Configure a Ruleset
A ruleset is a set of rules that tells us which events you want to be alerted on.
Go to Configuration > Rulesets to tell us which events you want to be alerted on. You can monitor changes to hosts, vulnerabilities, tickets, ports, and certificates.
Permissions
The Manager role has all the permissions to create, edit, view, and delete rulesets. The Reader, Unit Manager, and Remediation user roles have permission to view rulesets.
How do I add rules to the ruleset?
It's easy. Choose a rule type on the left, drag it to the right, and then set the rule criteria. Be as specific as you want when setting rule criteria. For example, you may want to be notified of all new vulnerabilities or only new vulnerabilities on Windows hosts with a patch available. For some rule criteria, you can choose the option "Matches RegEx" and then provide a regular expression to match. To make a regular expression match case insensitive, include (?i) at the start of the regular expression. See sample rules below.
AND is used within a rule. For example, get an alert for a vulnerability that matches: New, Reopened status AND severity 5 AND has a patch.
OR is used between multiple rules. For example, get an alert for a newly opened port, expired certificate, OR new host.
OR is used between multiple Threat Protection RTIs (when available in your subscription). For example, get an alert for a vulnerability that matches Zero Day OR Public Exploit.
Sample Rules
Check out these examples to get some ideas:
Sample 1 - PCI vulnerabilitiesSample 1 - PCI vulnerabilities
In this example, alerts will be generated when we detect new or reopened vulnerabilities that need to be fixed to maintain PCI compliance.
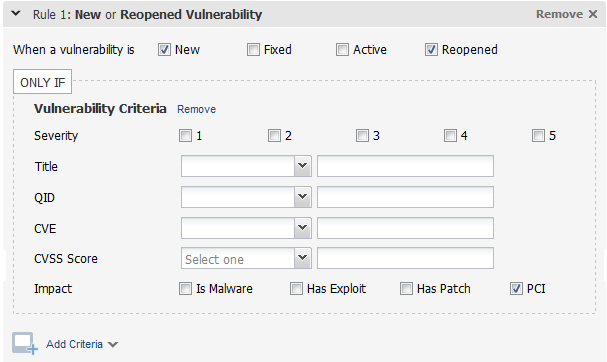
Tip - Click the Add Criteria link to further customize this rule. For example, add host criteria to tell us the type of hosts this rule applies to.
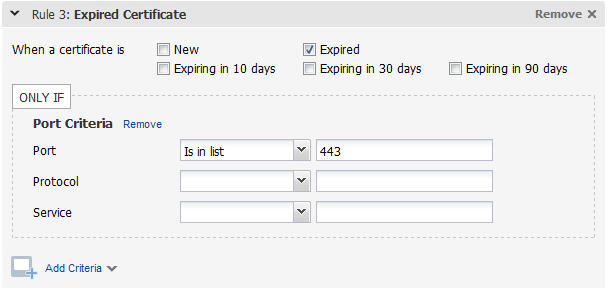
Sample 2 - Expired certificatesSample 2 - Expired certificates
In this example, alerts will be generated when we detect an expired certificate on a host with port 443 open. We evaluate certificate rules daily to find expired and expiring certificates. This is the only rule type not based on scans. (Tip - You could also create a Port rule and add certificate criteria to it. In that case, you will get alerts based on scans.)
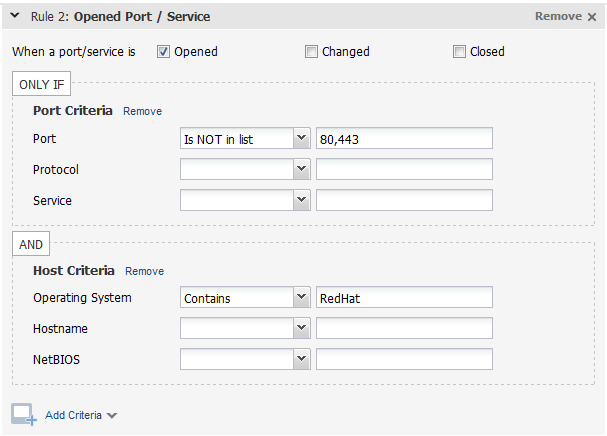
Sample 3 - Open ports on Linux hostsSample 3 - Open ports on Linux hosts
In this example, alerts will be generated when any port except 80 or 443 is opened on a Linux host.
Sample 4 - FTP running on a non-standard portSample 4 - FTP running on a non-standard port
In this example, alerts will be generated when we detect that FTP is running but not on port 21.
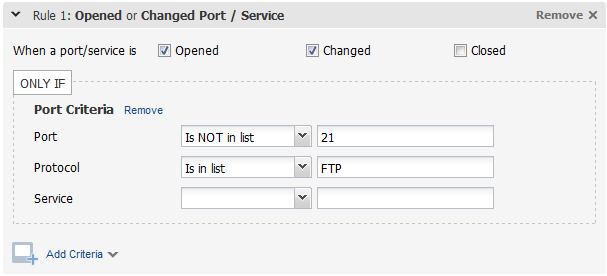
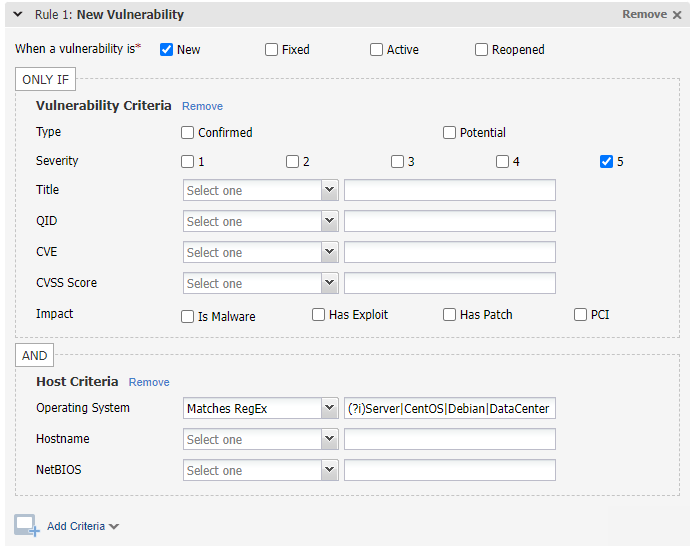
In this example, alerts will be generated when we detect new, severity 5 vulnerabilities on hosts with operating systems that match Server, CentOS, Debian or DataCenter. (?i) indicates that the regular expression is case insensitive.
Quick Links
Manage Your Rulesets | View Your Alerts | Threat Protection RTI