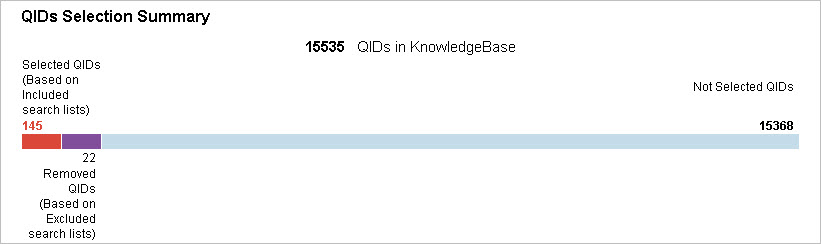
Out of 15535 QIDs in the KnowledgeBase, 145 were included, 22 were excluded and 15368 were not selected for this report.
You can edit any of the scorecard report templates in order to save a personal copy with customized settings.
|
See also Reporting - The Basics |
Go to VM/VMDR > Reports > New > Scorecard Report, select any report in the list and click the Edit link (below the list). Make changes to the Filter and Display settings. Then use the "Save As" option to save your report with a new name. Note that you cannot overwrite the settings in the service provided scorecard reports.
Asset tagging gives you flexibility with managing assets for all of the network assets that you are monitoring for security and compliance. You can select asset tags to include in your report instead of selecting IP addresses and/or asset groups. Learn more
Managers can select a business unit for the report source. Asset groups in the business unit are included in the report automatically. If you also specify business info tags, then asset groups in the business unit with the specified tags are included in the report. Learn moreLearn more
The asset groups included depend on your business unit selection:
If you choose the "Unassigned" business unit, then asset groups created by users in the Unassigned business unit are included in the report.
If you choose a user-defined business unit, then asset groups assigned to the business unit by Managers are included in the report. Asset groups created by users in the business unit (Unit Managers, Scanners and Readers) are not included in the report.
Are you an Express Lite user? If yes, the business unit option is not available.
These tags refer to the text fields on the Business Info tab when creating/editing asset groups. You can enter business information into these fields to essentially tag the asset group for a particular division, business function or location. If you've assigned tags to your asset groups, your tags appear in the Division, Function and Location drop-down menus. (Note that these menus are disabled when business info tags are not in use.)
Are you an Express Lite user? If yes, the business info tag options are not available.
If you select more than one tag, only asset groups with all specified tags are included in the report. For example, if you select the Location "Tokyo" and the Function "On-line Banking", then the report will include asset groups tagged with both the location and function.
Yes, you can filter vulnerabilities (QIDs) by severity or by search lists. These options appear in the Filter section of the template. You may also want to choose the option "Show Included & Excluded Search List summary" in the Display section of the template to show the list of included QIDs in your report based on your search list selection.
Non-running kernelsNon-running kernels
By default we report all vulnerabilities on all Linux kernels (the running kernel and non-running kernels). Choose the display option to add a new section to your report listing vulnerabilities on non-running kernels or choose the exclude option to filter them out. Learn more
Pre-defined QID filtersPre-defined QID filters
Select filters to exclude certain vulnerabilities from your reports like vulnerabilities found on non-running ports/services and vulnerabilities that can’t be exploited because of a host configuration. These filters apply to certain QIDs only. Learn more
Yes, select the confirmed and/or potential severity levels you want to include in the report. For example, you can include only confirmed vulnerabilities with severity 3 and above. All other vulnerabilities will be filtered out. Note - When you filter QIDs by severity you cannot filter QIDs by search list at the same time. If you add search lists to the template, your severity selection will be removed/deselected. Tip - Check out the other scorecard report templates to see similar filter options.
If you've added search lists for a custom QID selection, you can select this option to display these additional sections in your report: QIDs Selection Summary and Search List Summary. Show me an exampleShow me an example
Out of 15535 QIDs in the KnowledgeBase, 145 were included, 22 were excluded and 15368 were not selected for this report.

The Patch Scorecard Report identifies hosts with missing patches and software based on the most current host/vulnerability data.
Patch Release QIDs - Select up to 10 QIDs to find hosts that are missing patches (when a patch is available for the QID). Learn moreLearn more
For example, you may specify QID 90108 "Multiple Microsoft Windows Vulnerabilities (MS04-011)" which has an update that was released in Microsoft Security Bulletin MS04-011. When the QID is detected on a host, the host does not have the update installed and the host will be listed in the Results section of the report.
Missing Software QIDs - Select 1 or 2 QIDs that correspond to software that you want to make sure is installed on hosts. Information on installed software is typically provided through information gathered checks. There are information gathered checks that identify when antivirus software is detected, when an SMS client is installed, when a personal firewall is installed, and so on. Learn moreLearn more
For example, your organization might require that hosts have Symantec Norton Anti-Virus software installed. To find hosts that are missing this software, include QID 105003 "Symantec Norton Anti-Virus Corporate Edition Detected" in your report. When the QID is not detected on a host, the host is missing the software and the host will be listed in the Results section of the report.
(Applicable to the Vulnerability Scorecard Report only) Yes it's easy and your report will show you whether your remediation efforts are meeting the goals set by your own security policy. Select Business Risk Goal and use the slider to set the maximum acceptable risk from 0 to 100 percent of vulnerable hosts. Your setting will apply to all target assets. When set at 50%, the target group/tag passes if 50% or fewer of the hosts are vulnerable. The group/tag fails if more than 50% are vulnerable. By creating multiple templates with different goals you can address different business requirements.
(Applicable to the Vulnerability Scorecard Report only) When "Vulnerability Status" is selected on the Display tab, then we'll show vulnerability counts in your report for each status level, including Fixed. By default, the Fixed count includes all vulnerabilities fixed over time, since the start of your subscription. If you want to see the number of vulnerabilities fixed say within the past month or quarter or after a particular date, then select a timeframe on the Filter tab.
(Applicable to the Vulnerability Scorecard Report only) Select the Include Vulnerability Ignore Status option, when "Vulnerability Status" is selected on the Display tab of the vulnerability scorecard report template, then we'll show ignored vulnerabilities count when reporting vulnerability counts by status.
(Applicable to the Vulnerability Scorecard Report only) Use this option to filter hosts based on the last scan date for each host. For example, select a timeframe like July 1, 2016 - July 31, 2016 to only include hosts that were last scanned between those dates. If a host was last scanned before July 1 or after July 31 then it will not be included.
Please note:
When you choose one of the "Previous" options we'll start with the current date and count backwards to get the date range.
Previous Week = the last week starting from Sunday to Saturday
Previous Month = the last month starting from 1st to end of the month
Previous Quarter= the last quarter (3 complete months of the quarter starting
from 1st to end of each month)
Previous Year = the last year starting from January to December
(Applicable to the Vulnerability Scorecard Report only) Select this option to ensure that only vulnerability information gathered in the timeframe that you've specified is included in the report. If you do not select this option, vulnerability information for hosts that were last scanned prior to the report timeframe may be included. For example, let's say you want to create a report analyzing data for the past 4 weeks. Host A was scanned 5 weeks ago, and has not been scanned since then because it was firewalled and unreachable. By selecting this option you'll exclude Host A from the report and only analyze vulnerability information detected in the past 4 weeks. By clearing this option you'll include Host A in your report with the last known vulnerability information from 5 weeks ago.
This is a spot where you can add required information like a disclosure statement or data classification (e.g. Public, Confidential). The text you enter will appear in all reports generated from this template, except reports in XML and CSV formats.