Vulnerability scanning of Docker Images
Vulnerability scanning of: Docker Images | Docker Containers | Docker Hosts | Registry
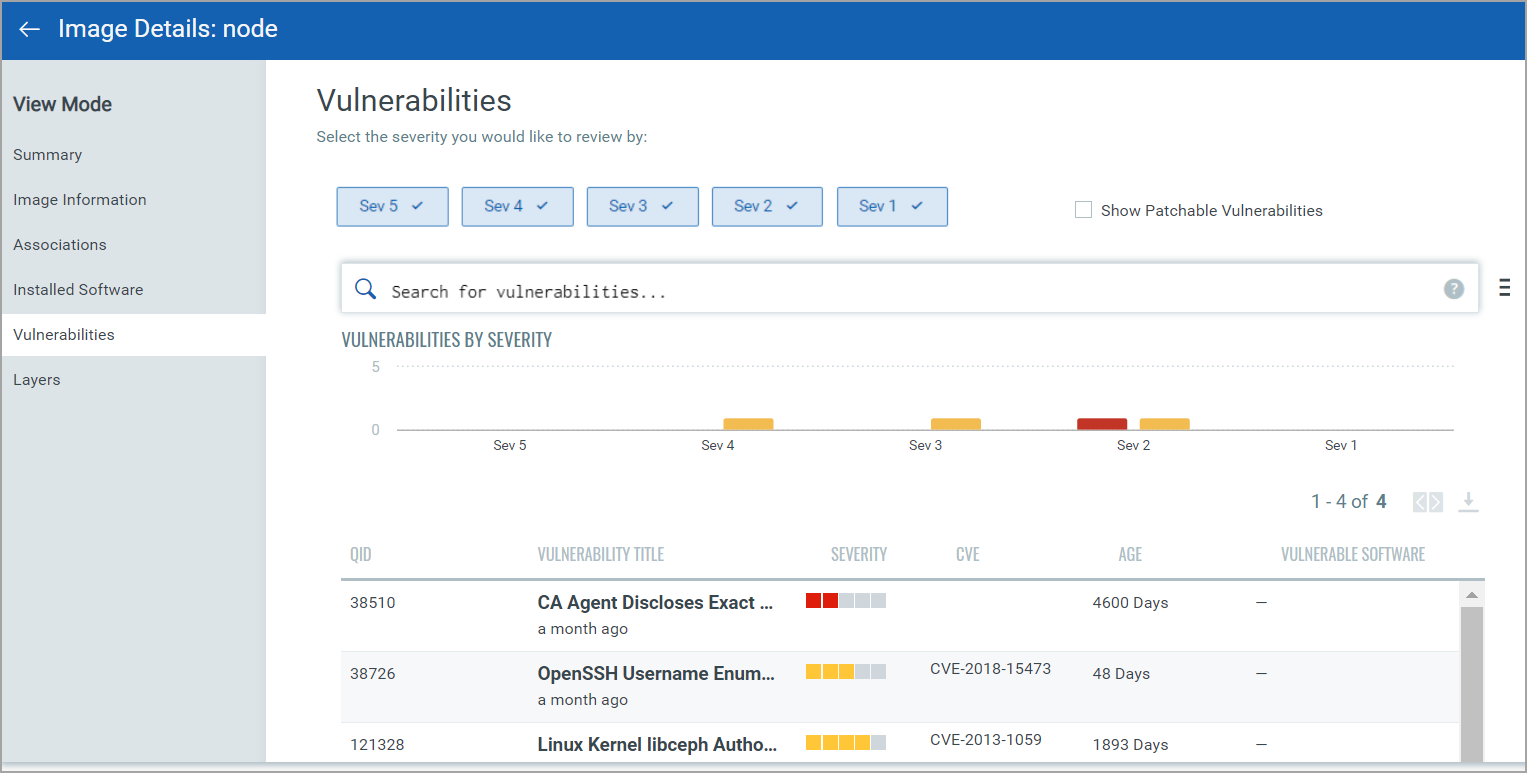
The docker images are scanned to check the presence of any vulnerabilities by the Qualys container sensor. The vulnerabilities panel in Image Details provides a list of vulnerabilities with Severity along with their QIDs. Select Show Patchable Vulnerabilities to view vulnerabilities with available patches.
Docker Images are found distributed across the environment from developer laptops, build systems, Image Registry to being cached on the docker hosts running Containers. To scan for vulnerabilities you would need the Container Sensor deployed on the host asset.
To get an inventory of the images and scan them for vulnerabilities, deploy the container sensor on the host. Refer to Installing Sensors for the install instructions and system requirements.
On the local host or laptops
To get an inventory of the images and scan them for vulnerabilities, deploy the container sensor on the local host. Refer to Installing Sensors for the install instructions and system requirements
To deploy the Sensor on the Mac laptops, there are additional install steps. See Installing the sensor on a MAC.
Upon Installation the sensor automatically detects the images, and provides inventory and vulnerability scans of the image.
In the CI/CD pipeline
Doing a complete check of vulnerabilities in an image during the build time ensures a lot cleaner operating environment. Qualys Container Security provides a plugin for Jenkins and Bamboo to get the vulnerability analysis of images in the build environment. (Learn more how to configure and use the plugin - See the Container Security User Guide on www.qualys.com) If you are using other tools you can use the REST APIs available to perform vulnerability analysis on the images.
To start, deploy the Container Sensor on the Build host where the images are being created. The sensor upon install would automatically trigger a vulnerability analysis of the new images found. Use the API or the plug-in to look for vulnerabilities in the Images. If you are in Jenkins or Bamboo environment, the plug-in would provide detail list of the vulnerabilities and its details directly within the plug-in, you could optionally access your Qualys subscription to view the full report.
In the Registry
Currently, the Qualys Container Sensor doesn’t automatically poll or pull images to do an analysis. Rather you would be needed to deploy the sensor on the host that is configured to pull images from the registry. Either manually or via a cron pull the new images to the host. The sensor does an automatic analysis as soon as it finds a new image. Use the APIs or the Qualys portal to query for the vulnerabilities identified.