Events
Events related to Salesforce, Dropbox and Office 365 can be viewed, filtered according to the service types. Events of varying criticality related to user, application, files can be viewed here. This view helps IT admins and Security Operations teams monitor any unusual activities.
What’s in it for the users?
To view any user activity, go to Monitor > Events.
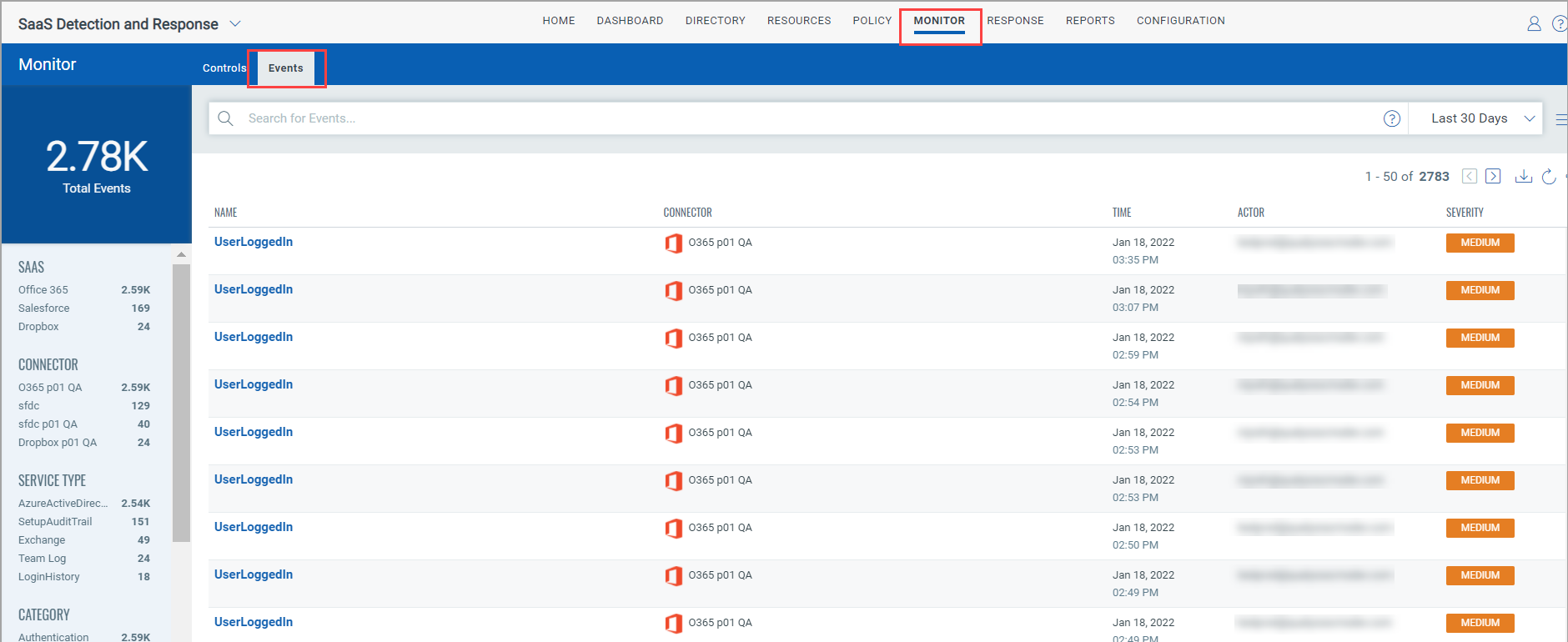
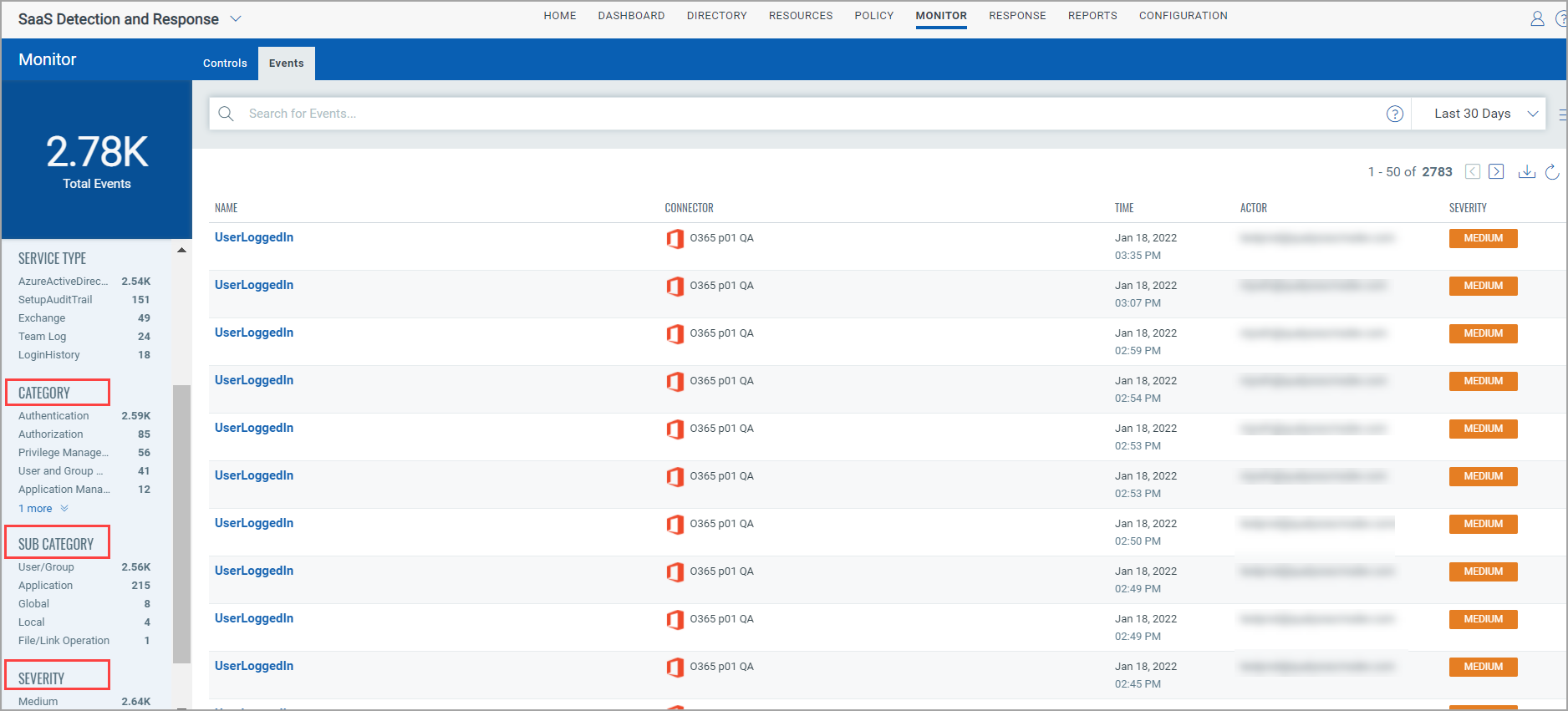
You can filter the activities by clicking on any Category, Sub Category or, Severity options available in left navigation pane. Filter is based on the variations of the events appearing in the list.
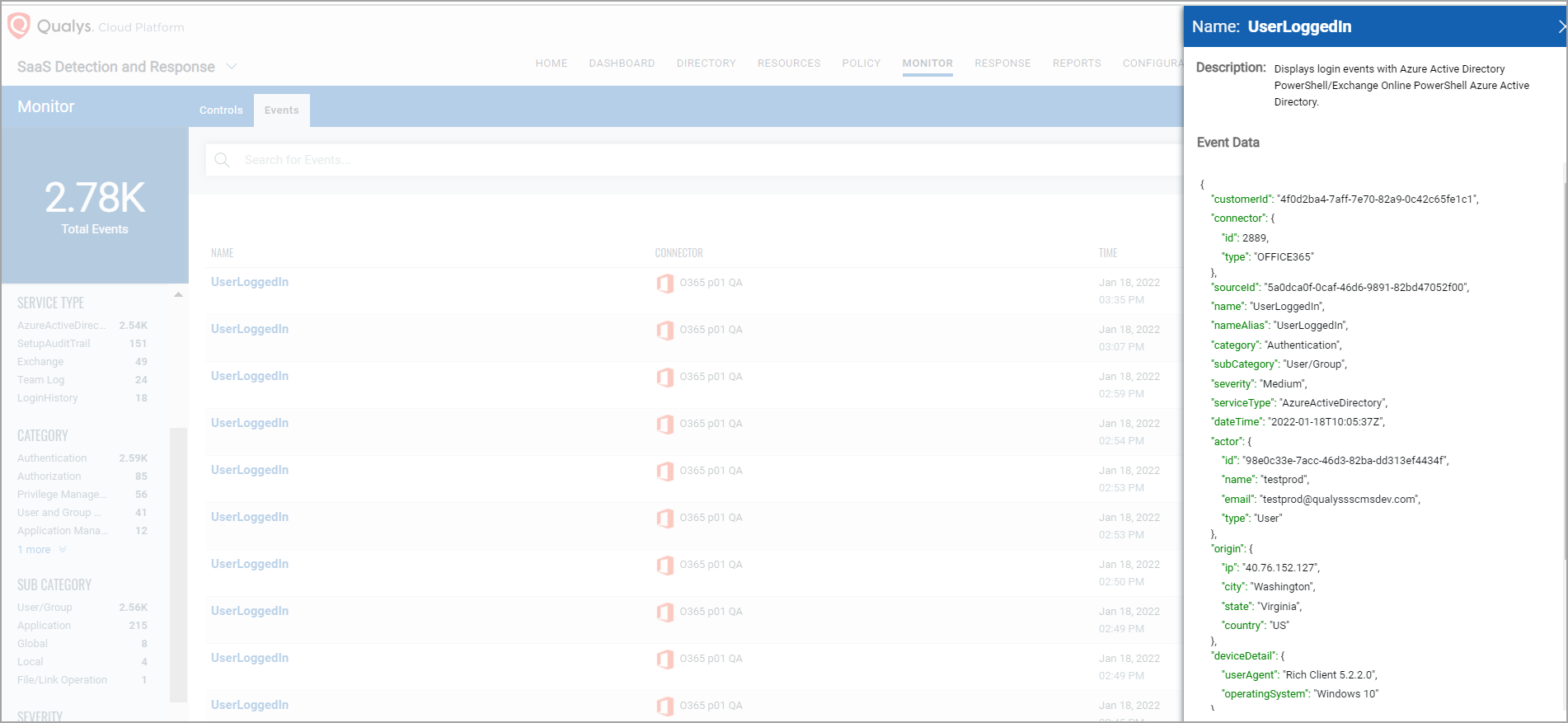
To view the details of the User Activity Event, click the Event, the detail page will show pop-up in JSON view.
SaaSDR monitors Salesforce logs, Dropbox logs and Office365 logs for events (as recommended by CISA) such as:
- Failed to login
- Update Application Permission
- Update Group
- Set domain authentication.
- Add admin role to a member
- Remove admin role
And lot more!
To know more on Office 365 logs for events, click here.