View Asset Details
The Assets section lists the Images and Containers discovered along with their metadata information like ports, networks, services, users, installed software, etc. The assets are listed along with their associations like associated containers and hosts for an image, other containers from the same parent image. Users can search for images and containers based on their attributes.
Jump to a section below to learn more:
Hosts
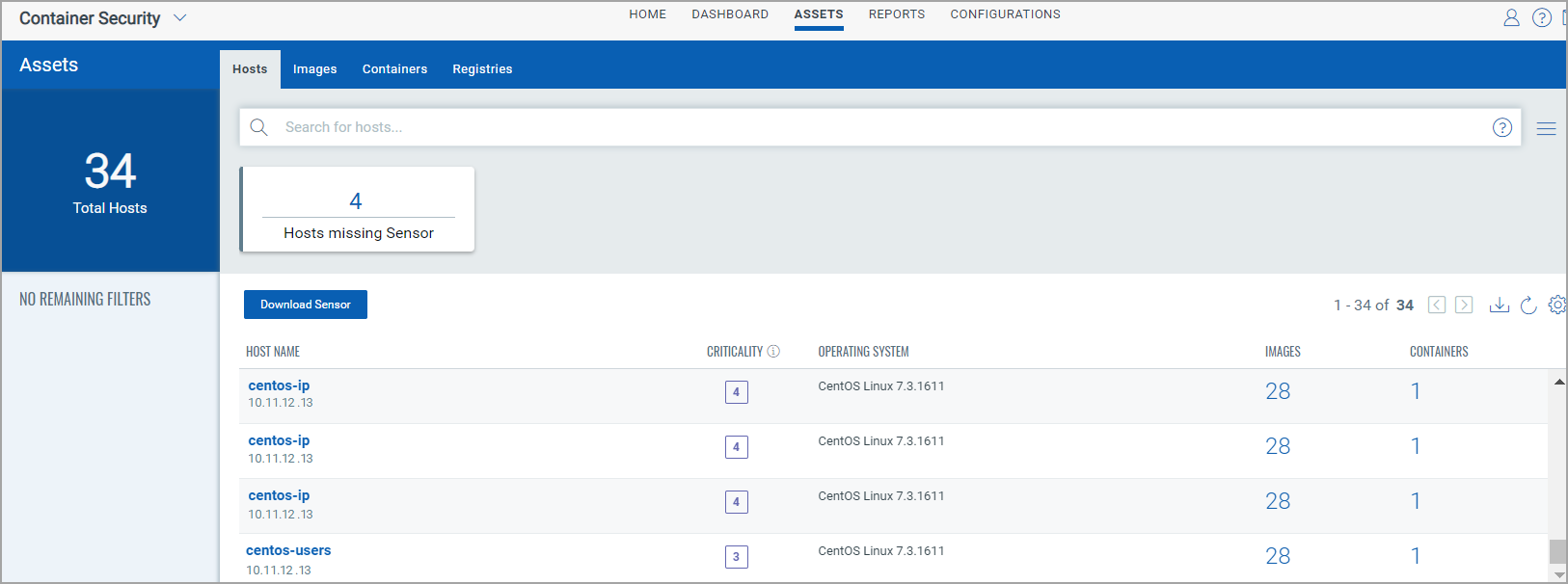
The Assets > Hosts tab shows container hosts discovered, scanned by the Qualys Cloud Agent and/or Qualys Network Scanner. Currently, container hosts discovered, scanned only by the Qualys Container Sensor are not shown in this list. It is recommended you use the Images or Containers tabs for these. Additionally, Qualys Container sensors currently only support hosts and clusters with Linux-based host OSes and Mac OS.
For each host in the list, you'll see the image and container count. Image and container details can be viewed in their respective tabs.
You'll also see the asset criticality score, which represents the criticality of an asset to your business infrastructure. This score is calculated based on multiple tags assigned to the asset with asset criticality scores defined. Learn more about the asset criticality score
View Asset Details
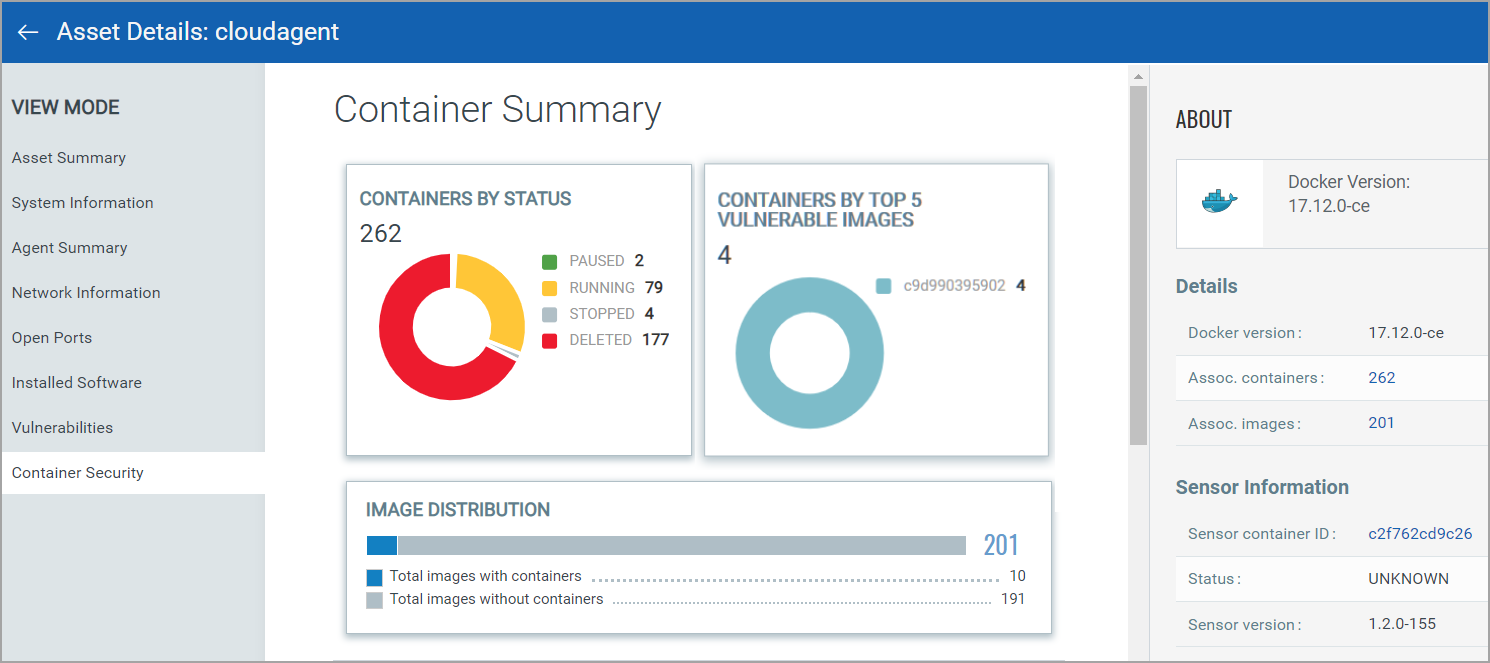
Access the Asset Details page for a host from the Sensor details page.
The Asset Details view displays information about the host on which the sensor is deployed. Besides system, network, and port information, the Asset Details view also displays a list of software installed on the host, vulnerabilities present, certificates, and Threat Protection RTIs (when Qualys TP app is enabled). Container Security panel shows all containers installed on the host, their status, and the images from which the containers are spawned.
Images
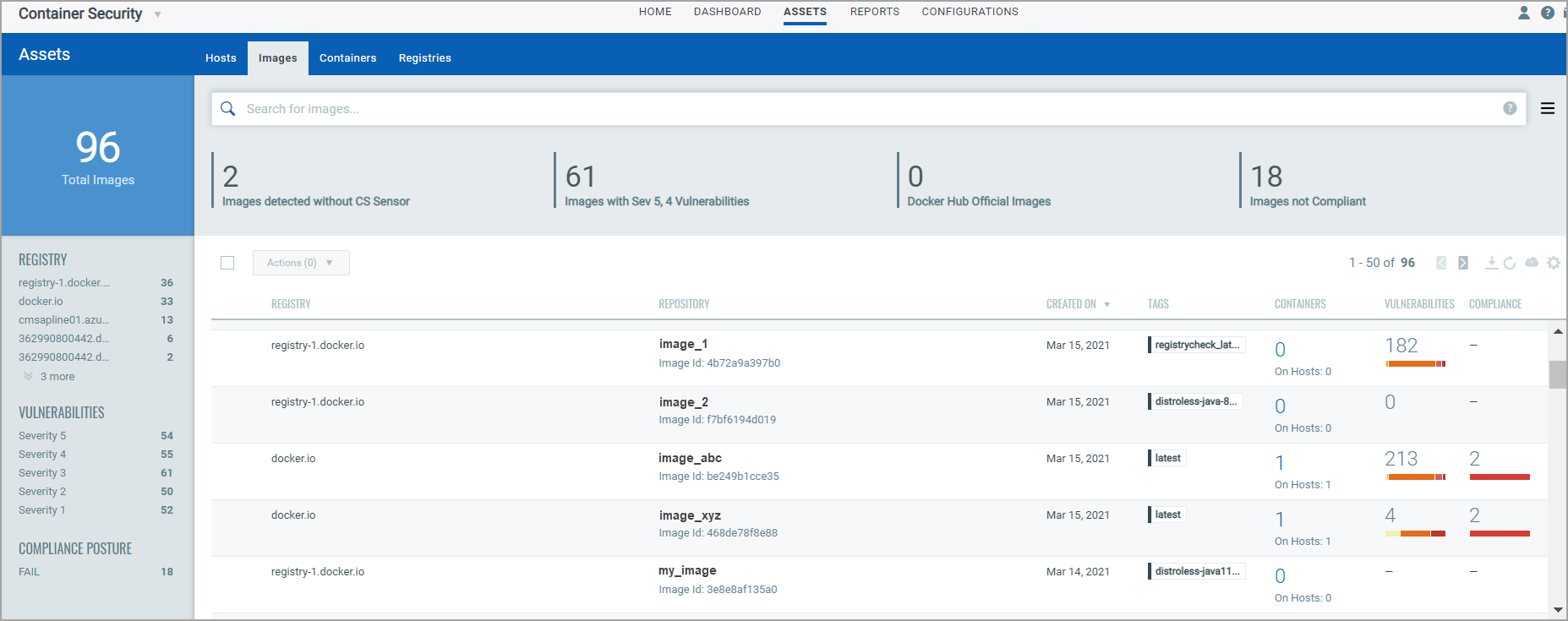
The Assets > Images tab shows the discovered images along with their metadata information.
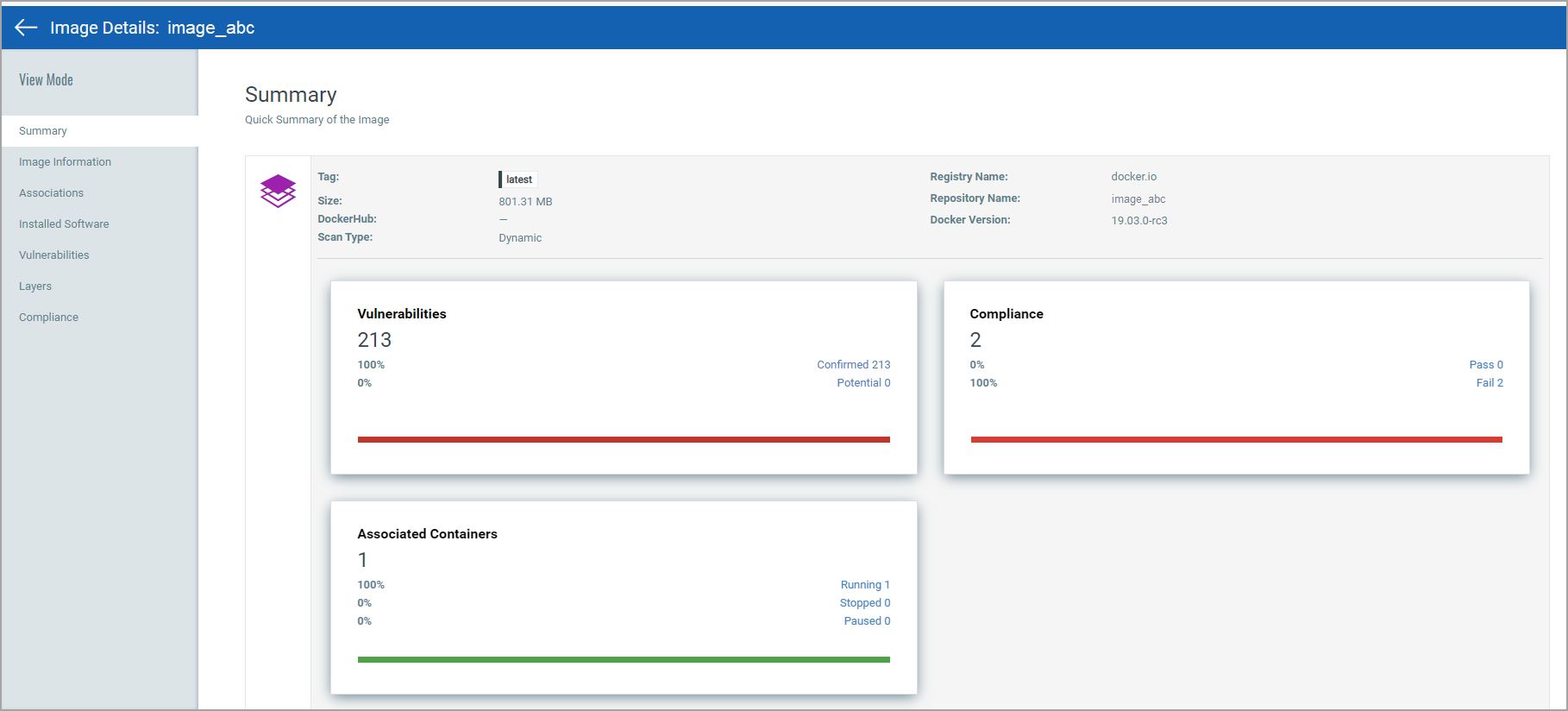
View Image Details
Select View Details from the Quick Actions menu for any image in the list to get comprehensive information about the image. You can view detailed information about the image, its associations with containers, drift containers, and hosts.
- The Installed Software section displays software having vulnerabilities, and for which fixes (patches) are available.
- The Vulnerabilities section provides vulnerability information, such as confirmed and potential vulnerabilities with their severity. For each vulnerability you'll see the vulnerability age (in days). Age is calculated from the point Qualys published the vulnerability.
- The Compliance section provides a list of controls that were scanned with control details (CID, criticality, statement, category, technologies). Learn more
- The Layers section displays a list of layers the image is made of.
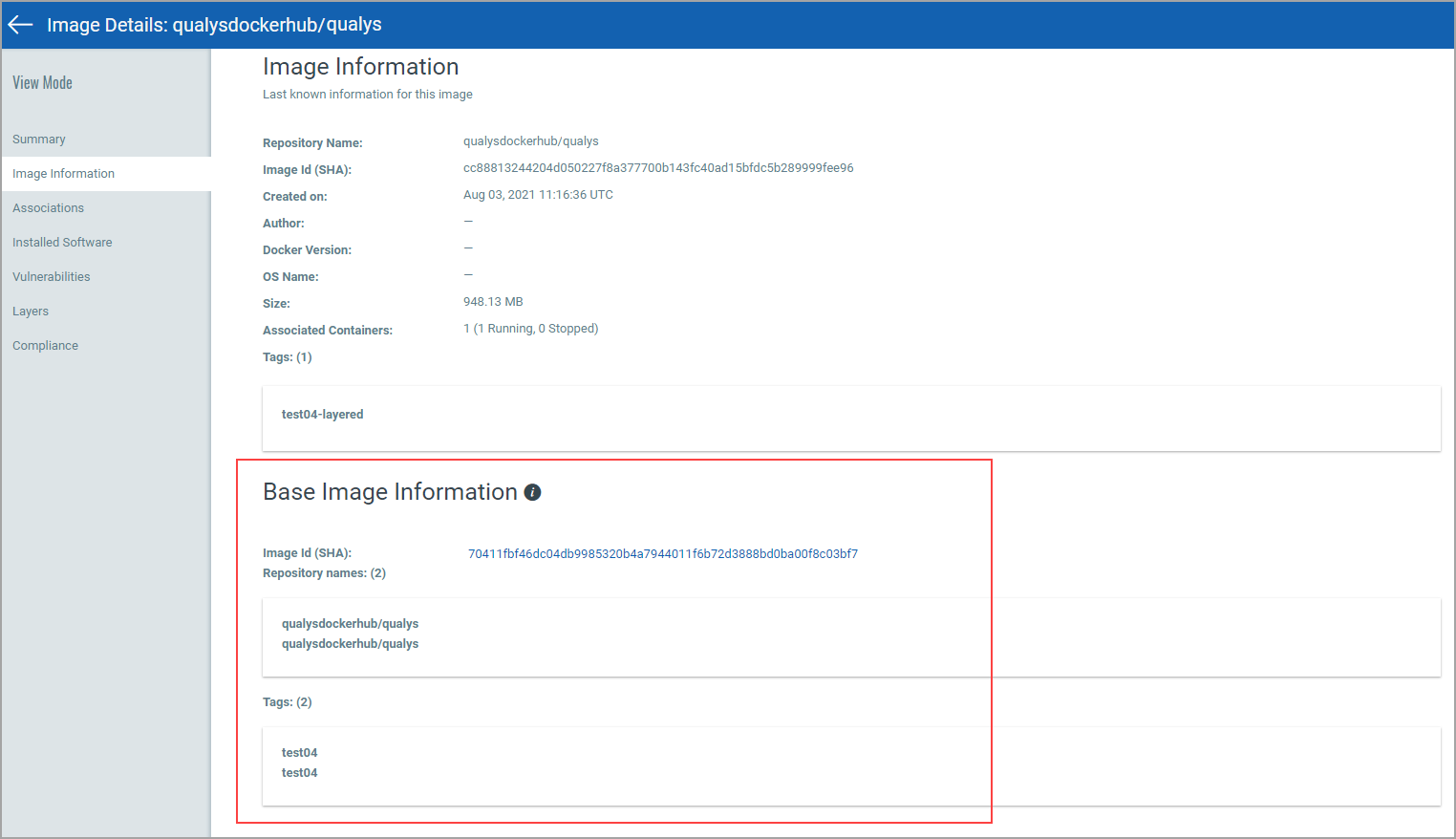
View Base Image Information for Instrumented Images
When viewing details for an instrumented image, you'll see Base Image Information under Image Information. Base image information includes the Image Id (SHA), Repository name(s) and Tags for the base image that was used to instrument the selected image. Click the Image Id (SHA) value in the Base Image Information section to view the image details for the base image. Note - If the base image is no longer in your list of images, then this value will not appear as a hyperlink and you will not be able to view any additional information for the base image.
Tip - To quickly find instrumented images on your Images list, use the following search query:
source:INSTRUMENTATION
Containers
The Assets > Containers tab shows the discovered containers along with their metadata information.
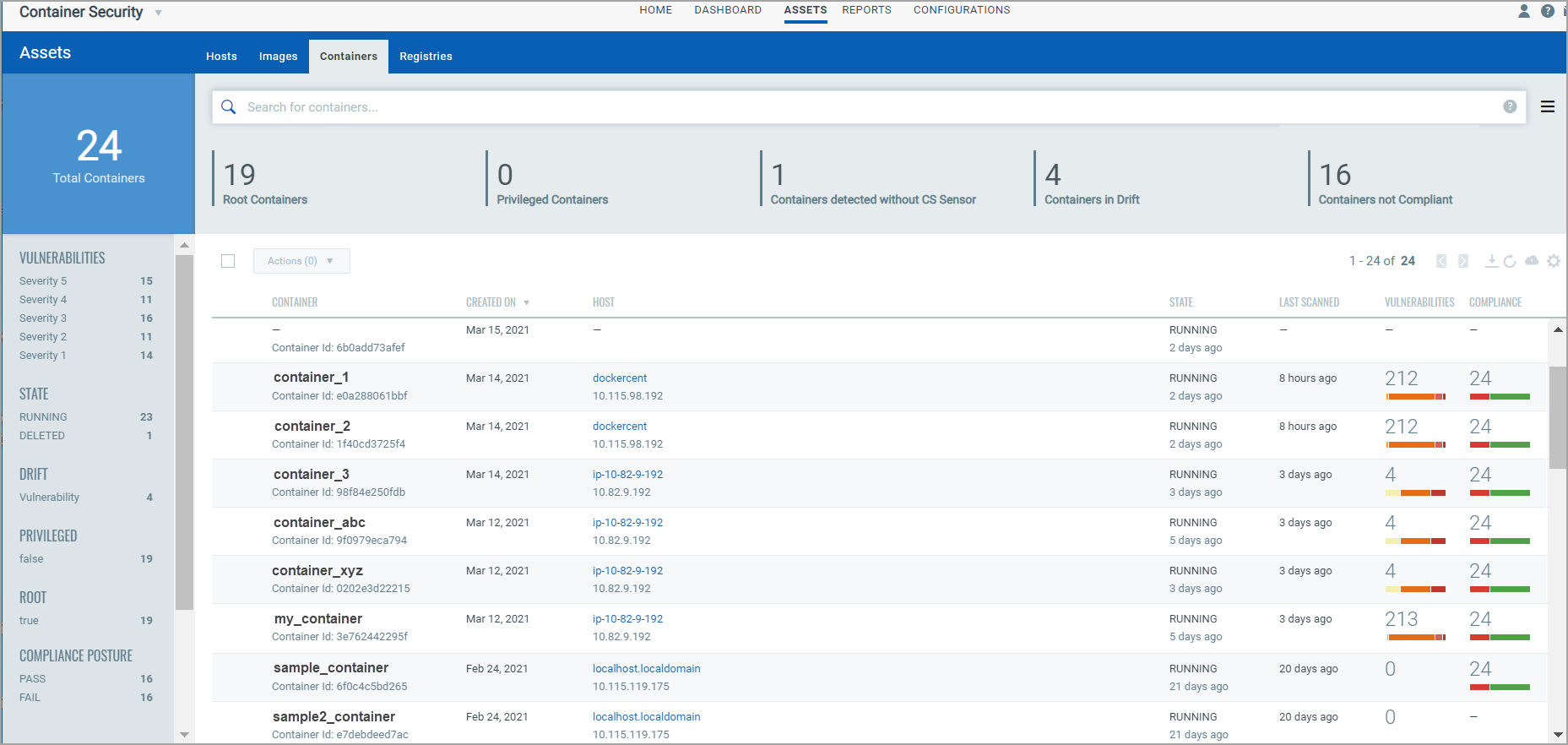
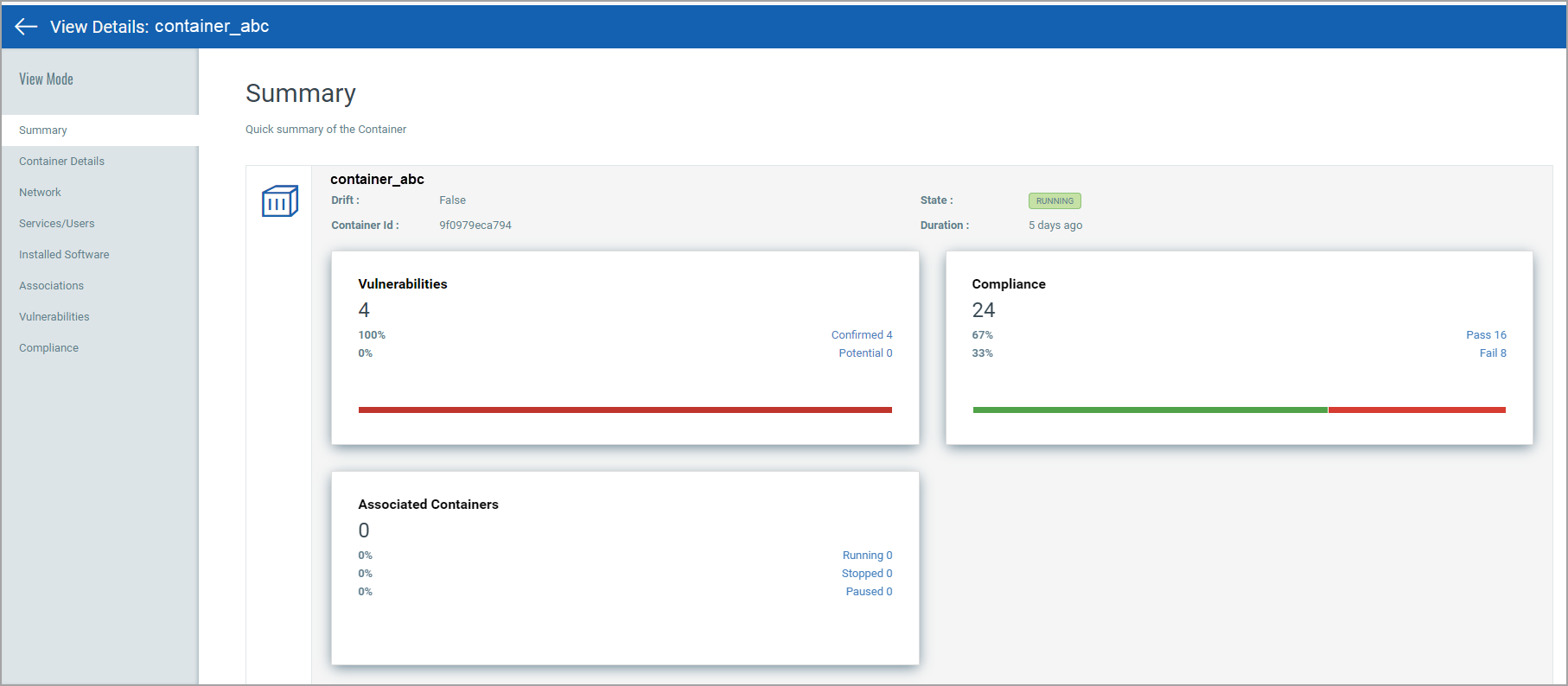
View Container Details
Select View Details from the Quick Actions menu for any container in the list to get comprehensive information about the container. You'll get detailed information about the container, its associations with an image, drift containers, and hosts.
- Container “State” is updated based on the docker events (exec_start, kill, destroy, stop) that Qualys Sensor reports to Qualys Cloud Platform.
- The Services/Users section displays the list of services available in the container and users associated with the container.
- You'll see Kubernetes Metadata in Container Details, including Kubernetes attributes, resources and labels. See Kubernetes Metadata to learn more.
- The Installed Software section displays software having vulnerabilities, and for which fixes (patches) are available.
- The Vulnerabilities section provides vulnerability information, such as confirmed and potential vulnerabilities with their severity. For each vulnerability you'll see the vulnerability age (in days). Age is calculated from the point Qualys published the vulnerability.
- The Compliance section provides a list of controls that were scanned with control details (CID, criticality, statement, category, technologies). Learn more
Registries
The Assets > Registries tab shows the registries in your account. See Adding a new registry to scan to learn how to add and scan registries.
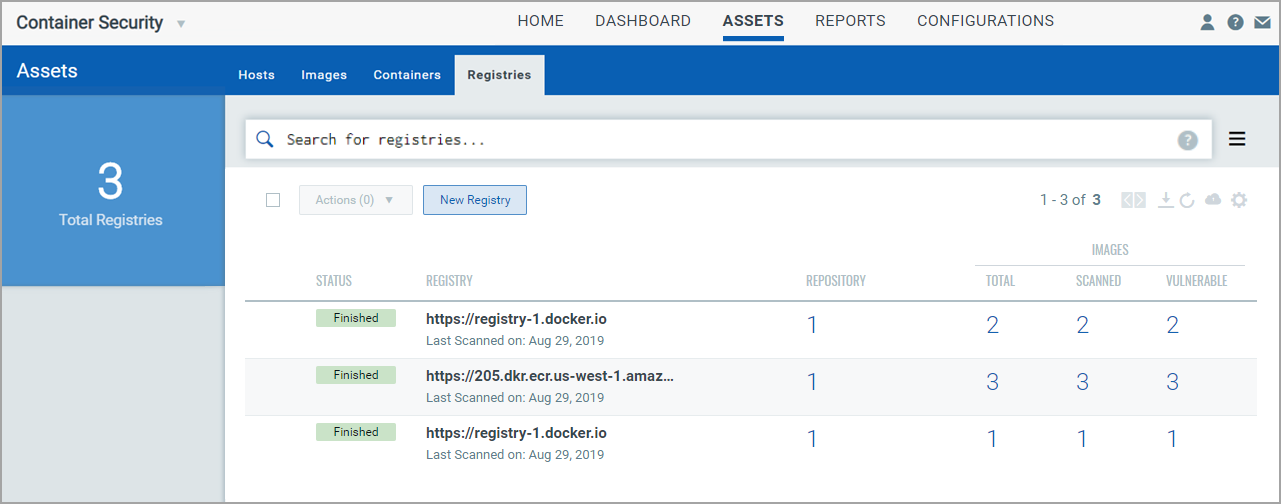
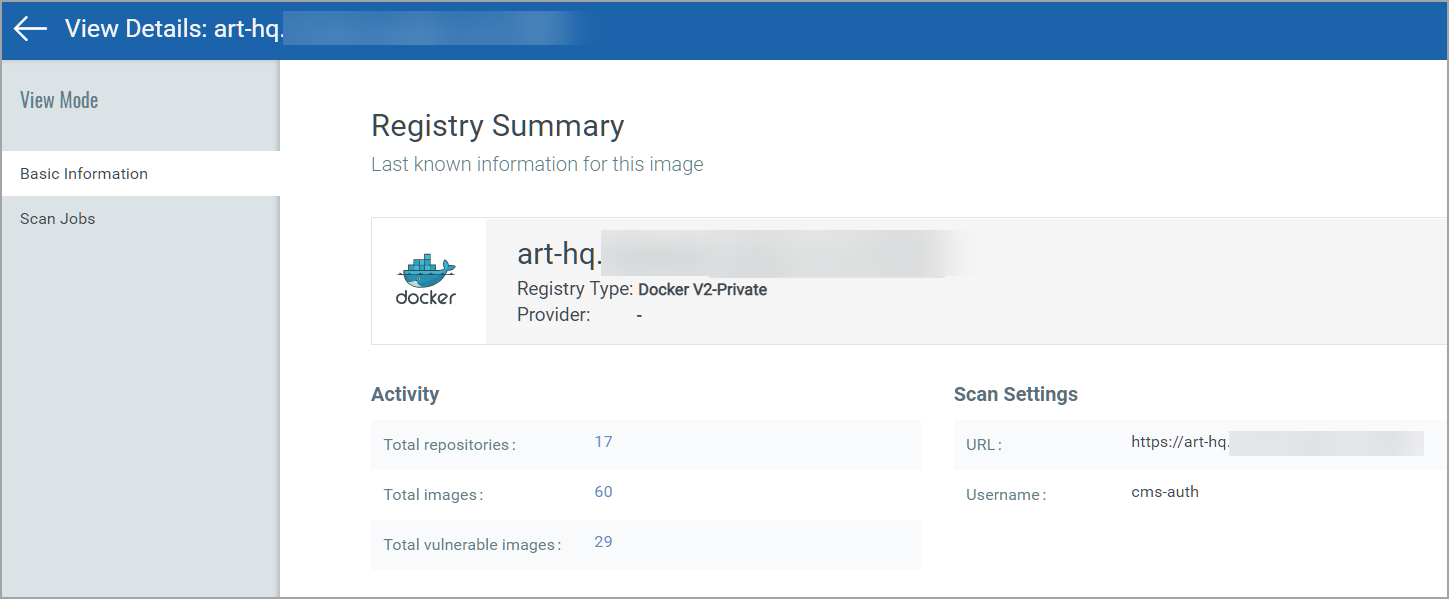
View Registry Details
Select View Details from the Quick Actions menu for any registry in the list to get comprehensive information about the registry. You can view detailed information about the registry: number of repositories, total number of images and number of vulnerable images within that registry. The Scan Jobs panel lists the On Demand and Automatic Jobs created for that registry. For more information, see Vulnerability scanning of Registries.