Customize the various options for running a scan. These can be saved as profiles for reuse. A default profile is provided for common environments. Go to Configuration > Option Profiles.
User roles and permissions determine whether users have WAS Configuration Permissions; there are individual permissions for creating, editing and deleting option profiles and the other WAS configurations. Learn more
Apply tags to an option profile to make it available to other users. Users with a tag in their scope that matches a tag applied to an option profile will be able choose that profile for scans.
We provide the option profile called "Initial WAS Options" with recommended settings for web application scanning to help you get started. You can customize and rename this profile.
You can choose to define an option profile as the default for your subscription as long as your account has full permissions and scope. Just select the setting "Make this the default option profile for the subscription". We'll select that profile automatically each time you launch a scan, unless another option profile is defined for the target web application. (You can still choose to override the default in your scan settings.)
The user who creates a profile is set as the initial owner by default. Users with permission to edit option profiles can change the owner.
The crawling settings tell us how the scanner should submit requests to forms. Post & Get is the default setting. With this setting, the scan submits requests to all forms. For authentication, this option is recommended best practice to ensure maximum vulnerability analysis and the most comprehensive scan results. You can select None if you want requests submitted to no forms unless authentication is requested, in which case only the login form will be tested. You can also select POST to instruct the scan to submit requests only to POST forms, or GET for submitting requests only to GET forms.
To prevent forms with same fields from being ignored during the scan, you should select Form Crawl Scope option. If you enable Form Crawl Scope, we will use form action URI in addition to form fields to calculate form uniqueness. Learn more
Yes, if the option profile setting "Ignore common binary files..." is selected in your option profile settings. When enabled, scans will ignore all files with these extensions: pdf, zip and doc. This option is enabled by default when you create an option profile and can be edited for any option profile at any time.
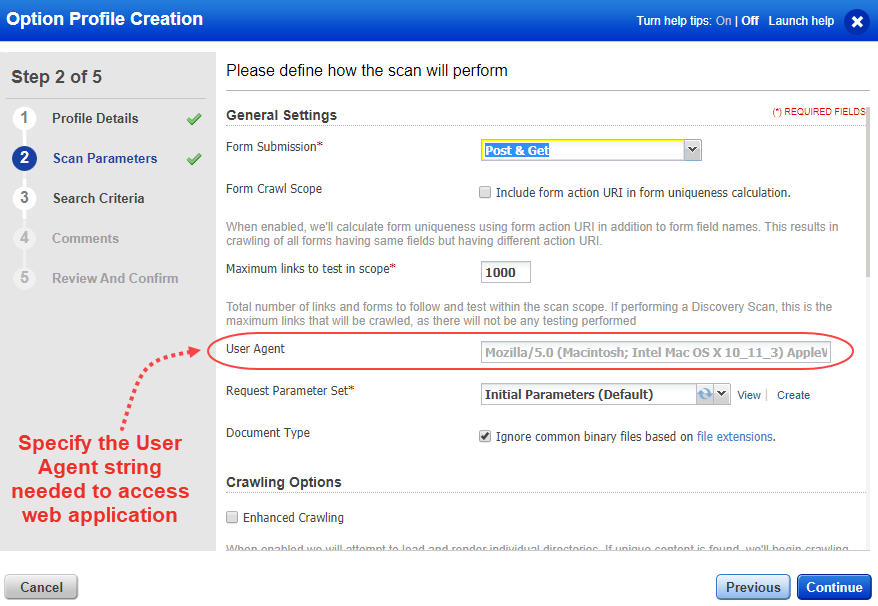
If your web application requires specific user-agent string to access it, you need specify the same. To specify the user-agent string, when you configure option profile for a scan, you can specify the user agent settings of your web application in User Agent field of General Settings. Show me
If you do not specify any user agent settings, the scan uses default user agent settings. The default user agent setting that is used is user-agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_11_3) AppleWebKit/601.4.4 (KHTML, like Gecko) Version/9.0.3 Safari/601.4.4
If your web application uses certain user settings, and if you do no the specify the same, the web application may not get loaded in such cases. Show me
To know the user-agent string for a web application, copy the user-agent string from the request headers, by accessing the web application from your desired browser. Show me
We have two options to improve crawling of web applications during scan:
The performance settings allow you to set the overall intensity level for web application scans. You could either choose to select a pre-defined setting or configure your custom scan intensity. Learn more
Use password bruteforcing to find out how vulnerable your web applications are to password-cracking techniques. Choose "System list" and we'll attempt to guess the password for each detected login ID. Select the level of brute forcing you prefer with options ranging from "Minimal" to "Exhaustive". Choose "User list" to select a bruteforce list defined in your account (Configuration > Bruteforce Lists). Learn more
The detection scope settings determine whether the scan will check for vulnerabilities in our KnowledgeBase.
XSS Payloads: You can enable comprehensive tests for cross-site scripting vulnerabilities to be executed during our standard scan using the Include additional XSS payloads checkbox. The comprehensive tests includes XSS with exhaustive set of payloads including set of standard payloads. Running a scan with XSS payloads option enabled in the detection scope of scan will provide the best assurance that your web application is free from XSS vulnerabilities. However, enabling this option leads to significant increase in the scan time. Show me
- Core: The "core" detection scope is the default for new WAS option profiles. Core scope includes vulnerabilities that Qualys considers most common in today's web applications. It does not include all the vulnerabilities that WAS can detect. For example, vulnerabilities such as QID 150233 - XSS vulnerabilities in old versions of Atlassian JIRA or QID 150225 - vulnerabilities in Liferay Portal are not included when Core detection scope is defined for the scan. Testing for all possible vulnerabilities will result in longer scan times.
You can always run scans with complete detection scope, if required. Simply create a dynamic search list and mark all the check boxes under Confirmed Severity, Potential Severity, and Information Severity. In WAS option profile, select "Custom Search Lists" for Detection Scope and add that dynamic search list.
- Categories: specific vulnerabilities defined in the categories. Select a category to check for associated vulnerabilities in the scan. For example, Experimental category. This category consists of QIDs reported by to reduce False Positives or False Negatives scenarios. Experimental QIDs are findings where the vulnerability cannot be confirmed through an active Proof of Concept (POC). The reasons that the vulnerabilities could not be confirmed can include:
- Not all environments related to the vulnerability were tested due to logistics like licenses, access, or time constraints.
- Vulnerabilities may be limited to specific environments.
- The QID confirmation is in progress and all the variants to be tested and reported are not complete.
To view the detections/QIDs included in a particular category, click the number indicating number of QIDs added for each category.
- Custom Search Lists: specific vulnerabilities defined in search lists. This provides the most granular control over detection scope. You can select search lists to include and search lists to exclude. Any QID's in the included list are included and those in the excluded list are excluded from the scope. The Custom Search Lists setting enables you to choose search lists defined in your account (Configuration > Search Lists) to identify vulnerabilities you want to include and vulnerabilities you want to exclude. Learn more
- XSS Power Mode: comprehensive tests for cross-site scripting vulnerabilities. The XSS Power Mode detection scope performs tests using the standard XSS payloads, which detect the most common instances of XSS, but also with additional payloads that can identify XSS in certain, less-common situations. Running a scan with XSS Power Mode will increase the scan time but would provide more comprehensive testing for XSS vulnerabilities.
- Everything: all the vulnerabilities that WAS can detect. Select Everything in detection scope to check for all the WAS related vulnerabilities in a scan and this could lead to a longer scan time.
Add search lists to select the vulnerability checks (QIDs) to scan for. Click "Add search list" to select existing search lists. Click "Create new" to create a new search list (static or dynamic). Note that the search lists you add must contain only web application vulnerabilities.
Add search lists to select the vulnerability checks (QIDs) to exclude from scans. Click "Add search list" to select existing search lists. Click "Create new" to create a new search list (static or dynamic). Note that the search lists you add must contain only web application vulnerabilities.
Our service can check for sensitive content in the web application pages it crawls based on known patterns (such as credit card numbers, social security numbers) or based on custom patterns you enter. The expression search mechanism can check for credit card numbers and social security numbers (United States only) while reducing false positives. Our service does not collect credit card information or social security information.
Important: Sensitive content detection will be performed only when you scan for QID 150016. If you select Custom in the Detection Scope settings, you must add an "Include" search list that includes QID 150016.
We let you search for URL links by keywords that can be specified in the form of strings and regular expressions. The Keyword URL Search field in the Search Criteria tab allows you to specify keywords. At the time of the Discovery/Vulnerability scan, we search for these keywords in the internal links that are found for the target web applications in the crawling phase . We then report all the unique links that have the specified keywords in the WAS scan and web application reports under information gathered QID 150141.
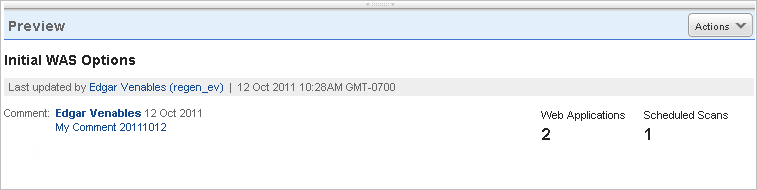
The preview pane appears under the list when you click an option profile row. The preview displays the number of web applications and scheduled scans using the option profile, the name of the user who last updated the option profile, the date and time of the update and the last comment added.
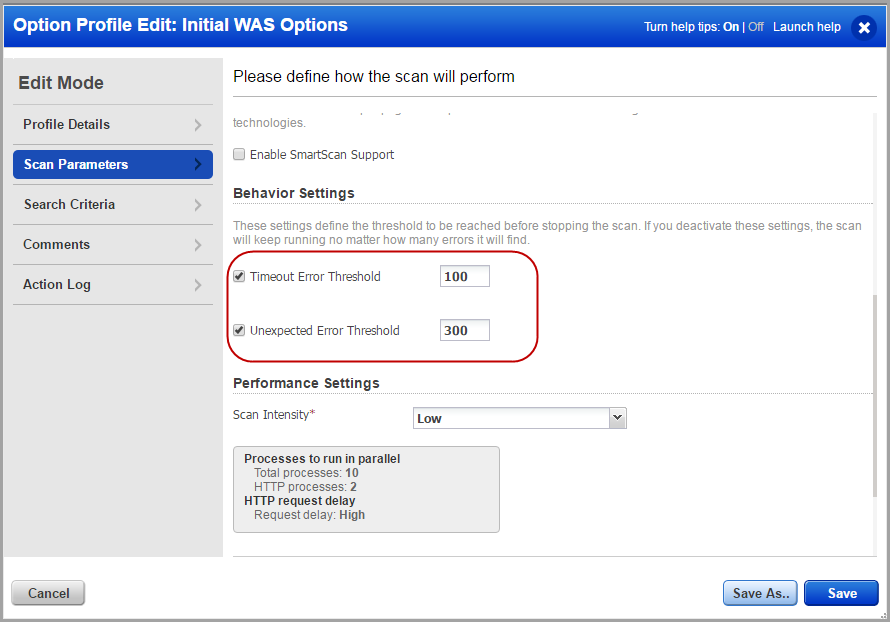
Tell us the threshold for the timeout and unexpected consecutive errors that would be allowed during a scan. We will terminate the scan if the number of errors during the scan exceed the specified threshold.
You can customize Core, XSS Power Mode, and Categories detection scopes from the option profile.
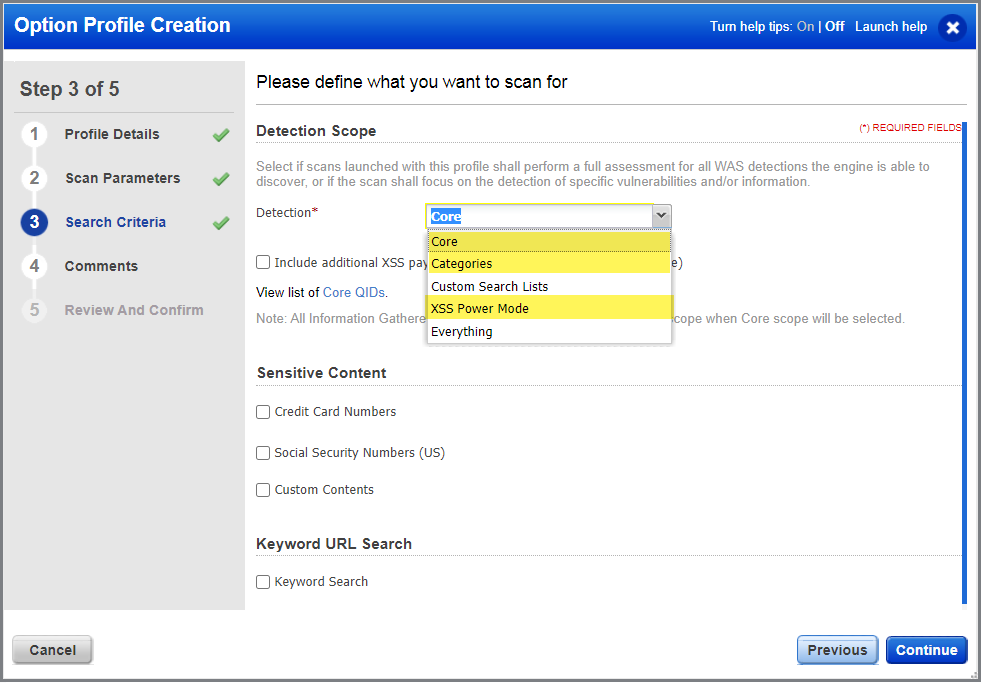
To customize the detection scopes, create or edit an option profile with detection scope set as Core, XSS Power Mode Detection Scope or Categories. On the create/edit option profile screen, go to the Search Criteria tab.
For "Core" detection scope, Click the link Core QIDs in "View list of Core QIDs". From the QIDs included in Core Detection Scope screen, click Copy All QIDs. Next, add or remove QIDs from the list as desired, then create a new search list with these QIDs.
For "XSS Power Mode detection scope", click the link "here" in "View list of XSS QIDs here". From the QIDs included in XSS Power Mode Detection Scope screen, click Copy All QIDs. Next, add or remove QIDs from the list as desired, then create a new search list with these QIDs.
For "Categories" scope, click the number showing the total number of QIDs for the category that you want to customize. From the "QIDs included in category" screen, click Copy All QIDs. Next, add or remove QIDs from the list as desired, then create a new search list with these QIDs.