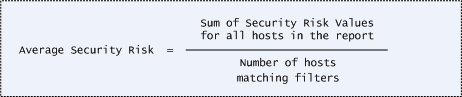
This formula is used for calculating the average security risk for the entire report.
A scan report includes current vulnerability information about hosts in your account (hosts you select at run time). The amount of detail included in the report is based on your report template settings.
|
|
With a scan report you can analyze trends in vulnerabilities detected, sort and filter scan data, generate graphical reports, and create executive reports that provide a high-level view of your overall network security.
Go to VM/VMDR > Reports > Templates. Hover over the scan report template you want to run and then select Run from the Quick Actions menu.
You choose the report target when you run the report. Then the hosts in your target that have scan findings will be included. All of these conditions must be true for a host to be included:
- The host was a target of a vulnerability scan.
- The host was found to be active (alive) during the scan.
- The host scan completed successfully and we returned findings (in the scan results).
- Findings were found for the host during report creation (host was not purged after being scanned). The findings may indicate vulnerabilities were detected or no vulnerabilities were detected.
Any host found to be active (alive) during the scan is counted.
Any host matching the filters defined in the report template is counted.
The Summary of Vulnerabilities provides an overview of all vulnerabilities detected for all hosts included in your report. The total number of detections includes vulnerabilities, potential vulnerabilities and information gathered. Notes: 1) For a trend report this is the number of detections in the report timeframe. 2) Fixed vulnerabilities (and fixed potential vulnerabilities) are not counted. 3) You'll see a trend number indicating whether the total increased, decreased or stayed the same as compared to previous scans. The trend number includes vulnerabilities and potential vulnerabilities only (not information gathered).
We'll show a security risk score for the overall report (in the report summary) and per host (in the detailed results). Your scan report must: 1) be template based (Executive Report, High Severity Report, Technical Report, or another report based on a scan report template), and 2) select host based findings (instead of scan based findings).
The score for the overall report is the average security risk for all hosts in the report (all hosts matching filters). This is calculated as the sum of all security risk scores for all hosts in the report divided by the number of hosts. The score for each host is the average severity level detected (the default) or the highest severity level detected - all vulnerabilities and potential vulnerabilities are counted in the calculation. Managers can configure the calculation method for the subscription by going to Reports > Setup > Security Risk. (Are you an Express Lite user? If yes the average severity level is always used.)
Show me the formulaShow me the formula
This formula is used for calculating the average security risk for the entire report.

What if my report isn't sorted by host?What if my report isn't sorted by host?
The security risk value displayed in the Detailed Results section of the report is the security risk for all hosts that match the sorting method (host, operating system, asset group, etc).
For example, if you sort by host you see the security risk for each host. If you sort by operating system you see the security risk for all hosts with the operating system. If you sort by asset group you see the security risk for all hosts in the asset group. The same methodology applies to the other sorting methods.
Don't see the score per host?Don't see the score per host?
You might need to configure your scan report template. Be sure to select Text Summary under Display > Detailed Results.
Business risk is expressed as a value (0 to 100). Generally, the higher the value the higher the potential for business loss since the service returns a higher value when critical assets are vulnerable. A Manager can configure business risk by going to Reports > Setup > Business Risk. (Express Lite users cannot edit the settings.)
Business risk in the Summary of Vulnerabilities section represents the overall business risk for the entire report. Business risk is first calculated for each asset group/host in the report, and then the average of those values is calculated and displayed in the summary.
Business risk in the Detailed Results section represents the business risk value for each asset group (only included when results are sorted by asset group).
For asset groups in the report, the business impact level assigned to each group is used in the business risk calculation. When individual IPs are included in the report, a business impact level of High (or its equivalent) is used in the calculation. This is because these IPs may be included in multiple groups or no groups at all.
CVSS v2 and v3.1 scores along with their vector strings will now appear at the vulnerability level when detailed results are sorted by host or asset group.
You'll see CVSS scores for each vulnerability when the following conditions are true: 1) You run a scan report (template based) with host based findings, and 2) the CVSS Scoring feature is enabled for the subscription.
Learn more about CVSS v2 and v3.1 vector strings
Depending on your template settings, your results may contain the following details for each vulnerability: the assigned QID, CVE ID, Bugtraq ID, CVSS Base and Temporal scores, descriptions of the threat, impact and solution, exploitability and malware information from third party vendors and/or publicly available sources, and specific scan test results for each vulnerability instance. You can also choose to include a list of CVE IDs detected for each QID for each asset. Learn more
You'll see TruRisk details in the report, including Asset Risk Score (ARS), Asset Criticality Score (ACS) and Qualys Detection Score (QDS) when this option is selected in your scan report template.
The Asset Risk Score and Asset Criticality Score appear in the host summary section. The Qualys Detection Score appears when you expand vulnerability details.
Anytime you include vulnerability details in your scan report, you'll see a list of associated CVE IDs for each QID. This list includes all CVE IDs that are associated with the vulnerability, not what was detected. This list appears as "Associated CVEs" in the report.
A pencil![]() next to the severity level indicates that the vulnerability was edited. The content (Threat, Impact and Solution) and/or the severity level was changed by a Manager.
next to the severity level indicates that the vulnerability was edited. The content (Threat, Impact and Solution) and/or the severity level was changed by a Manager.
The detailed results section of your report is organized by one of these methods: host, vulnerability, asset group, operating system, service or port. Edit your scan report template to change the method used.
In scan results reports, hosts are always listed by IP address. In scan reports that include host based findings, hosts are listed by the host's tracking method: IP address, DNS hostname or NetBIOS hostname. For each host you'll see details like the operating system detected on the host.
Tell me about asset tags displayed for each hostTell me about asset tags displayed for each host
When your subscription has Asset Tagging and tags were used to run your report, then you'll see a list of tags for each host. The list includes the tag(s) that matched the tags selected for host targets, as well as other tags assigned to the host.
For example, let's say host 10.10.10.65 has these 3 tags assigned: 10.10.10-network, Linux and Milwaukee. Milwaukee is a child tag of USA. If you run a report on the tag USA then host 10.10.10.65 appears in the report (since it is the parent tag of Milwaukee) and the tags listed for this host are USA, 10.10.10-network, Linux and Milwaukee.
Tell me about OS CPETell me about OS CPE
This is the OS CPE name assigned to the operating system detected on the host. (The OS CPE name appears only when the OS CPE feature is enabled for the subscription, and an authenticated scan was run on this host after enabling this feature.)
You can include many different graphs in your report by editing your scan report template. Keep in mind that your filter settings will affect the data reflected in your graphs. If you see "There is no data available" in your graph, check your filter settings.
10 Most Prevalent Vulnerabilities10 Most Prevalent Vulnerabilities
This graph displays the 10 most frequently reported vulnerabilities. These vulnerabilities appear the most often for the report target. For example, a vulnerability may be detected for the first time in your report, but if it is detected on many hosts, it may be considered one of the most prevalent vulnerabilities. A trend is also included to show whether the number of occurrences for each vulnerability increased or decreased.
Operating Systems DetectedOperating Systems Detected
This graph displays all detected operating systems. Notes: 1) We may not have been able to detect the operating system for every host in your report. 2) No data will be available for this graph if QID 45017 (Operating System Detected) was not included in the scan.
Services DetectedServices Detected
This graph displays all services, such as ssh, ftp and smtp, discovered under the Open TCP and Open UDP Services lists. Notes: 1) A service may be counted more than once for a single host if the service is discovered on different ports. 2) Services may not have been detected on all hosts in your report. 3) No data will be available for the graph if QID 82023 (Open TCP Services List) and QID 82004 (Open UDP Services List) were not included in the scan.
This is a list of vulnerabilities (QIDs) that were found on non-running Linux kernels on the hosts in your report. This section appears only when "Display non-running kernels" is selected in your report template (on the Filter tab). Tip - You can also choose to filter out vulnerabilities on non-running kernels.
You'll see some additional information in the Appendix section at the end of your report.
No results available for these hostsNo results available for these hosts
This list includes up to 200 IPs that don't have scan results. Possible reasons:
- Hosts were not "alive" at the time of the scan
- Hosts were never scanned
- Hosts were scanned but the data was purged
Don't see the list of IPs? You'll see the number of IPs that don't have scan results.
This list includes IPs that were scanned but results are not shown for these reasons:
- No vulnerabilities were detected
- All vulnerabilities were filtered out. You can edit your filter settings in the report template to see these results.
Don't see the Appendix?Don't see the Appendix?
Edit your scan report template and select the "Appendix" option in the Display settings.
Scroll down to the Detailed Results section of your report, click ![]() and choose an action. The action you choose applies to the vulnerability instance (vulnerability/host/port).
and choose an action. The action you choose applies to the vulnerability instance (vulnerability/host/port).
Check out these options: Ignore vulnerabilityIgnore vulnerability | Activate vulnerabilityActivate vulnerability | View / Create ticketView / Create ticket
View an existing ticket or create a new one. When you create a ticket, the action is logged in the ticket history with your name and time stamp. You can make changes to an existing ticket by selecting File > Edit when viewing the ticket details.
Activate a vulnerability that's been marked ignored. You can do this when viewing a scan report (template based) with host based findings.
Ignore a vulnerability to filter it out of the UI (host information, asset search, dashboard, etc) and template based scan reports with host based findings.
How it works - If no remediation ticket currently exists, we'll create one and close it automatically for tracking purposes. Already have a ticket for this? If yes we'll close associated tickets for the vulnerability.
Don't see these options?Don't see these options?
You'll see these options only when viewing a scan report (template based) with host based findings in HTML format and vulnerability details included.
Scanners and Readers may not have permission to ignore/activate vulnerabilities, depending on remediation options set for the subscription.
Are you an Express Lite user? If yes, the ticket options are not available.