Here are a few examples of QQL queries for your reference:
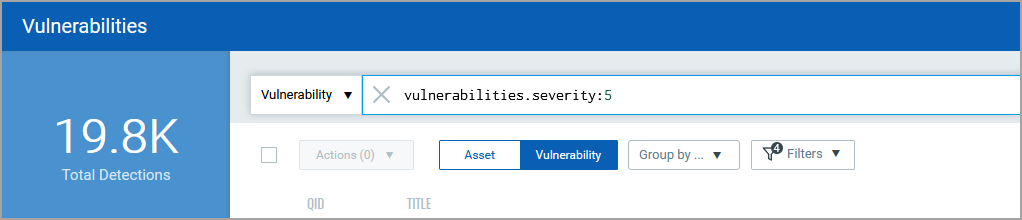
1) Let’s create a query to find out, out of total vulnerability detections, how many vulnerabilities are of severity 5.

Run the query, and note the difference in the total detections in the result.
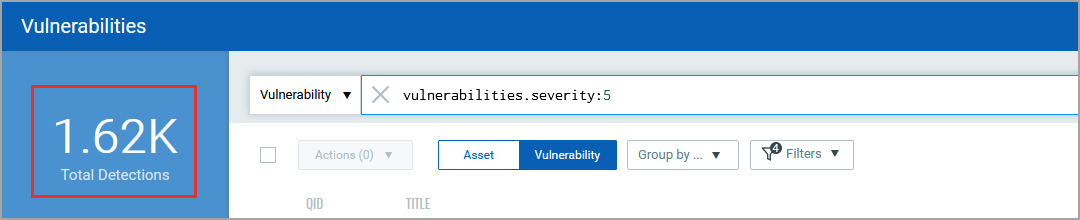
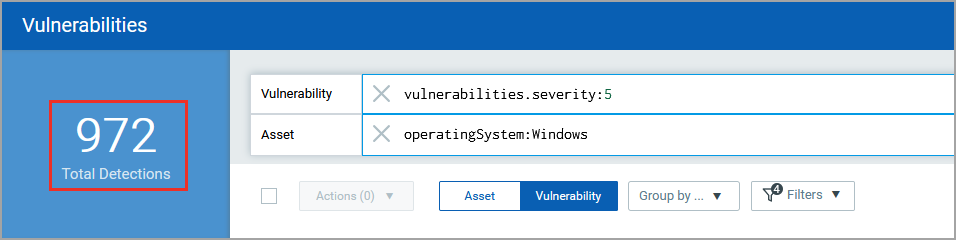
Let’s further narrow down our search and look for severity 5 vulnerabilities detected only on the Windows assets in our environment. Add another query for the Asset data source index, and run the combined query.
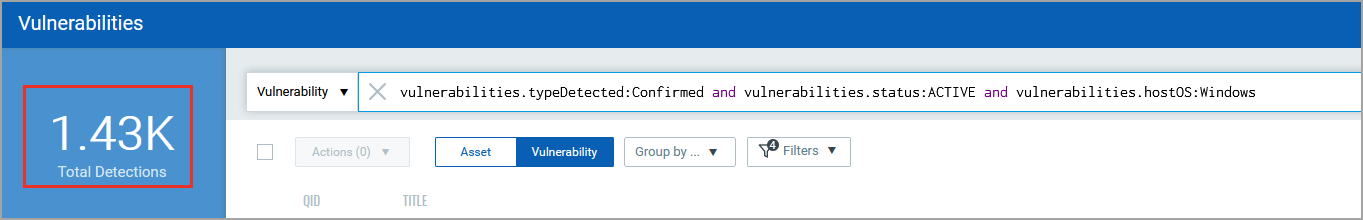
2) Let’s go for a little more complex query. Let’s find out vulnerabilities having the detection type as Confirmed, with ACTIVE status and those detected on Windows assets.
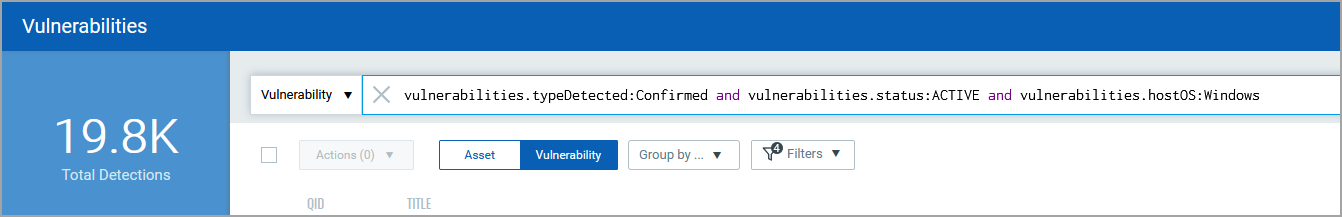
Run the query and you will find that we have narrowed down our search considerably.
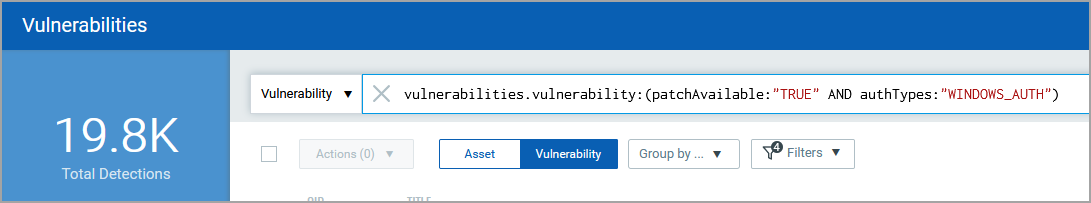
3) Here's an example of a nested query using parentheses. Run the query and note the results.
4) Let's create even a more complex nested query. Let's search for all the active instances of QID 100350 for assets scanned within the last 24 hours having the tag Windows Desktop or Cloud Agent, but not tag SiteA and Lab1.
It's important to reason out what exactly we're looking for. It's then important to use each query as a building block, add operators correctly and enclose your values in parentheses accurately.
Let's build each individual query first and later join all to form a complex one.
|
What we are looking for |
Query |
|
active instances of QID 100350 |
vulnerabilities.vulnerability.qid:`100350` |
|
assets scanned within the last 24 hours |
lastVmScanDate>=now-24h |
|
tag Windows Desktop or Cloud Agent |
(tags:(name:`Windows Desktop` OR name:`cloud agent`)) |
|
not tag SiteA and Lab1 |
NOT (tags:(name:SiteA AND name:Lab1)) |
Note: In the Asset search, the tags.name token returns the assets that are tagged with the given tag or its child tags.
If the Asset search is performed using the Group by Tags option, the Asset Count shown is only for the given tag.
Now that we have all the building blocks ready, let's create the single complex query by adding all these individual queries:
In the search bar for the Asset data source, add:
(lastVmScanDate>=now-24h AND (tags:(name:`Windows Desktop` OR name:`Cloud Agent`)) AND NOT (tags:(name:SiteA AND name:Lab1)))
In the search bar for the Vulnerability data source, add:
vulnerabilities.vulnerability.qid:`100350`
See Data Sources