Qualys has integrated Real-time Threat Indicators (RTI) to deduce Vulnerability Intelligence with the Qualys Cloud Platform. Qualys gathered many of the RTIs for years now for internal use to prioritize vulnerability signature development and is now exposing the same for customers.
Real-time Threat Indicators are data points collected per vulnerability. It is accurate, timely and actionable information aggregated from multiple reliable data sources to prioritize and shrink flood of security alerts. Current Real-time Threat Indicators are:
High Data Loss - Successful exploitation will result in massive data loss on the host. |
High Lateral Movement - After a successful compromise, attacker has high potential to compromise other machines in the network. |
Wormable - Wormable has been associated with this vulnerability. The vulnerability can be used in “worms” - malware that spreads itself without user interaction. |
Denial of Service - Successful exploitation will result in denial of service. |
Patch Not Available - Vendor has not provided an official fix. |
Privilege Escalation - Successful exploitation allows an attacker to gain elevated privileges. |
Unauthenticated Exploitation - Exploitation of this vulnerability does not require authentication. |
Remote Code Execution - Successful exploitation allows an attacker to execute arbitrary commands or code on a targeted system or in a target process. |
Active Attacks - Active attacks have been observed in the wild. This information is derived from Malware, Exploit Kits, acknowledgment from vendors, US-CERT and similar trusted sources. In addition, if there are no patches available from the vendor, Qualys will also add the Zero Day RTI. |
Malware - Malware has been associated with this vulnerability. |
Zero Day - Active attack has been observed in the wild and there is no patch from the vendor. An active attack is a prerequisite for this RTI in addition to no patch from the vendor. If a vulnerability is not actively attacked this RTI will not be set (even if there is no patch from the vendor). If a patch becomes available Qualys will remove the Zero Day RTI attribute which helps users to focus only on vulnerabilities that are actively exploited and there is no official patch. |
Public Exploit - Exploit knowledge is well known and a working exploitation code is publicly available. Potential of active attacks is very high. This attribute is set for example when PoC exploit code is available from Exploit-DB, Metasploit, Core, Immunity or other exploit vendors. This RTI does not necessarily indicate that active attacks have been observed in the wild. |
Predicted High Risk - Predicted High Risk has been associated with this vulnerability. Leverages machine learning to determine if a non-exploited vulnerability should be prioritized. |
Easy Exploit - The attack can be carried out easily and requires little skills or does not require additional information. |
Exploit Kit - Exploit Kit has been associated with this vulnerability. Exploit Kits are usually cloud based toolkits that help malware writers in identifying vulnerable browsers/plugins and install malware. Users can also search on Exploit Kit name like Angler, Nuclear, Rig and others. |
Wormable - Wormable has been associated with this vulnerability. The vulnerability can be used in “worms” - malware that spreads itself without user interaction. |
Solorigate Sunburst - Solorigate Sunburst has been associated with all the CVEs, used by FireEye's Red Team tools to test the security of their client environments and compromised versions of SolarWinds Orion. |
Ransomware - This vulnerability has been exploited in attack vectors where ransomware has been deployed. In other words, this vulnerability is associated with known ransomware. |
CISA Exploited - CISA maintains a catalog of the top publicly known vulnerabilities being exploited in the wild and organizations are advised to patch affected systems on priority. This RTI indicates that the vulnerability is associated with the CISA catalog and with CVE mappings to respective QIDs. |
Qualys gathers RTI information from its own research and from multiple external sources. Qualys has worldwide team of engineers who constantly monitor and track RTI data points. This includes information on attacks, exploits and exploits kits. Qualys engineers also analyze this information to determine RTI attributes like lateral movement. Qualys has partnerships with companies like CORE Security, Immunity Inc, TrendMicro and others from which information is obtained and correlated.
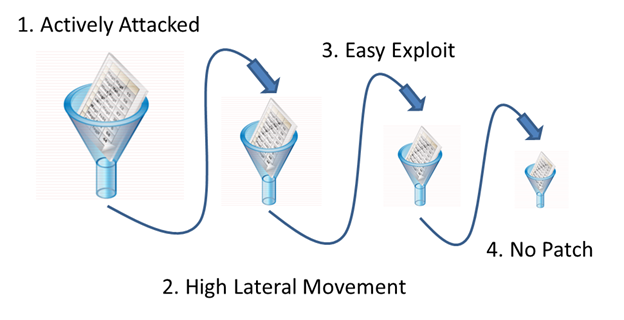
Real-time Threat Indicators can be used in multiple ways. They can be used standalone or can be used as filters that can be cascaded with each other. For example if Bob has 10,000 QIDs detected in his organization he can prioritize his efforts by cascading multiple RTIs and provide workarounds or alternate defenses since patches are not available, but the vulnerabilities are actively attacked, have a high lateral movement potential and the exploit is easy.
Prioritization using 4 example Real-time Threat Indicators Show me
Absolutely and we are in the process of creating some more Real-time Threat Indicators now.