The PowerShell default execution policy is as follows:
| Computer | Default Execution Policy | Comments |
Windows Server Computers |
RemoteSigned/Restricted |
RemoteSigned requires that all scripts and configuration files downloaded from the Internet are signed by a trusted publisher. With this execution policy, Qualys Cloud Agents should be able to run signed scripts on server computers. Restricted does not load configuration files or run scripts. |
Windows Desktop Computers |
Restricted |
Does not load configuration files or run scripts. Execution policy has to be changed to allow execution of signed scripts at minimum/allow unrestricted execution of PowerShell scripts. The execution policy can be configured through the Group Policy Object (Set PowerShell Execution Policy with Group Policy | 4sysops). The recommended execution policy to set is AllSigned/RemoteSigned depending on user requirement. |
For more information on various execution policies, refer to About Execution Policies - PowerShell | Microsoft Docs
You can use either a self-signed certificate or obtain a certificate from a certificate authority to sign the PowerShell scripts.
For more information on signing, refer to PowerShell | Microsoft Docs.
After the script is signed, the public key of the certificate has to be installed on the system certificate store on Cloud Agents that need to run the signed scripts.
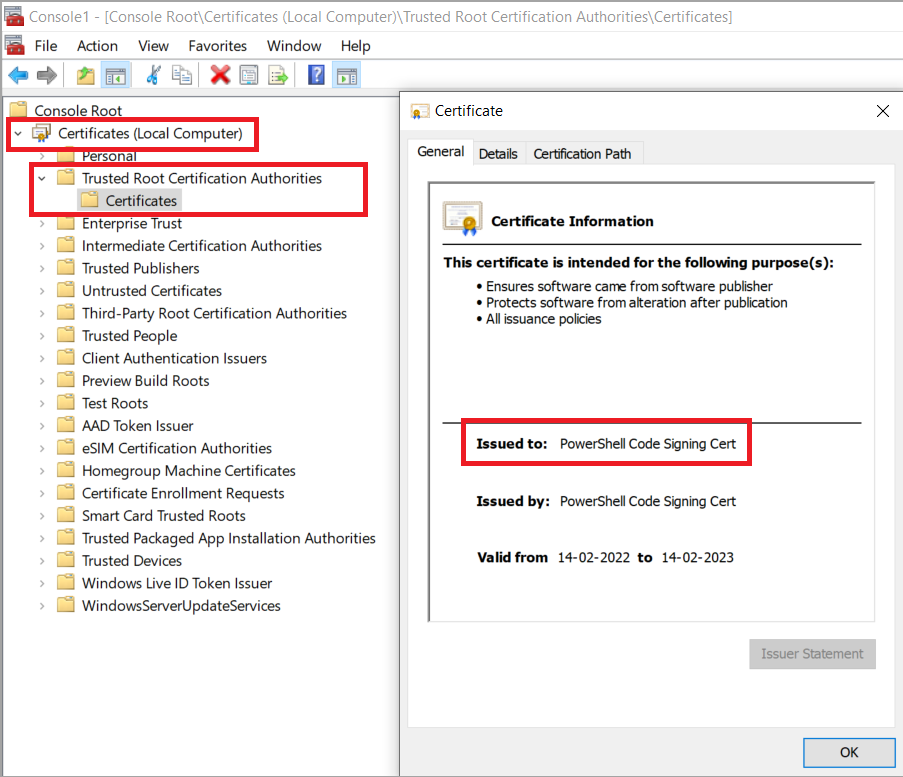
a) To deploy the public key of a self-signed certificate, import the public key certificate to the following System certificate stores:
- Trusted Root Certification Authorities
- Trusted Publishers
b) To deploy the public key obtained from a certificate authority, import the public key certificate to the following System certificate stores:
- Trusted Publishers
Perform the following steps to create and use a self-signed certificate to sign PowerShell scripts by using PowerShell cmdlets:
1) On any computer, create a new self-signed certificate in PowerShell console. Change the ’CN’ string as required (Subject).
$cert = New-SelfSignedCertificate -Subject "PowerShell Code Signing Cert" -CertStoreLocation Cert:\LocalMachine\My -Type CodeSigningCert
Export-Certificate -Cert $cert -FilePath c:\public_certificate.cer
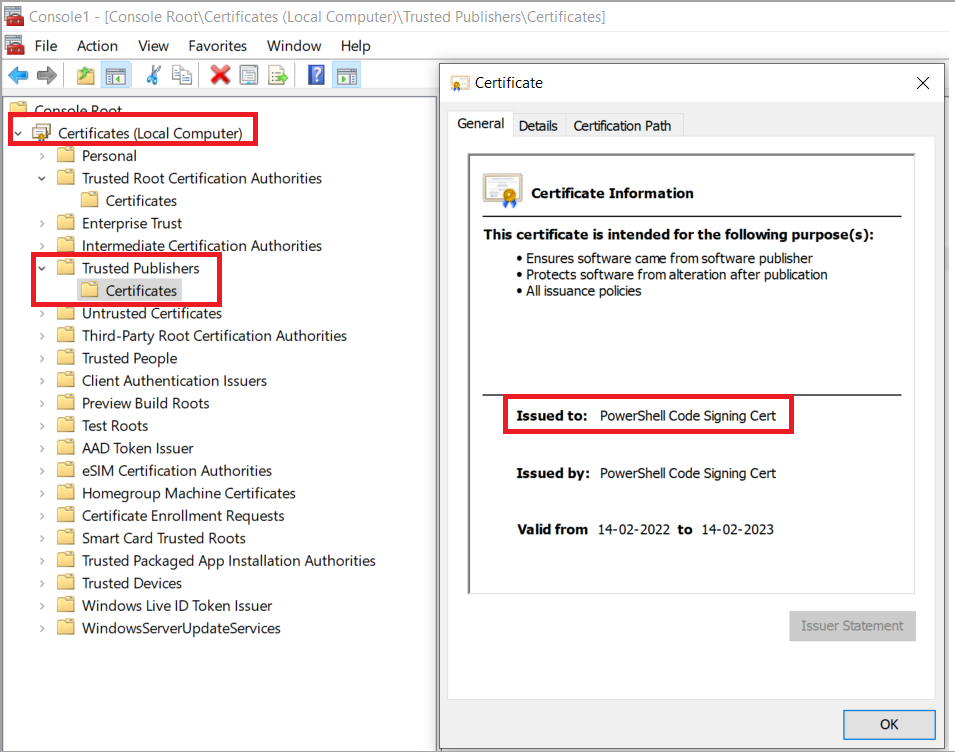
2) Deploy the public key certificate c:\public_certificate.cer from step 1 in the following System certificate stores on the desktop where the script is being signed and all assets where the signed script has to be executed.
a) Trusted Root Certification Authorities

b) Trusted Publishers
3) Sign your PowerShell script using the following cmdlets. ’CN’ string must be same as the ’Subject’ in step 1.
$codeCertificate = Get-ChildItem Cert:\LocalMachine\My | Where-Object {$_.Subject -eq "CN=PowerShell Code Signing Cert"}
# Sign the PowerShell script
# FilePath - Specifies the file path of the PowerShell script to sign, eg. C:\ATA\myscript.ps1.
# Certificate - Specifies the certificate to use when signing the script.
# TimeStampServer - Specifies the trusted timestamp server that adds a timestamp to your script's digital signature. Adding a timestamp ensures that your code will not expire when the signing certificate expires.
Set-AuthenticodeSignature -FilePath "C:\myscript.ps1" -Certificate $codeCertificate -TimeStampServer <http://timestamp.digicert.com>