Concepts and Terminologies in Container Security
Docker Image
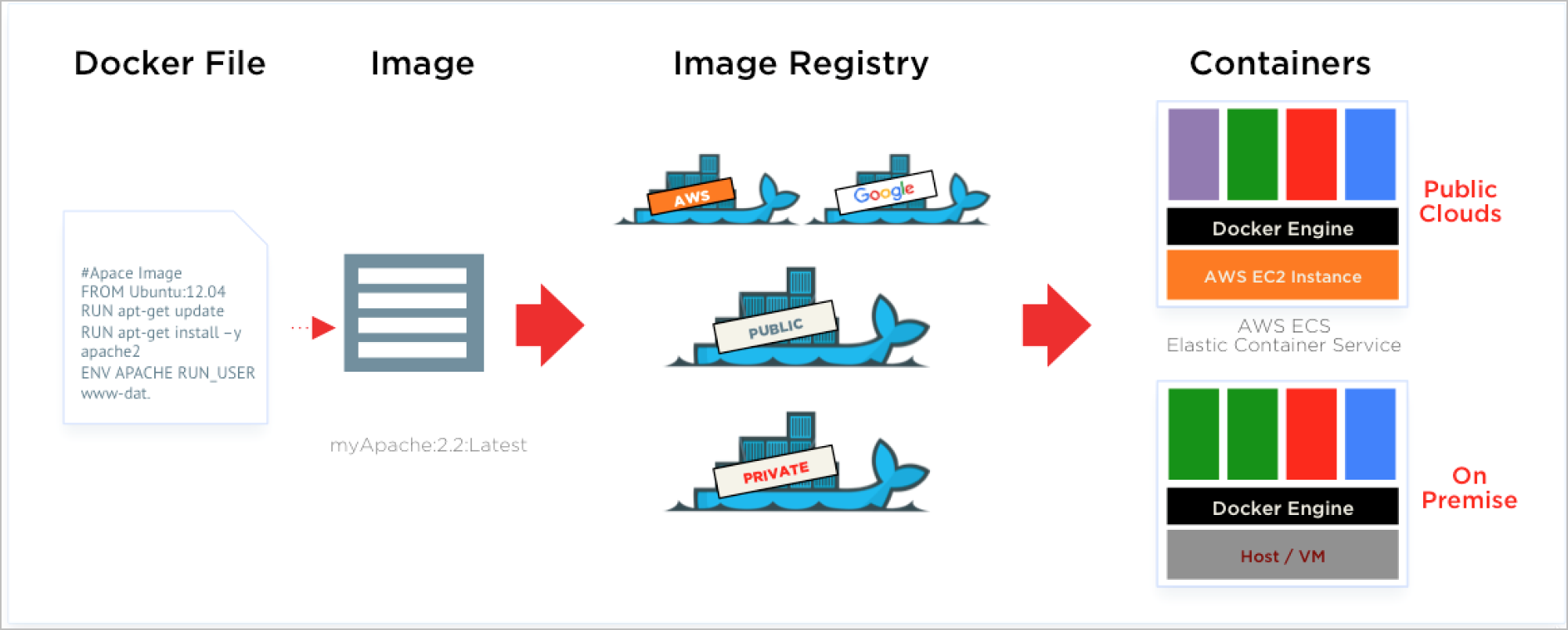
A Docker image is a read-only template. For example, an image could contain an Ubuntu operating system with Apache and your web application installed. Images are used to create Docker containers. Docker provides a simple way to build new images or update existing images, or you can download Docker images that other people have already created. Docker images are the build component of Docker.
An image is a static specification what the container should be in runtime, including the application code inside the container and runtime configuration settings. Docker images contain read-only layers, which means once an image is created it is never modified.
Image is tracked within Qualys Container Security module using Image Id and also a unique identifier generated by Qualys called Image UUID.
Docker Registry
Docker registries hold images. These are public or private stores from which you upload or download images. The public Docker registry is provided with the Docker Hub, Quay.Io or from cloud providers like AWS ECR, Azure Container Registry or Google Cloud Registry. It serves a huge collection of existing images for your use. These can be images you create yourself or you can use images that others have previously created. Docker registries are the distribution component of Docker.
We support scanning the following registries:
Public registries: Docker Hub, AWS ECR, Google Cloud Registry (GCR), Google Artifact Registry, Azure Container Registry (ACR)
Private registries: v2-private registry
- Docker Private Registry: insecure (http), secure (auth + https)
- Docker Trusted Registry
- Harbor
- JFrog Artifactory Private
- Mirantis Secure Registry (MSR) 2.9.4+
- OpenShift Container Registry (OCR)
- RedHat Quay
- Sonatype Nexus
Note: Using http requires customers to manually configure their docker-engine for the registry. Qualys does not recommend using http and it’s intended more for testing in dev environments.
For details on the sensor versions supported for each registry type and interoperability with 3rd party solutions, refer to the Qualys Container Security Interoperability Matrix.
For instrumentation support, see Container Runtime Security.
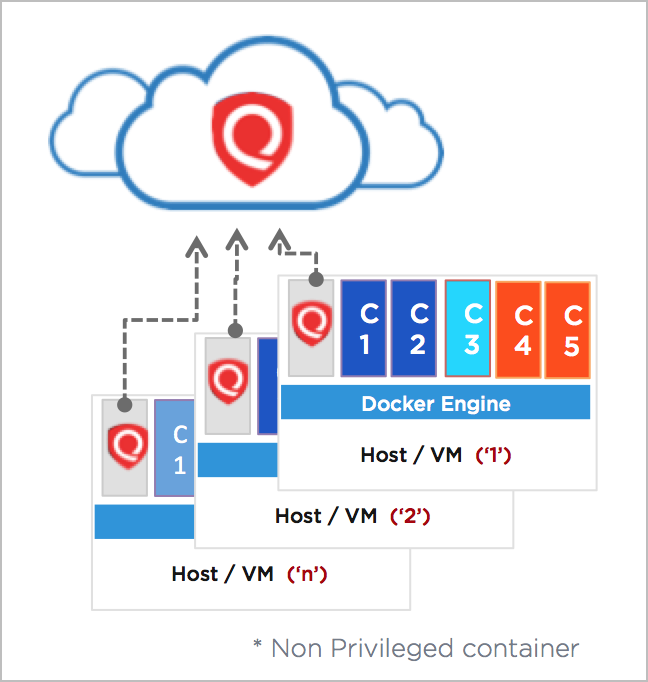
Docker Containers
Docker containers are similar to a directory. A Docker container holds everything that is needed for an application to run. Each container is created from a Docker image. Docker containers can be run, started, stopped, moved, and deleted. Each container is an isolated and secure application platform. Docker containers are the run component of Docker.
A running Docker container is an instantiation of an image. Containers derived from the same image are identical to each other in terms of their application code and runtime dependencies. But unlike images that are read-only, each running container includes a writable layer (a.k.a. the container layer) on top of the read-only content. Runtime changes, including any writes and updates to data and files, are saved in the container layer only. Thus multiple concurrent running containers that share the same underlying image may have different container layers.
Containers are tracked within Qualys Container Security module using Container Id and also a unique identifier generated by Qualys called Container UUID.
Docker Host
Hosts or servers running on top of ContainerD, CRI-O and Docker Daemon, and hosting containers and images. Qualys tracks them as Host Assets, collects the metadata including IP address, DNS and other attributes of the Host. A host in Qualys is identified by a unique identifier Host UUID. The UUID is also stored in a marker file under /usr/local/qualys directory by the Agent or a scan with authentication via a Scanner Appliance.