabilities. Learn more
Do you have WAF in your account? If yes, you can use WAF to protect against vulnerabilities by installing virtual patches. Go to WAS > Detections > Detection List. Identify the detection you want to patch (vulnerability or sensitive content) and choose Install Patch from the Quick Actions menu. Review the detection details and feel free to update or remove rule conditions. Then click OK. We'll add a virtual patch rule to your firewall.
If your web application uses URL rewrite, you can now tell us the path components that need to be tested by defining the path fuzzing rules. The rules will tell us the path components/parameters that need to be fuzzed and we will prevent multiple crawling of paths that meet the rules. Go to WAS > Web Applications > Create/Edit a web application and define the rules in the Redundant Links section. Learn more
The Advanced Options allows you to configure Default DNS Override and Form Training.
DNS Override: By default we'll use the DNS for the web application URL to crawl the web app and perform scanning. If you select a DNS override record, we'll use the mappings in your record instead. Learn more
Form Training: Define a action URI, specific form field and its value to be substituted during crawling and fuzzing. This feature allows you to override a specific field's value in any given form. Global field names and associated values can be specified as well, independent of any form. Learn more
The Open in Browser quick action allows you to directly open the web application in a new tab of the same browser window.
We support security test of REST APIs exported using Postman or Swagger tool.
Postman tool, used to test the REST APIs, has the facility to export and share the REST APIs. Postman Collection file is the group of REST APIs. Just upload the Postman Collection exported file in JSON format and we will then scan for vulnerabilities. Show me
Note: We currently only support v2.0.0 and v2.1.0. for Postman Collection. The size of the file you upload should not exceed 5 MB.
Choose this option if you want to scan API endpoints and Swagger files. Swagger tool, used to test the REST APIs, has the facility to export and share the REST APIs. Upload the Swagger/OpenAPI file in JSON or YAML format and we will then scan for vulnerabilities. Show me
For scanning Swagger-based REST APIs, the web application URL should point to the Swagger file host or OpenAPI server URL as per the API definition. It is your responsibility to verify that you have permission to scan APIs that you entered as a scan target.
It is important to ensure you have the correct crawl scope defined for the API based on the Swagger/OpenAPI file host entry. If the domain for the Swagger 2.0 file is same as the domain for the host (the API itself), you can use the crawl scope as the default "Limit at or below URL hostname". If If the domains are not same, modify your crawl scope to "Limit to URL hostname and specified sub-domain" or "Limit to URL hostname and specified domains" as appropriate. Learn more
Note: We currently only support Swagger v2.0 and v3.0. The size of the Swagger/OpenAPI file before compression should not exceed 5 MB.