You have multiple options for evaluating databases for security and compliance.
Jump to a section below:
Deep Assessment with Database Credentials Using Scanner
Limited Assessment Using Scanner
Limited Assessment Using Cloud Agent
Use privileged database user accounts in addition to host credentials to authenticate into your database instances running on Unix or Windows hosts. Qualys PC offers authenticated scanning for several database technologies. Simply create authentication records to allow the scanner to connect directly to a database using credentials that you provide, and scan it for compliance.
Each record identifies an authentication type, account login credentials and target IP addresses. You may also need to provide OS specific details like the path to the database configuration file on your Windows or Unix host. See the online help for each record type to know what’s required.
Authentication records in your account are used automatically for compliance scans. Being able to log into each database with a scanner provides the most in-depth coverage.
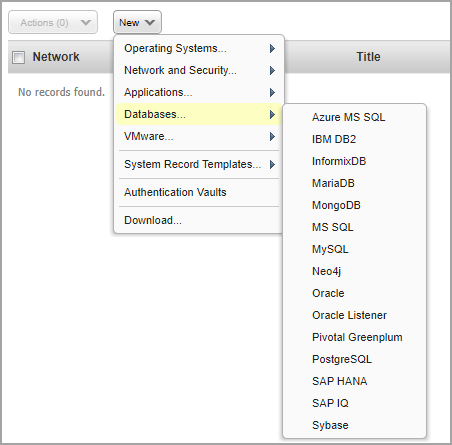
To create database authentication records, go to PC > Scans > Authentication and choose New > Databases. Select from the list of database technologies (note that this list will grow as we add new database technology records).

Organizations have traditionally used privileged database user accounts in addition to host credentials to authenticate into their database instances running on Unix or Windows hosts. But sharing database credentials with security teams presents a security and governance challenge for organizations, and the teams performing these assessments may not have privileged access to the databases.
We offer the ability to perform a limited assessment with only OS credentials when database authentication is not possible. This makes assessments simpler and more secure as customers do not need to create any additional restricted user accounts on their databases running on Unix or Windows hosts.
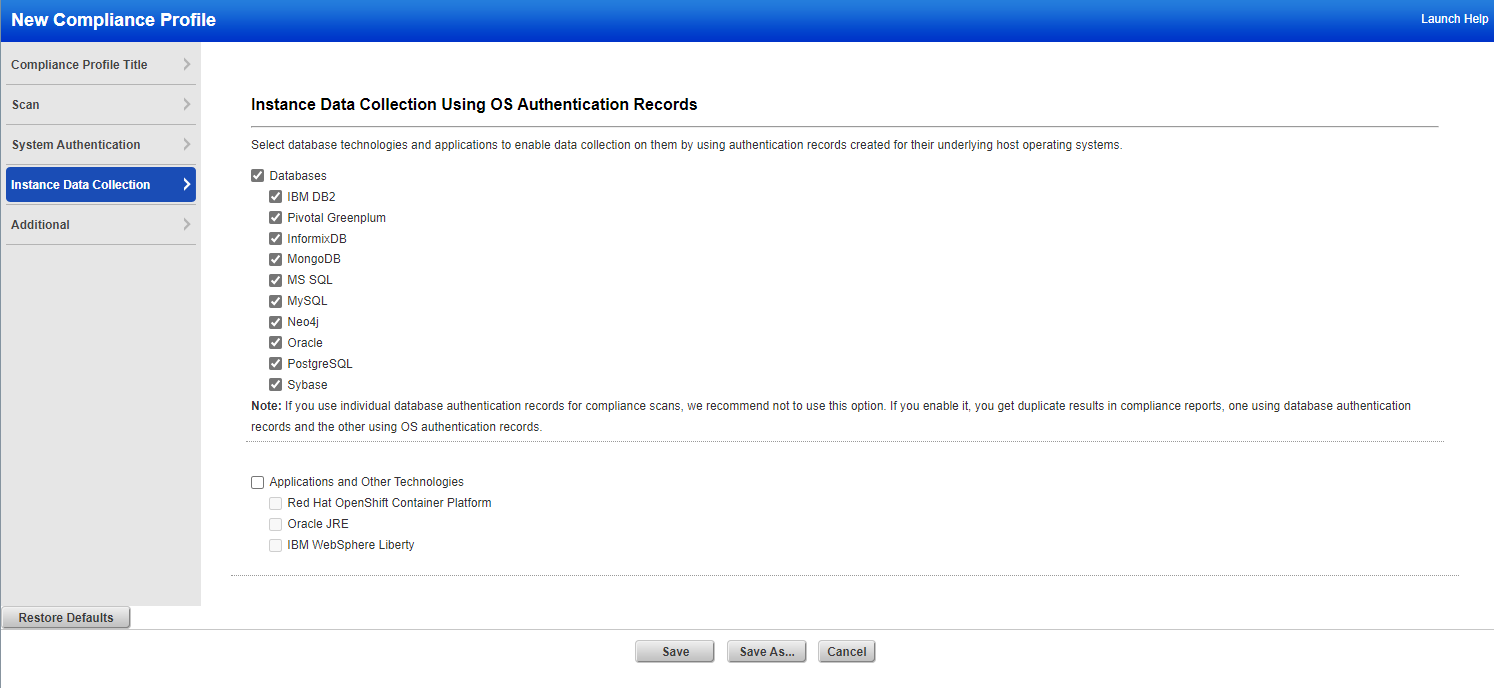
If you’re using a scanner, the Compliance Option Profile has the option to enable OS-based instance data collection. Selecting this option enables data collection for the supported databases using the underlying OS-based authentication records. Once the compliance profile is updated, simply launch compliance scans with this option profile for authenticated scanning. Note that only OS-dependent database controls will be evaluated in this case.
To enable instance data collection, go to PC > Scans > Option Profiles > New > Compliance Profile. Select Instance Data Collection. Click Databases and select each database technology you’re interested in. Apply this profile to your next compliance scan. See Configure Your Scan Option Profile (PC) to learn more about this feature.
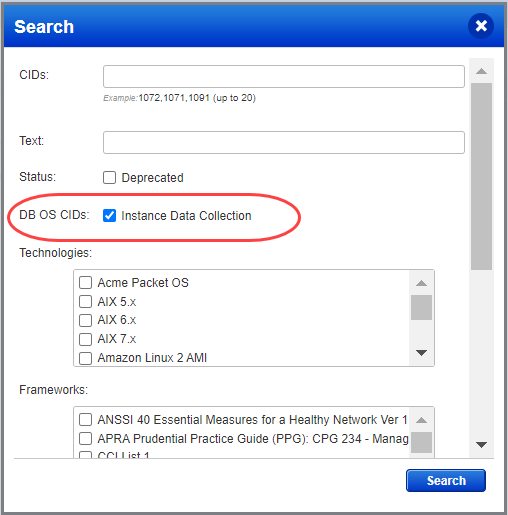
Only OS-dependent database controls are used in data collection and evaluation for limited assessments. You can search for these controls by going to PC > Policies > Controls and clicking the Search button. In the Search window, select Instance Data Collection next to DB OS CIDs. The search returns OS-dependent database controls that are system-defined and supported by Scanner.
The auto-discovery feature in Qualys Cloud Agent discovers the database instances on the system where Cloud Agent is running. Cloud Agent running on Windows or Unix discovers and inspects the database instances through registry keys or running processes, without logging into the database.
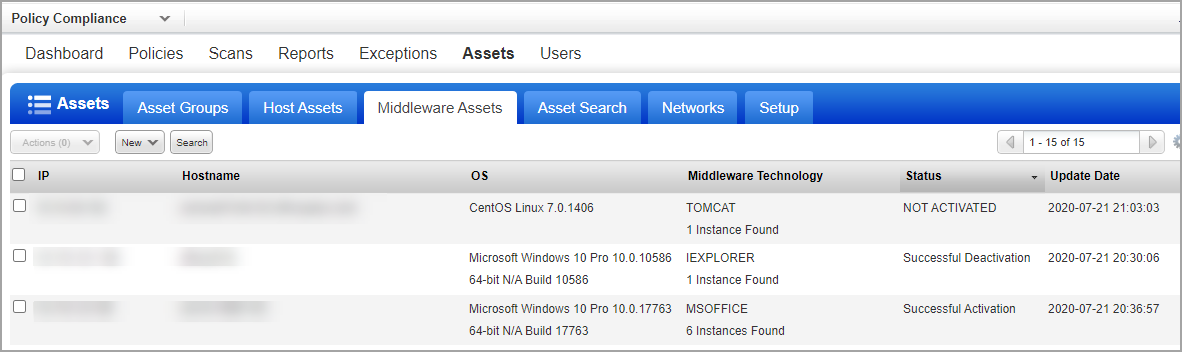
Once the assets are discovered and middleware technology details are listed on the Middleware Assets page, as shown below, you can activate the assets for middleware assessment, either selectively or choose default activation (recommended) for assessment to begin as soon as they are discovered. See Evaluate Middleware Assets by using Cloud Agent to learn more.
If middleware assessment is already enabled, Cloud Agent will auto-discover the database instances and assess for OS-dependent database controls. No additional user action is required to enable this functionality.
For the most current list of middleware technologies auto-discovered by Cloud Agent, please refer to this article:
Middleware Technologies Auto-discovered by Cloud Agents for PC