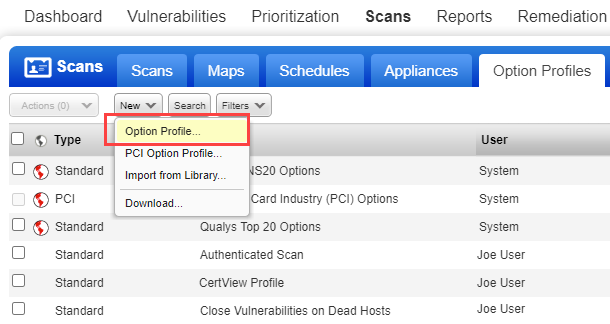
The Scans > Option Profiles section is where you'll find the option profiles in your subscription. You can create new option profiles or make changes to existing option profiles.
See Option Profile Settings below for help with the various settings that appear within the option profile.
Follow these steps to create or edit an option profile:
1) Go to Scans > Option Profiles.
2) Take one of these actions:
2a - To create a new option profile, select New > Option Profile.

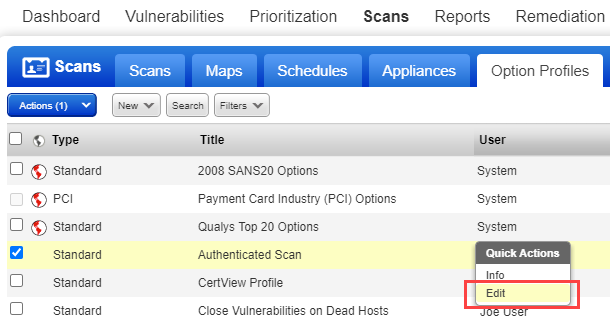
2b - To make changes to an existing option profile, select an option profile in the list and choose Edit from the Quick Actions menu.
The New Option Profile or Edit Option Profile window appears (depending on the action taken). This is where you'll make your map and scan settings.
3) Choose a tab on the left side of the option profile window to see the map and scan settings available. Make your selections on each tab, and then click Save to save your option profile.
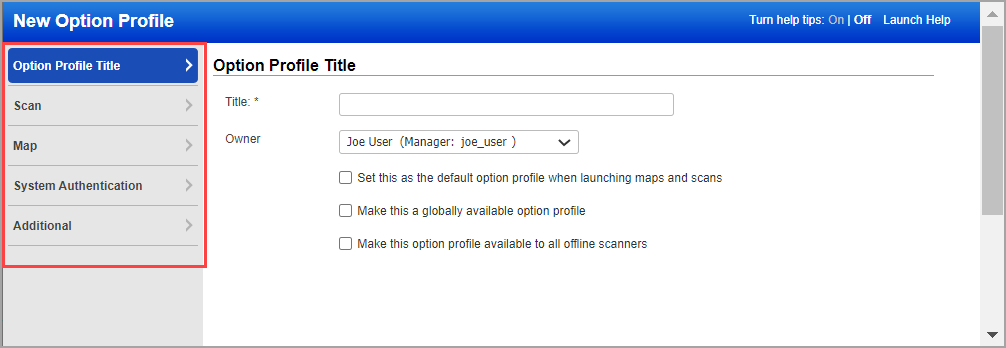
See the links below to get help for the various settings that appear on each of the tabs within the option profile.
Option Profile Title - This section has basic settings for the option profile like title and owner and whether the profile should be the default profile, or globally available.
Scan - This section has scan settings like which ports to scan, which QIDs to scan, whether to include authentication, scan performance settings, and more.
Map - This section has map settings like which ports and hosts to scan for basic information gathering on hosts during mapping and whether to disable DNS traffic.
System Authentication - This is where you can enable the use of system created authentication records in vulnerability scans.
Additional - This section has additional settings that affect both scans and maps, including the ports to scan during host discovery, and the ability to ignore certain types of packets sent at scan time.
If you made changes to an option profile and want to return to the default settings, simply click the Restore Defaults button in the option profile. We will reset all the settings across all the tabs.