Create application in Azure Active Directory and you can then note the application ID.
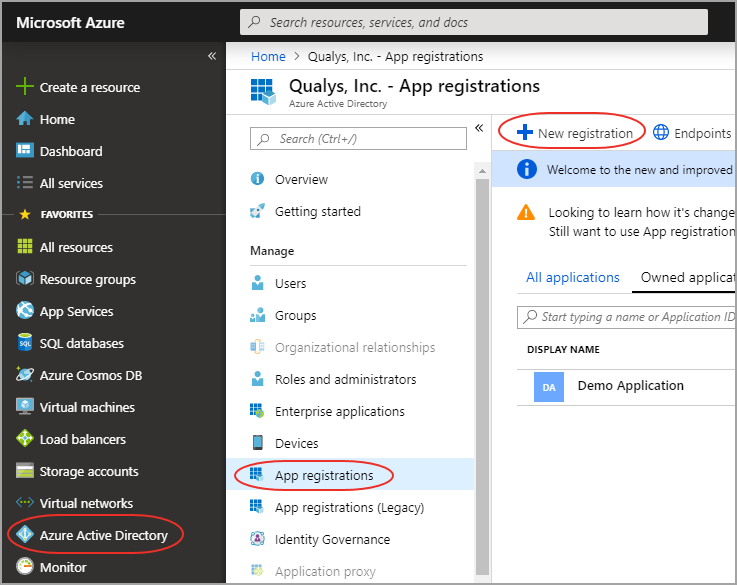
1 - Log on to the Microsoft Azure console and press Azure Active Directory in the left navigation pane. Show me
2 - Click App Registrations > New registration.
3 - Provide the following details:
a. Name: A name for the application (For example, My_Azure_Connector)
b. Supported account types: Select Accounts in any organizational directory.
4 - Click Register. The newly created application is displayed with its properties. Copy the Application (client) ID and Directory (tenant) ID and paste it into the connector details. Show me
Provide permission to the new application to access the Windows Azure Service Management API and create a secret key.
1 - Select the application that you created and go to API permissions > Add a permission.
2 - Select Azure Service Management API in Microsoft APIs for Request API permissions. Show me
3 - Select user impersonation permission and click Add permission. Show me
1 - Select the application that you created and go to Certificates and Secrets > New client secret.
2 - Add a description and expiry duration for the secret key (recommended: Never) and click Add. Show me
3 - The value of the key appears in the Value field.
Copy the key value at this time. You won’t be able to retrieve it later. Paste the key value as Authentication Key into the connector details. You need to provide the key value with the application ID to log on as the application. Store the key value where your application can retrieve it.
Grant permission for the application to access subscriptions. Assign a role to the new application. The role you assign will define the permissions for the new application to access subscriptions.
1 - On the Azure portal, navigate to Subscriptions. Show me
2 - Select the subscription for which you want to grant permission to the application and note the subscription ID. To grant permission to the application you created, choose Access Control (IAM).
3 - Go to Add > Add a role assignment. Pick a Reader role. A Reader can view everything, but cannot make any changes to the resources of a subscription.
Note: You need to assign the Reader role if
the same application is used in AssetView and CloudView module. If the
application usage is limited to only AssetView module (and not in CloudView
module), you need to have at least below permissions on the built-in or
custom role assigned to the subscription.
- "Microsoft.Compute/virtualMachines/read",
- "Microsoft.Resources/subscriptions/resourceGroups/read",
- "Microsoft.Network/networkInterfaces/read",
- "Microsoft.Network/publicIPAddresses/read",
- "Microsoft.Network/virtualNetworks/read",
- "Microsoft.Network/networkSecurityGroups/read"
4 - Select Azure AD user, group, or application in Assign Access to dropdown.
5 - Type the application name in Select drop-down and select the application you created. Show me
6 - Click Save to finish assigning the role. You’ll see your application in the list of users assigned to a role for that scope.
7 - Copy the subscription ID you noted and paste it into the connector details in the Qualys Azure Connector screen and then click Create Connector.