Search Vulnerability Details
Our Vulnerabilities tab gives you an integrated, incremental search and browse experience to help you find all about your assets.
Choose Vulnerability to display vulnerability data (like we did here), or Asset for asset data. You can easily browse the data list and explore details. For example click the QID 105170 to view details for that vulnerability.
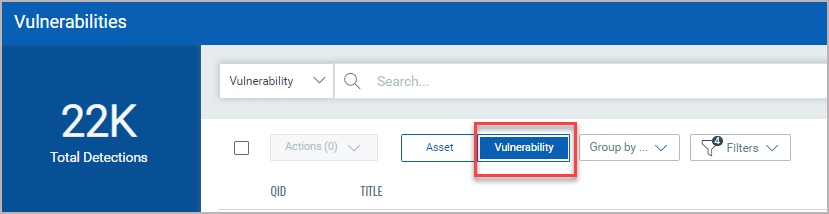
The Group By option help you organize your data. For example you can select Group By Severity then click any value listed in Detection Count column to view the list of assets that have the assigned severity.
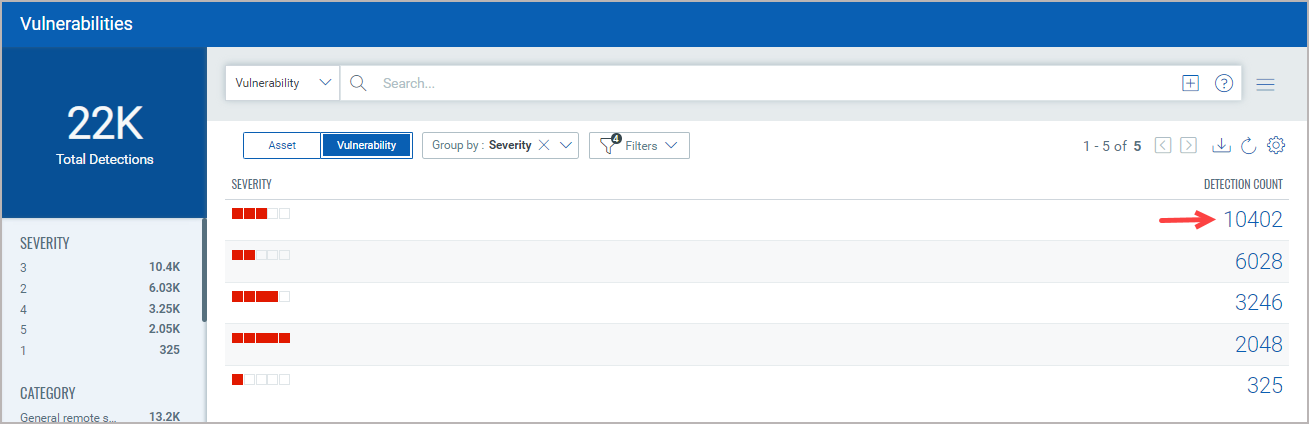
The Filters option lets you choose the type of vulnerabilities to filter the vulnerabilities further.
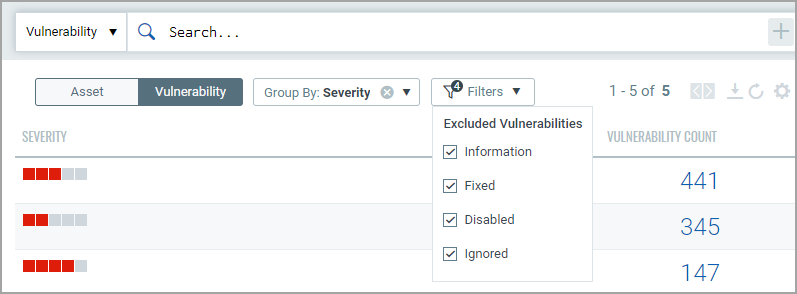
You will get a listing of severity 5 vulnerabilities. Notice the query selector shows your query.
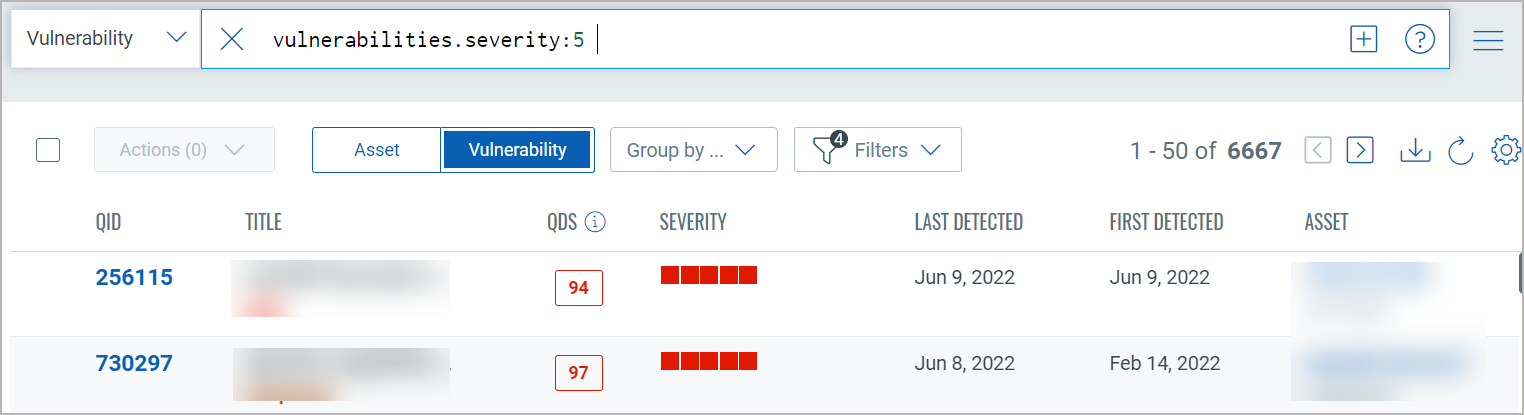
You will notice now you have fewer total vulnerabilities (in this case 68) Use the metadata filters on the right to narrow your search further. For example select Windows 2012
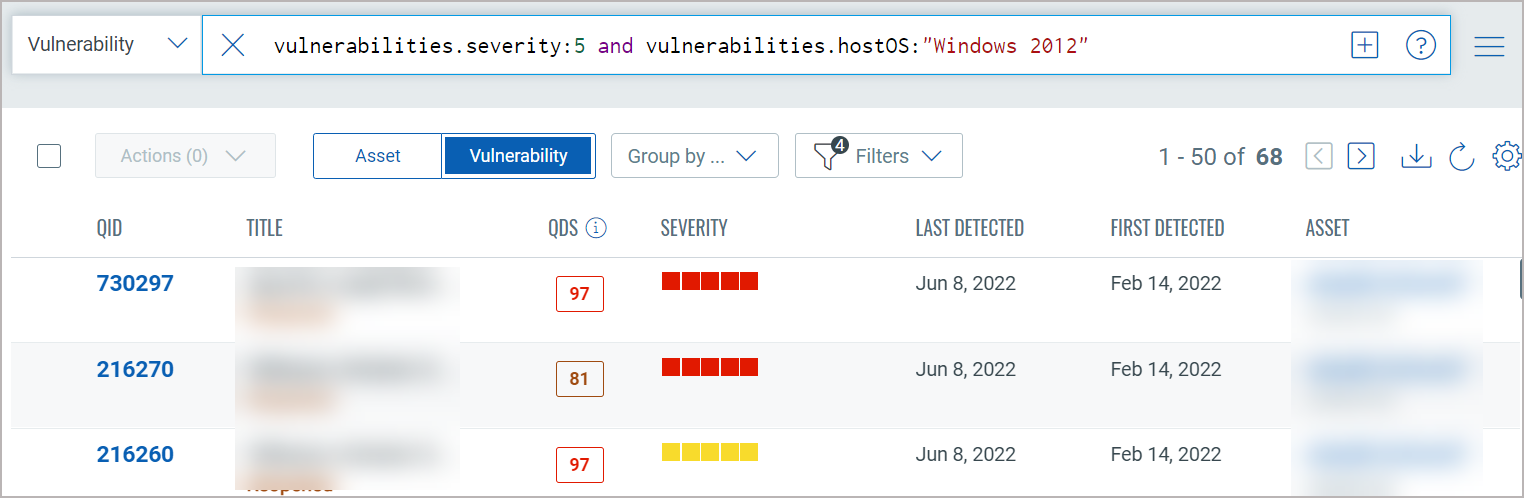
Using the query box you can add more query logic. For example say you want to see only New vulnerabilities. Just type "and" then start typing "status". Pick the token name vulnerabilities.status. Choose the token value ACTIVE and view syntax help on the right to help you form your query. Hit return to run the query when you're ready.
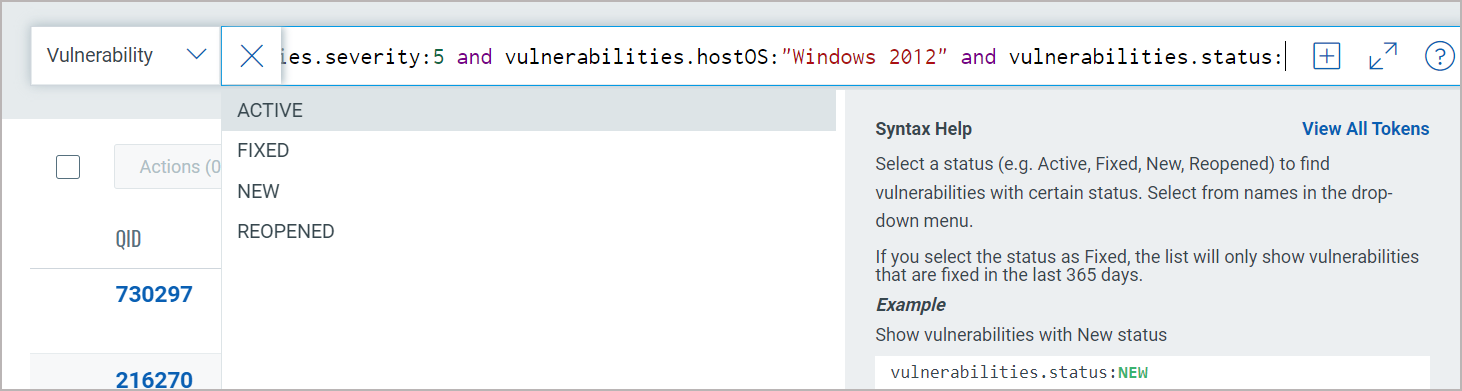
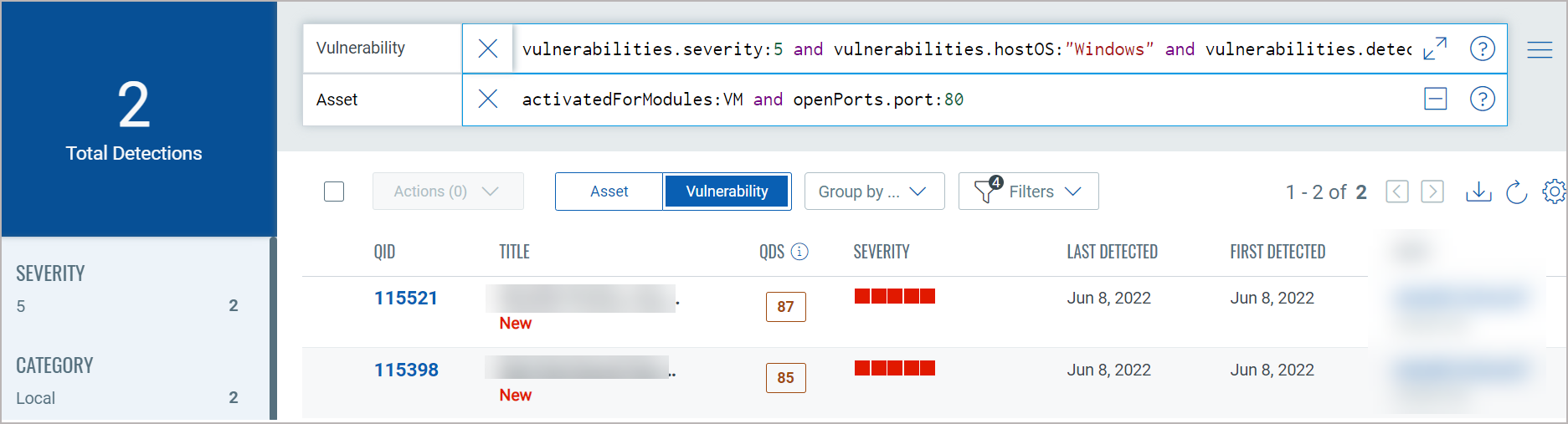
Easily add another query by clicking  . This way you'll search
the vulnerability index and the asset index. The queries in the 2 boxes
uses the AND operator together. Hit return when you are ready to run the
queries. Our sample queries further narrowed results and we have 2 total
vulnerabilities.
. This way you'll search
the vulnerability index and the asset index. The queries in the 2 boxes
uses the AND operator together. Hit return when you are ready to run the
queries. Our sample queries further narrowed results and we have 2 total
vulnerabilities.
Using our advanced search capabilities you can easily create robust queries using the many available search tokens. Looking for help with how to search? Click here
Using our ![]() search action menu options, you can view the frequently-used QQL queries,
save, and manage them with ease. You can create widgets from frequently
used queries for easy reference in future. Looking for the different actions
on the search queries, see Search
Actions.
search action menu options, you can view the frequently-used QQL queries,
save, and manage them with ease. You can create widgets from frequently
used queries for easy reference in future. Looking for the different actions
on the search queries, see Search
Actions.
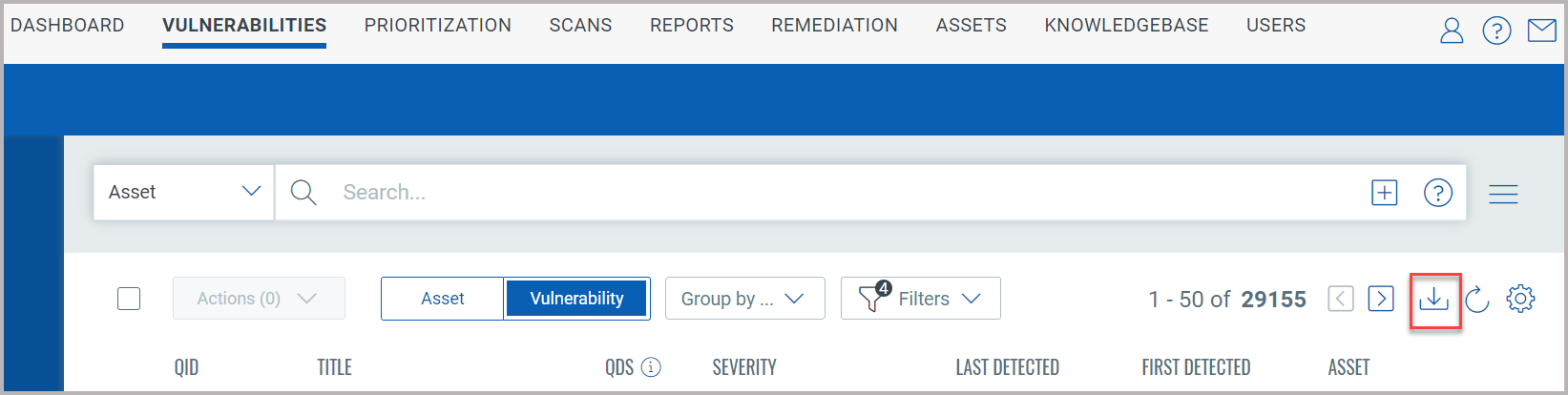
You could also export the search results to your local system and share
them with other users. You can export results in CSV format. It just takes
a minute to export search results. Click the download ![]() button.
button.
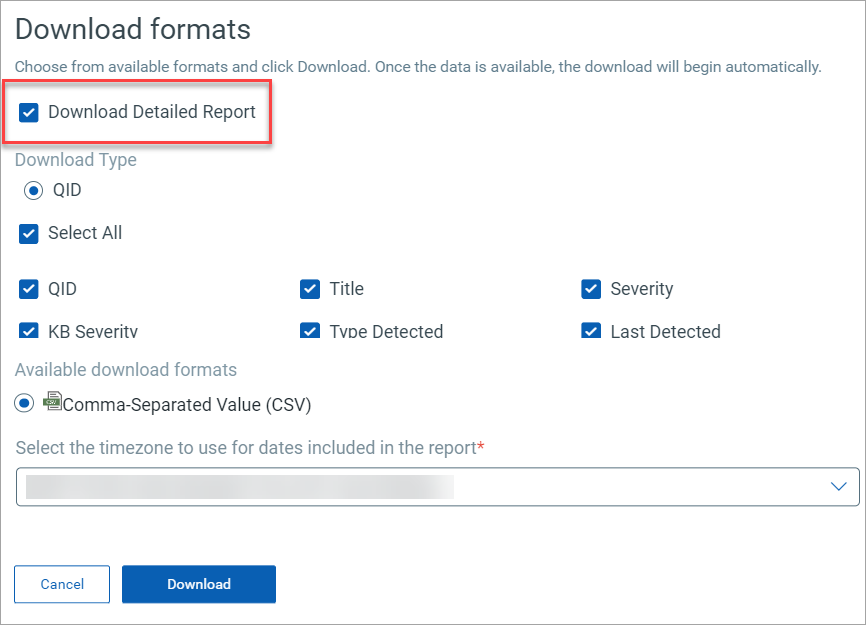
You can download vulnerability data based on CVE or QID. Additionally, based on the data you want to download, you can select specific check boxes.

Contact Qualys Support if the CVE and QID options are not displayed in the Download formats window.
Click Download. The details are downloaded in CSV format.
Using the Group by Vulnerability option to download the vulnerability data, you can only download the data based on selected QID fields. The report contains the asset data on which the QID is detected.
The download is limited to 10,000 vulnerability records.