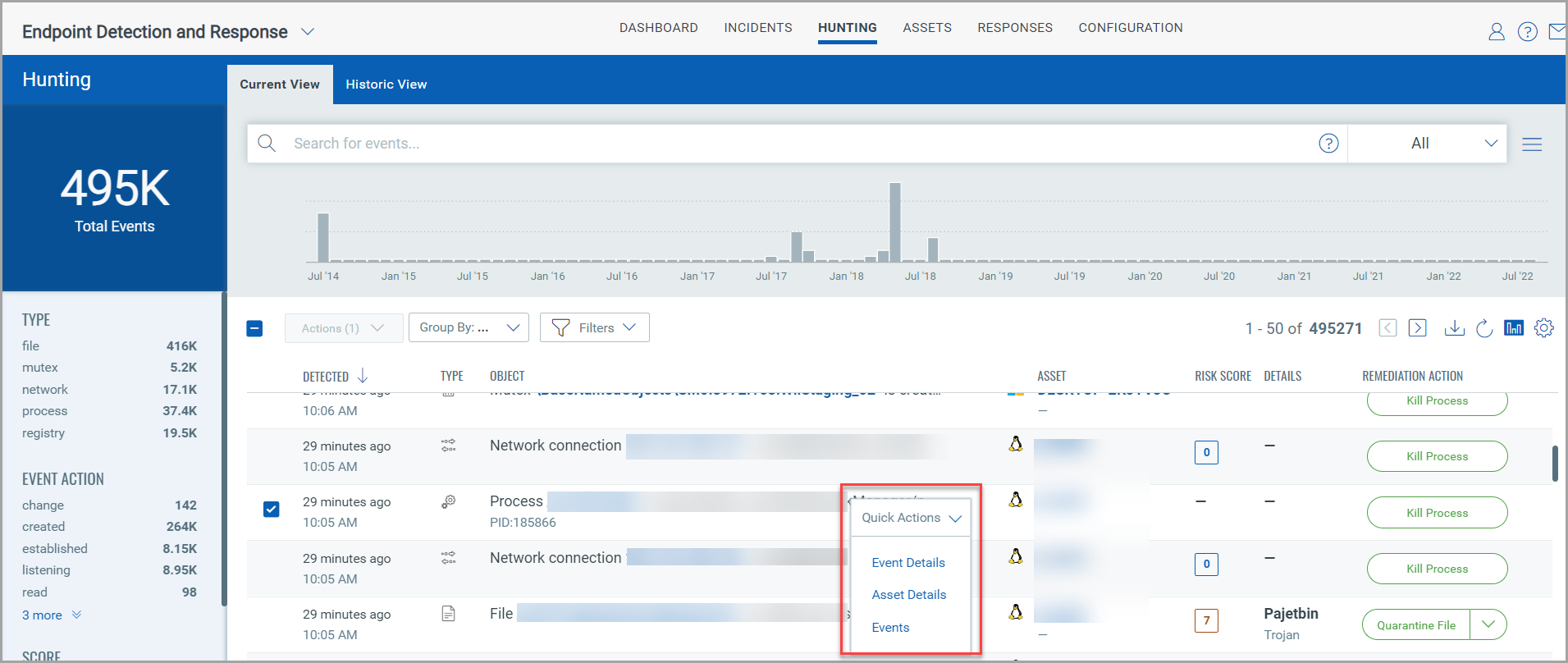
The Event Details page lists information about all the events. In the Hunting tab, to view the Event Details choose any event and from the Quick Actions menu click Event Details.

From the Event Details page, you can perform the remediation actions (Quarantine File/ Delete File/ Kill Process) on File, Mutex, Network, and Process events. For more information on remediation action, see Remediation.
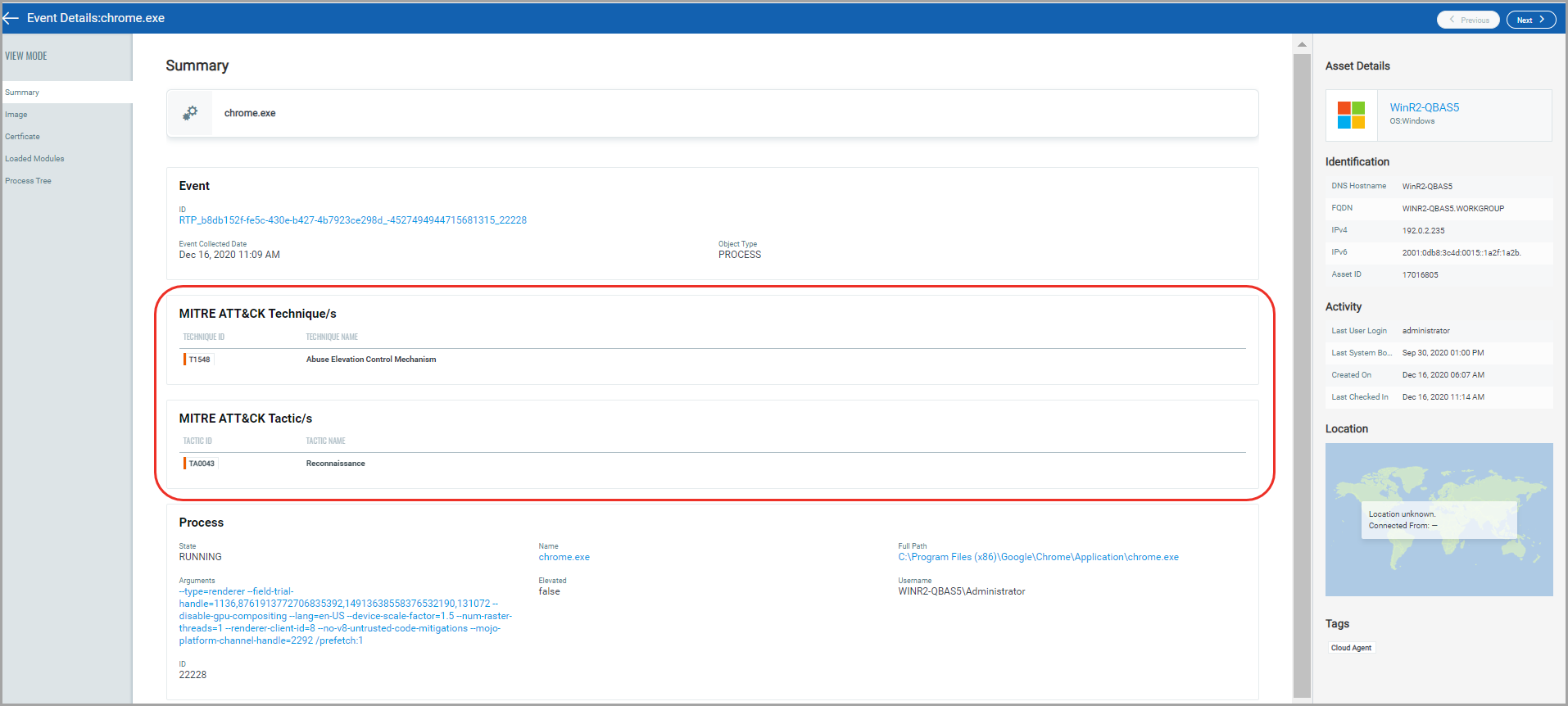
MITRE ATT&CK defines the tactics, techniques, and procedures that are leveraged by adversaries and malware. EDR helps detect malicious behavior on the endpoint by evaluating the events in context with MITRE ATT&CK.
Events registered on the agents are analyzed, and appropriate ATT&CK tactics and techniques are applied on the Event Details page.
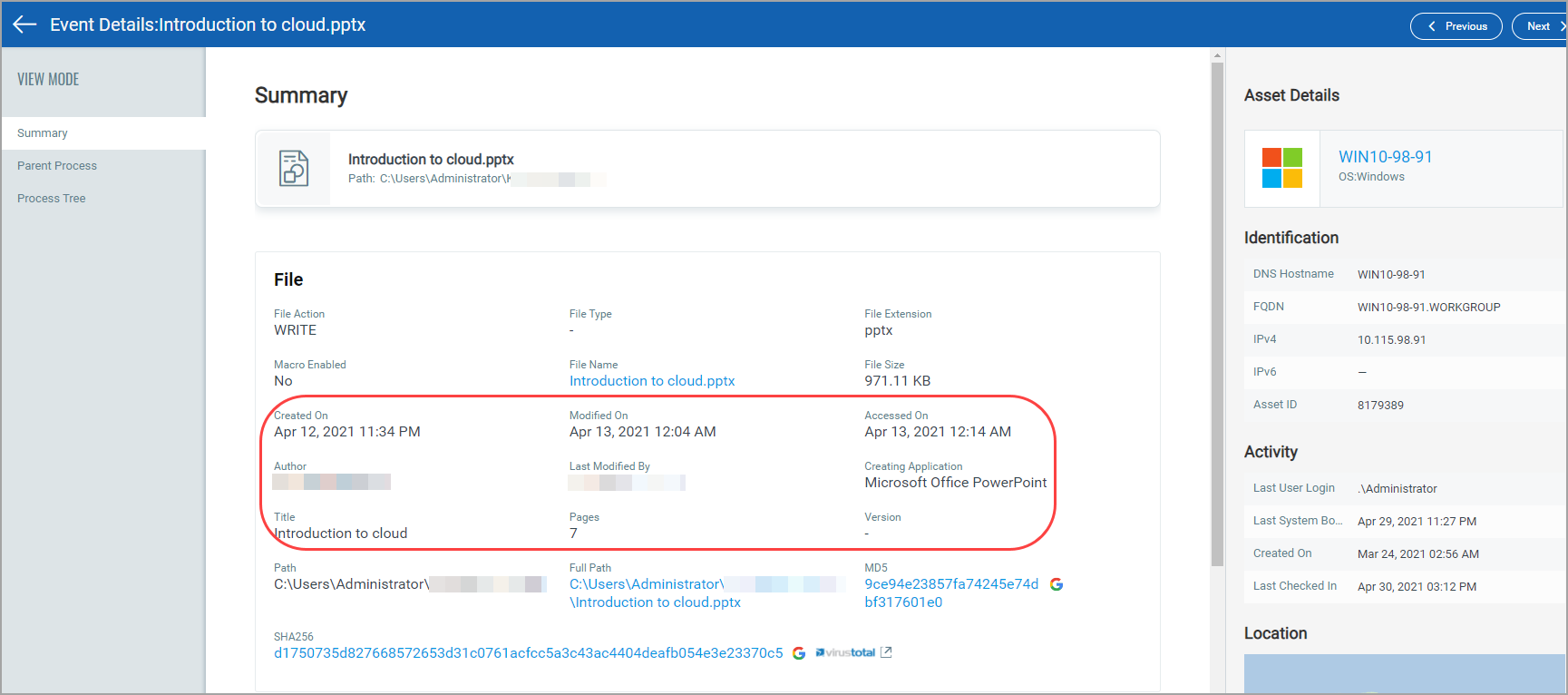
All the detected non-Portable Executable (non-PE) files are listed in the Current View of the Hunting tab. Navigate to a non-pe file and in the event details section you can view the details of the file as well as Parent Process and Process Tree details.
For example if it is a .pptx file, you will view the following details in your event details Summary:
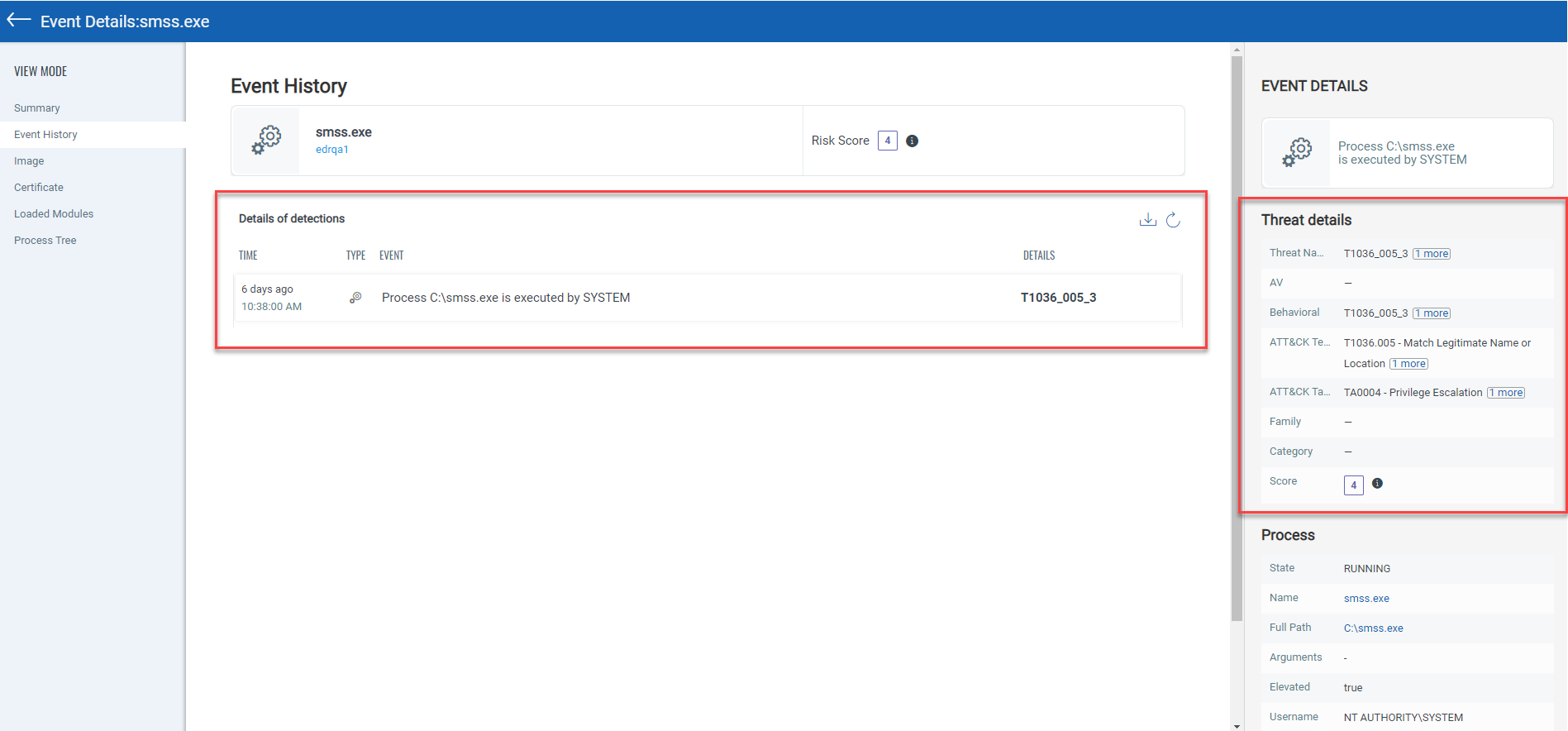
Click Event Details > Event History tab to view the detection history of the events. You can view the Threat details, the score which is assigned based on the detection engine and so on. The list shows 50 most recent events for the File, Process, Mutex, Registry, and Network events. You can refresh the list of events or download the event history in a CSV file. The Delete File, Quarantine File, and Kill Process options are shown only if the event is malicious type. To view details about each event, just click the individual event entry.
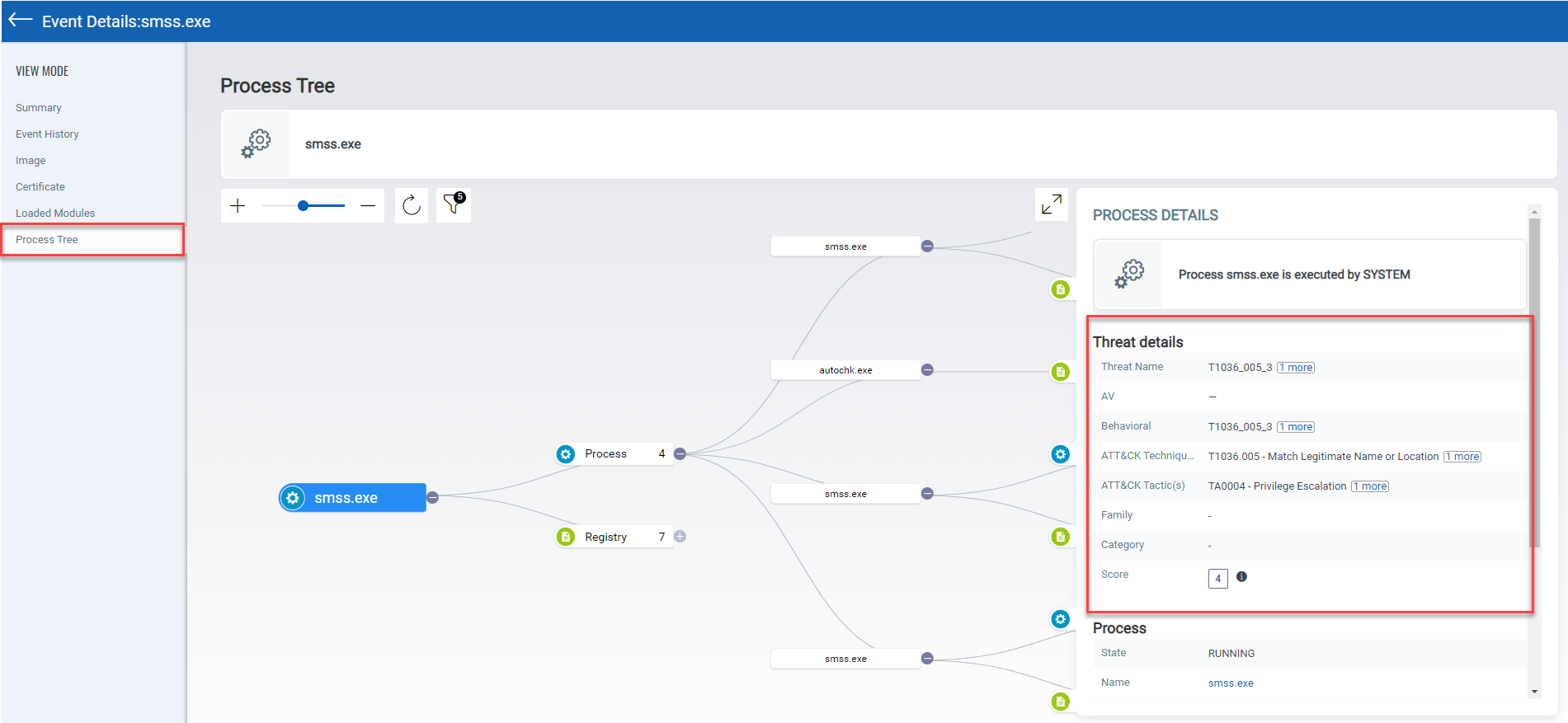
Click Event Details > Process Tree tab, to view the process tree for File, Process, Mutex, Registry, and Network events. The process tree displays all the related events of the selected event.
An event of the “Process” type will show its parent and child processes along with the mutex and network connection of the process. For the event of Network type, you see network connection of a process and for the event of Mutex type, mutex connection of a process.
In the process tree view, the selected event node is highlighted with the blue color. You can traverse between the nodes by clicking a node in the hierarchy. You can click on the (+) and (-) to expand and collapse the tree nodes and display the related events.
You can click on the event node to view the details of the selected node in the right pane. To help you identify event types of nodes in a hierarchy view, similar events are grouped under an event type (example: Mutex or Network) and respective event icons are added against the node.
You can view the detection engine (Malware Detection, Yara rules, Behavioral Analysis, Threat Intelligence, etc.) for the event and the event risk score in the Threat details section.
Process tree view displays a zoom bar and reset option.