User Roles and Permissions for Patch Management
Role Based Access Control gives you flexibility to control access to Patch Management features based on the roles of the individual users.
Each user is assigned a pre-defined user role which determines what actions the user can take.
We have 5 OOTB (Out-of-the-box) roles for PM users. Each role, except Patch Security, is an incremental role to the previous one.
1) Patch Reader: This is the default role designed to most (sub-)users, present in the system today, with minimum permissions possible. This role is granted to allow users viewing/ read-only capabilities in the Dashboards developed to provide an insight into the Patching operations. This role has only view permissions on assigned jobs, assessment profiles, and dashboards.
2) Patch Dashboard Author: This is a special role that would be needed only for larger organizations that delegate development of dashboards to a dedicated team especially, one that does NOT operate/ manage the patching jobs. This role includes all the Patch Reader permissions.
3) Patch User: This role is designed for the operators of the Patching job, who interact and manage patching activities on a regular basis. In most cases, these users will also build dashboards for reporting information to their respective department/ team. This role includes all the Patch Dashboard Author permissions.
4) Patch Security: This role is mutually exclusive to all the earlier set of roles. It is meant for the Security Expert in organizations where IT operations and Security operations (SecOps) are owned by distinct team. These users have very limited capabilities that allow them to pass on a list of selective patches to the IT operations team to operationalize their patching on the endpoints across the organization. All the job advisories created by Patch Security user are "Partially Configured Job" and only after assigning these jobs to a Patch User/ Patch Manager, the owners can choose the right tags/ assets, schedule and other options. Only the Patch Manager role has "Change Owner” permission enabling it to take/ assign ownership of a “Partially Configured Job” to other users, with Patch Manager or Patch User roles. These users can neither own nor edit/co-edit any job.
5) Patch Manager: A Patch Manager has all the permissions except the Create Job Advisory permission.
For Patch Management, we refer to the Global Dashboard Permissions to determine what operations the user can perform on Unified Dashboard. The Global Dashboard Permissions will only allow the Patch Manager, Patch User, and Patch Dashboard Author to create, edit and delete their own Our earlier RBAC model, was more restrictive enforcing a clear compartmentalization of users from each other and basic roles only. With the new RBAC model, we have added more roles, depicting the real-life hierarchies and responsibilities. With the upgrade of the RBAC model, all existing subdashboards. For permissions to edit, delete other users' dashboard and print/download dashboard, contact SuperUser or Administrator.
- users will take the Patch User role and all the existing super-users will have all the permission defined in RBAC. All other roles will need to be explicitly managed by the super-user.
Also note, that these roles are exclusive to the Patch Management module only. The roles defined in other modules have NO correlation with that defined in Patch Management.
We recommend users to NOT create custom roles for the Patch Management users by assigning or unassigning permissions available through the default roles. Such customization of roles or change of permissions may lead to user roles not working as per the design.
Job Sharing with other users
A job can be shared with other users by making them co-authors of the job, allowing them to edit/operate the job equivalent to the creator, provided they have the same (or higher) role and same (or larger) asset scope assigned to them for administration. See Jobs to deploy Patches on Assets/Roll Back Patches From Assets to assign co-authors to a job.
Note that co-authors of a job do not have permission to add/remove assets to/from the job but they can add/remove asset tags to/from the job. Though co-authors of a job can add an asset tag to the job, only the assets that are in the owner's asset scope will be picked up when the job is run. Remember that execution of a job is restricted by the tag scope of the job owner.
.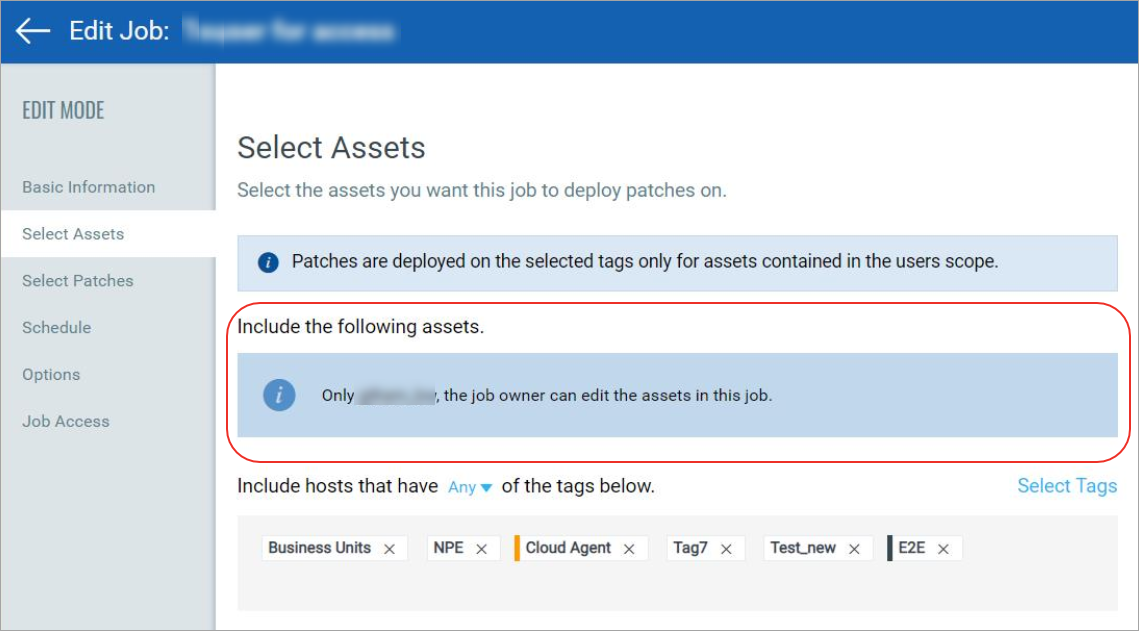
By default, only Patch Managers have complete asset scope, meaning only they can manage every asset of the organization. All other users need to be explicitly granted asset scope with the help of tags. Dynamic tags are generally the best choice, to ensure automatic tag scope changes as assets are added to/ removed from the system.
Partially Configured Job
Patching Job has 3 critical components:
a) Patch(es): One or more patches to be applied as a part of the job.
b) Asset(s)/ Tags: One or more assets on which the patches are to be applied. A logical collection of assets is referred to as Tags.
c) Schedule: The Patching job needs to be executed at a scheduled date and time. In case of a recurring Patching job, each job run is scheduled for a selected time, at a frequency across selected dates/ days of a month.
All these 3 components are important for the completeness of a job. If any of them is pending in a job definition, we have a Partially Configured Job.
The “Patch Security” role is restricted to defining only the first component i.e. Patch list of a job. This ensures that the security advisors leave the operational aspects at the discretion of the Patch Users. Other users who are permitted to create/ edit a job can also create Partially Configured Jobs. A job can be executed only when it is Fully Configured.
Apart from the above 3 mandatory components, a Fully Configured Job could also have some other options.
How to find PM Roles and view their permissions
You can assign roles from our Administration utility module. Within the Administration utility, you'll find roles and their related permissions in the Role Management section. See Qualys Administration utility Online Help.
1) From the application module picker, click Administration.
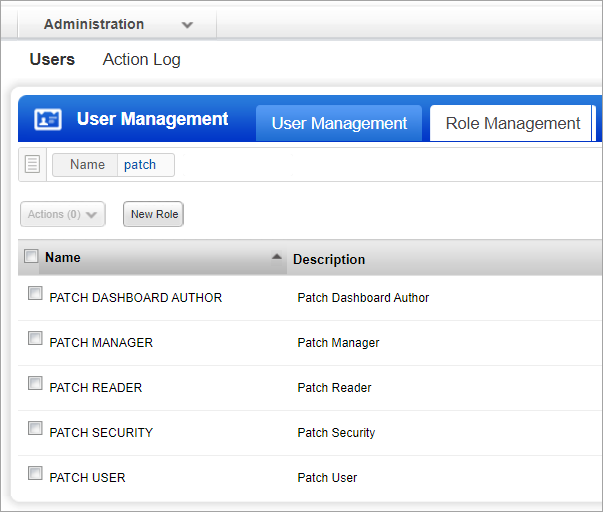
2) Go to the Role Management tab and enter "patch" in the search box to view all the patch management roles.
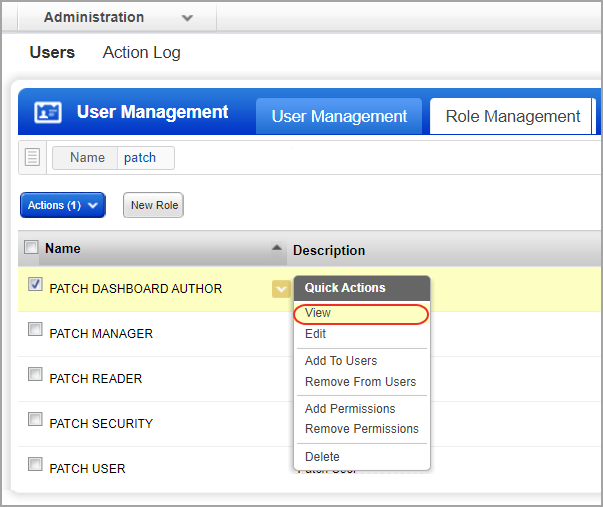
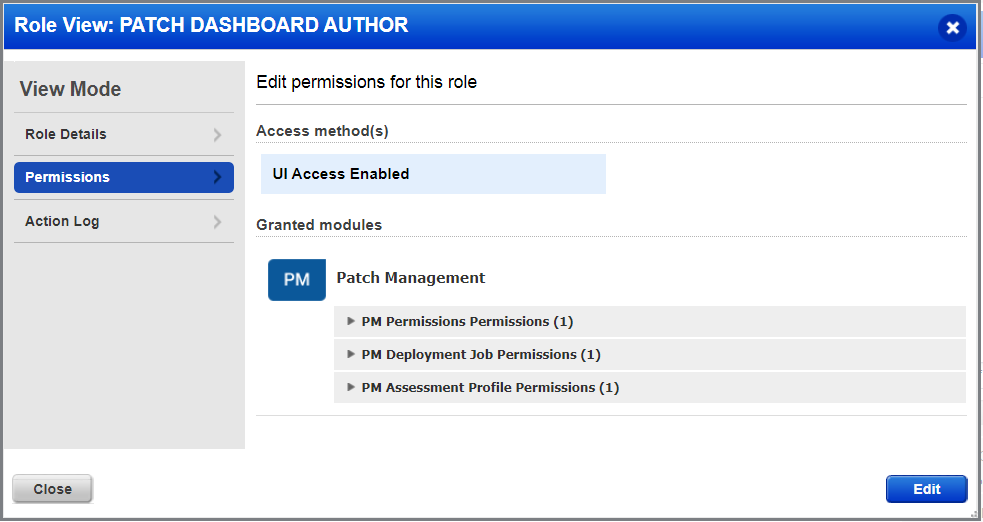
3) Select a role from the list and from the Quick Actions menu, click View.
4) On the Roles View screen, go to the Permissions tab to view the permission for the selected role.
How are tags used to grant access to assets?
An asset tag is a tag assigned to one or more assets. Tag scopes define what assets the user can view when creating a job or when user go to Assets tab in patch management. Assigning a tag to an asset enables you to grant users access to that asset by assigning the same tag to the users scope. Want to define tags? It's easy - just go to the Asset Management (AM) application.
To assign asset tags to the user,
1) Go to the Administration module and then from the User Management tab search a or select the user.
2) From the Quick Actions menu, click Edit.
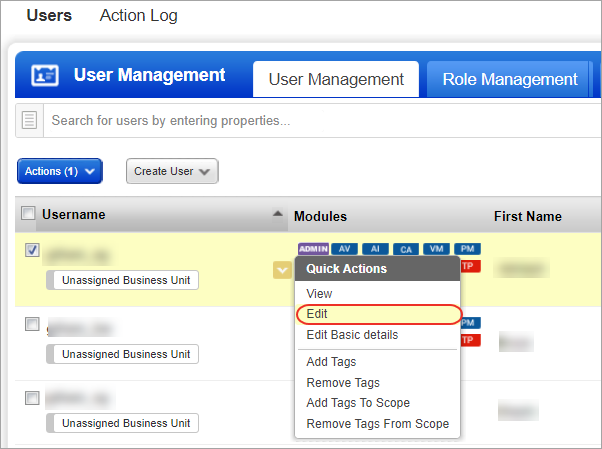
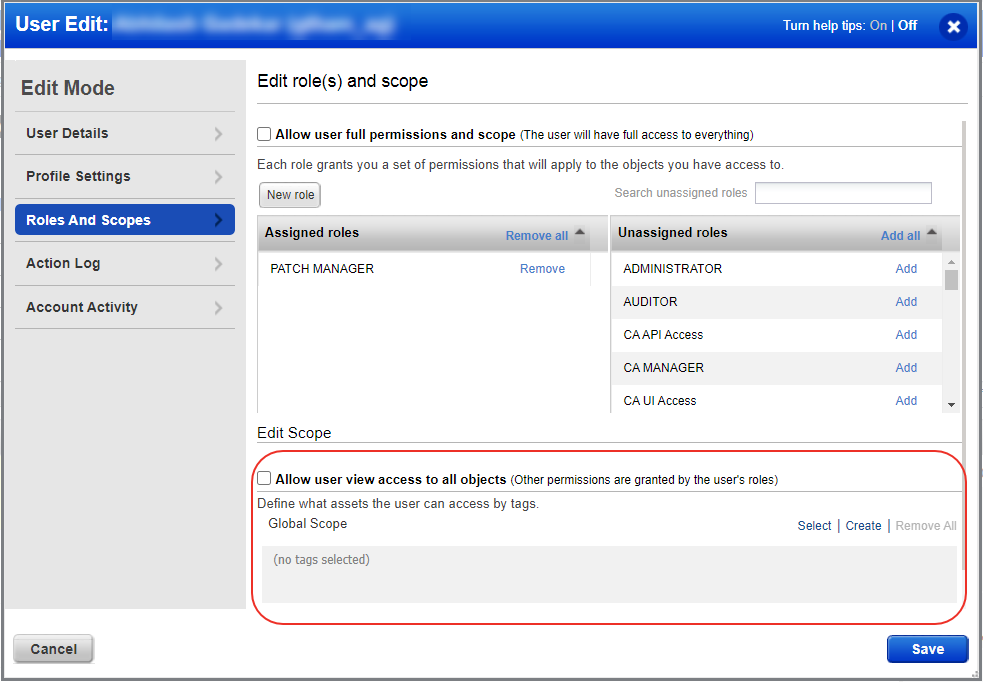
3) On the User Edit screen, go to the Roles and Scopes tab.
4) In the Edit Scope section, select one or more asset tags that you want to assign to the user. Then click Save.
User Roles Comparison
The following table provides a comparison of privileges granted to user roles for Patch Management. Note that Assigned Jobs of a user are the jobs that the user has created or permission to edit as a co-author.
|
Privileges |
Patch Manager |
Patch User |
Patch Dashboard Author |
Patch Reader |
Patch Security |
|
Manage License Permissions |
|
||||
|
Manage License |
Y |
||||
|
Assessment Profile Permissions |
|
||||
|
Create Profile |
Y |
||||
|
Edit Profile |
Y |
||||
|
Delete Profile |
Y |
||||
|
View Profile |
Y |
Y |
Y |
Y |
Y |
|
Deployment Job Permissions |
|
||||
|
Change Job Owner(ship) |
Y |
||||
|
View Any Job |
Y |
||||
|
Edit Any Job |
Y |
||||
|
Enable/disable any Job |
Y |
||||
|
Delete Any Job |
Y |
||||
|
Create job |
Y |
Y |
|||
|
Edit Assigned Job |
Y |
Y |
|||
|
Enable/disable Assigned Job only |
Y |
Y |
|||
|
Add Remove Patches on Assigned Job only |
Y |
Y |
|||
|
Delete Assigned Job only |
Y |
Y |
|||
|
View Assigned Job only |
Y |
Y |
Y |
Y |
Y |
|
Global Dashboard Permissions |
|
||||
|
Create, Edit, Delete your own dashboards |
Y |
Y |
Y |
||
|
Edit Dashboard |
|||||
|
Delete Dashboard |
|||||
|
Print/Download Dashboard |
|||||
|
Advisory Permissions |
|
||||
|
Create Job Advisory |
Y |