You can ignore confirmed and potential vulnerabilities so they don't appear as actionable issues for your vulnerability management program. A vulnerability can be ignored for an instance, in other words a host/vulnerability/port.
By ignoring vulnerability instances:
- You won't see these vulnerabilities throughout the UI (host information, asset search results, your dashboard, etc).
- These vulnerabilities will no longer appear in template based scan reports with host based findings.
- We'll close any remediation tickets for these vulnerabilities automatically. (Are you an Express Lite user? If yes, remediation ticket options do not apply.)
You can ignore a vulnerability while viewing vulnerability details in the UI (host information). Simply hover over the desired host and click View Host Information icon ![]() . Then from the Vulnerabilities tab select a vulnerability, place your cursor over the menu icon
. Then from the Vulnerabilities tab select a vulnerability, place your cursor over the menu icon ![]() and select Ignore vulnerability.
and select Ignore vulnerability.
You can also ignore vulnerabilities from within template based reports with host based findings. Just navigate to a vulnerability, place your cursor over the menu icon ![]() and select Ignore vulnerability.
and select Ignore vulnerability.
Once a vulnerability is ignored it is not listed in Asset Search. However, in AssetView the ignored vulnerabilities are listed by default and you need to use an additional query to filter them out.
Tell me about QIDs that cannot be ignoredTell me about QIDs that cannot be ignored
You cannot ignore information gathered checks, or the following QIDs: 38175 (Unauthorized Service Detected), 82043 (Unauthorized Open Port Detected), 38228 (Required Service Not Detected) and 82051 (Required Port Not Detected).
Tell me about user permissionsTell me about user permissions
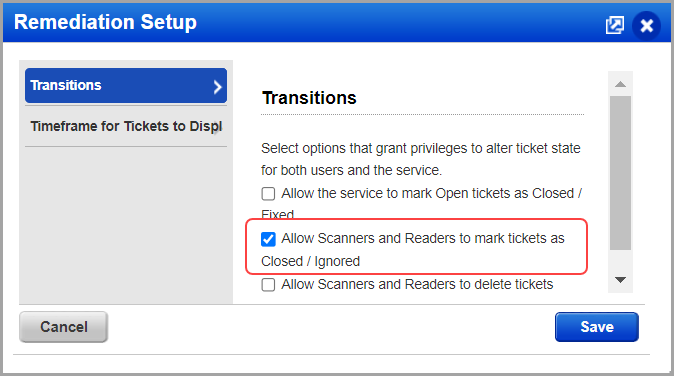
Managers and Unit Managers are allowed to ignore any vulnerability instance (host/vulnerability/port). The option to ignore vulnerabilities is available for Scanners and Readers, depending on remediation options set for the subscription. Go to Remediation > Setup.
Note: The Manager or Unit Manager user needs to assign asset groups to the Scanner and Reader users to ignore the vulnerability instances.
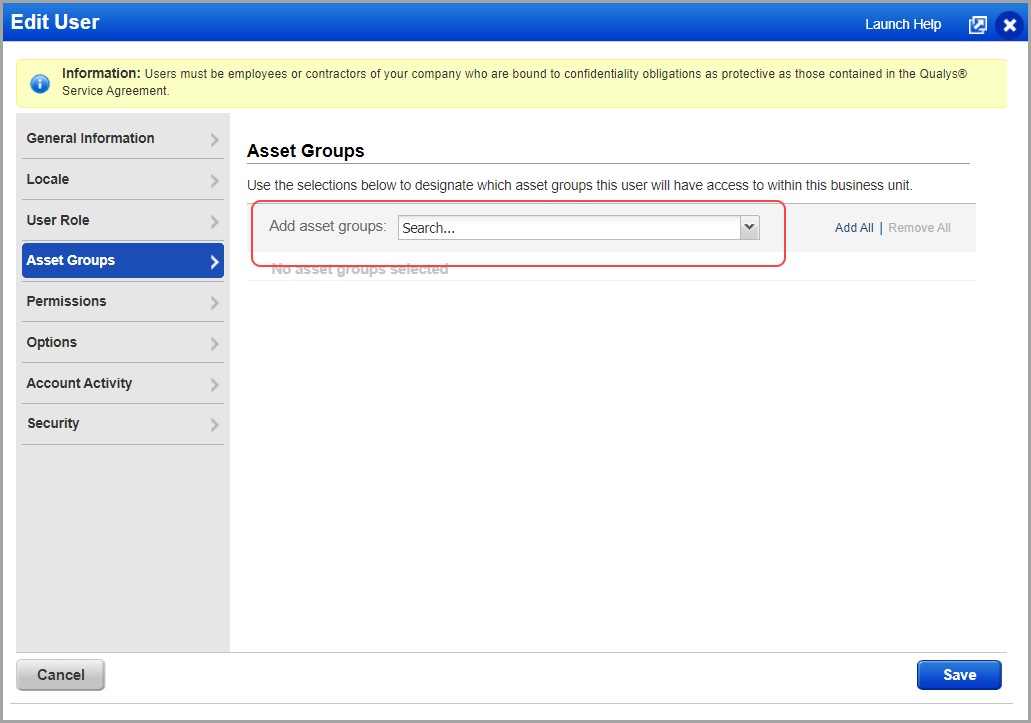
Manager or Unit Manager users can edit the existing user's profile or while creating a new user profile, can assign asset groups.
To assign asset groups to a user, go to Users > select the user's profile from the list and click Edit.
From the Asset Groups tab, add an asset group from the list and click Save.
When you ignore a vulnerability we'll create a ticket for the issue if no ticket currently exists for it, and close it automatically for tracking purposes.
You'll need to find the closed remediation ticket for the ignored vulnerability and reopen it. Go to VM/VMDR > Remediation > Tickets. Use the Search option to list all tickets for the applicable host (search by IP, DNS, etc) and then use the Filters option to only show the Closed/Ignored tickets for the host. Identify the ticket for the vulnerability you want to un-ignore, and pick Edit from the Quick Actions menu. Then pick Reopen from the Actions menu, and click Save. The ticket state will change to Open and you'll start seeing the vulnerability in your reports again.
Managers can filter vulnerabilities on a global basis, across all hosts, by disabling them. Just edit the vulnerability in the KnowledgeBase and select "Disable this vulnerability". Note - Disabling vulnerabilities will not result in the automatic closing of tickets because the setting applies to all your hosts.
Still see an ignored vulnerability in my report?Still see an ignored vulnerability in my report?
You must refresh the report to remove the ignored vulnerability. Note that you can edit the filter settings in the report template to always display ignored vulnerabilities in your scan report.
You can choose to include ignored vulnerabilities in template based scan reports with host based findings. Just edit the report template and change the filter settings.