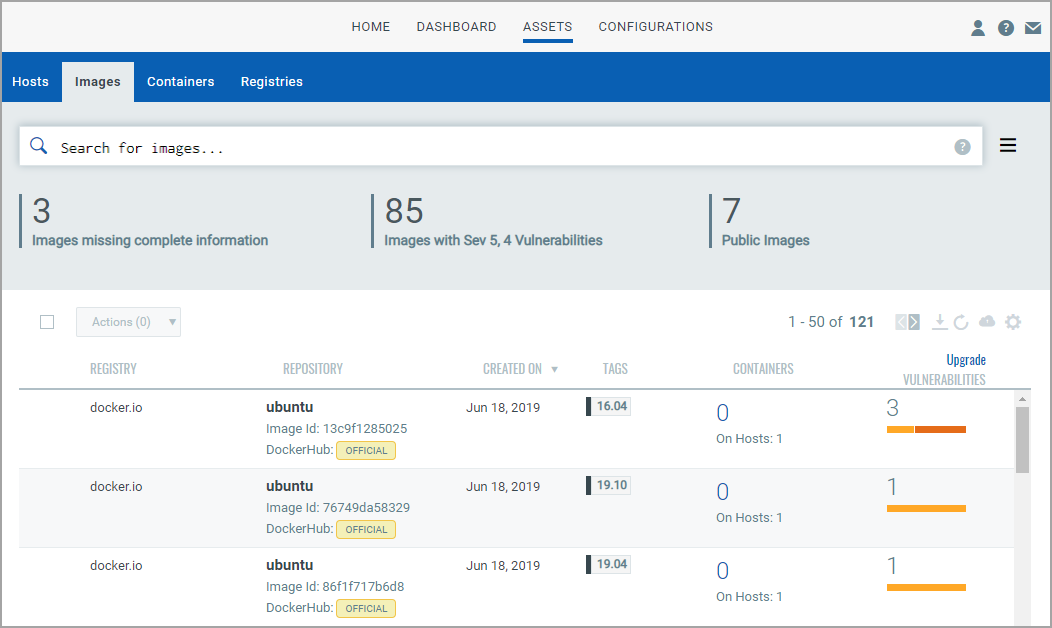
Vulnerability scanning of Registries
Vulnerability scanning of: Docker Images | Docker Containers | Docker Hosts | Registry
Registry images are scanned to check the presence of any vulnerabilities by the Qualys container sensor. You can scan public and private registries for vulnerable images.
Which registries are supported?
See Concepts and Terminologies for a list of public and private registries you can scan.
How do I add a registry to scan?
See Adding a New Registry to Scan for the steps.
Where will I see vulnerable images?
Once you connect to the registry, Container Security pulls the inventory data and performs scans on repositories and images within the registries.
Vulnerable images are listed on the Assets > Images tab. To get the total count of vulnerable images in a registry, go to Assets > Registries, and click View Details in the Quick Actions Menu of a registry.