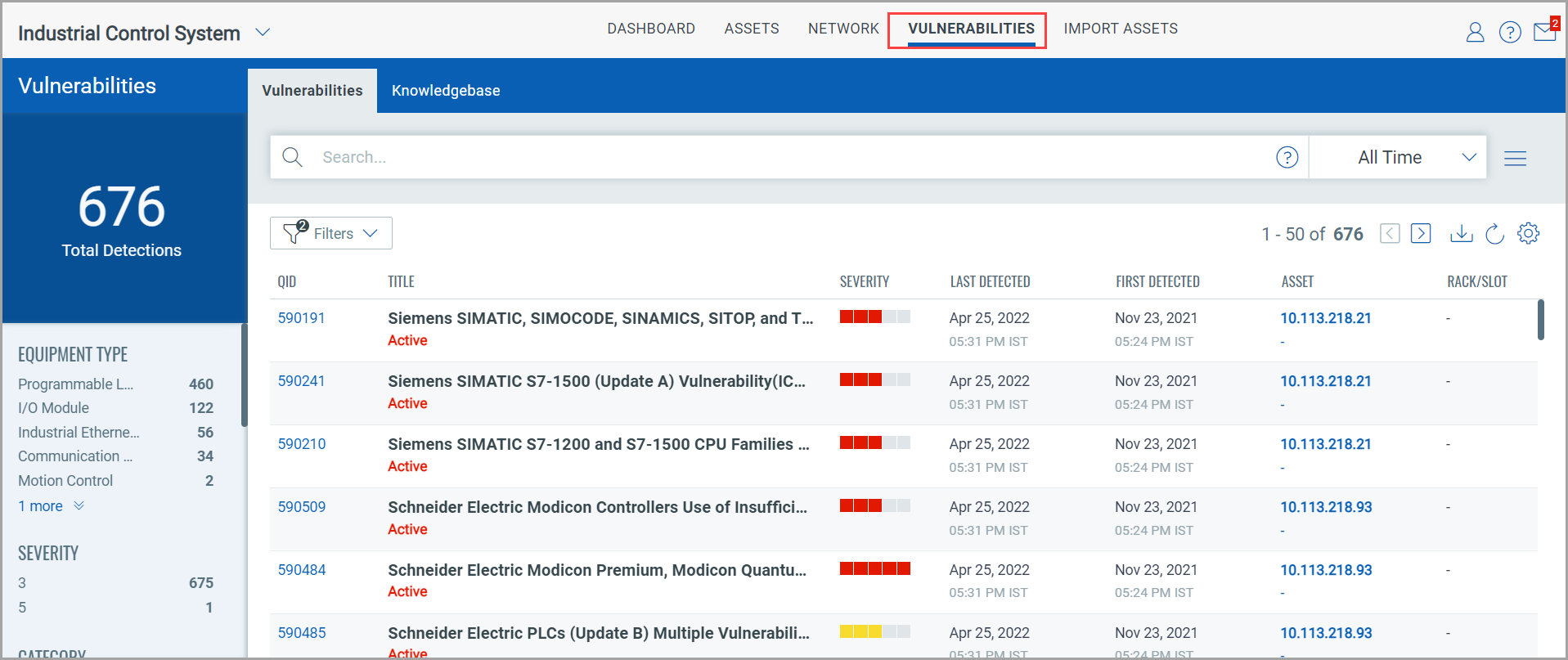
The Vulnerabilities tab gives you a complete view of vulnerability posture of the assets in your industrial network.

In the upper left corner, you see the total count of vulnerability detections in your network. These are the vulnerabilities detected by Qualys Network Passive Sensor.
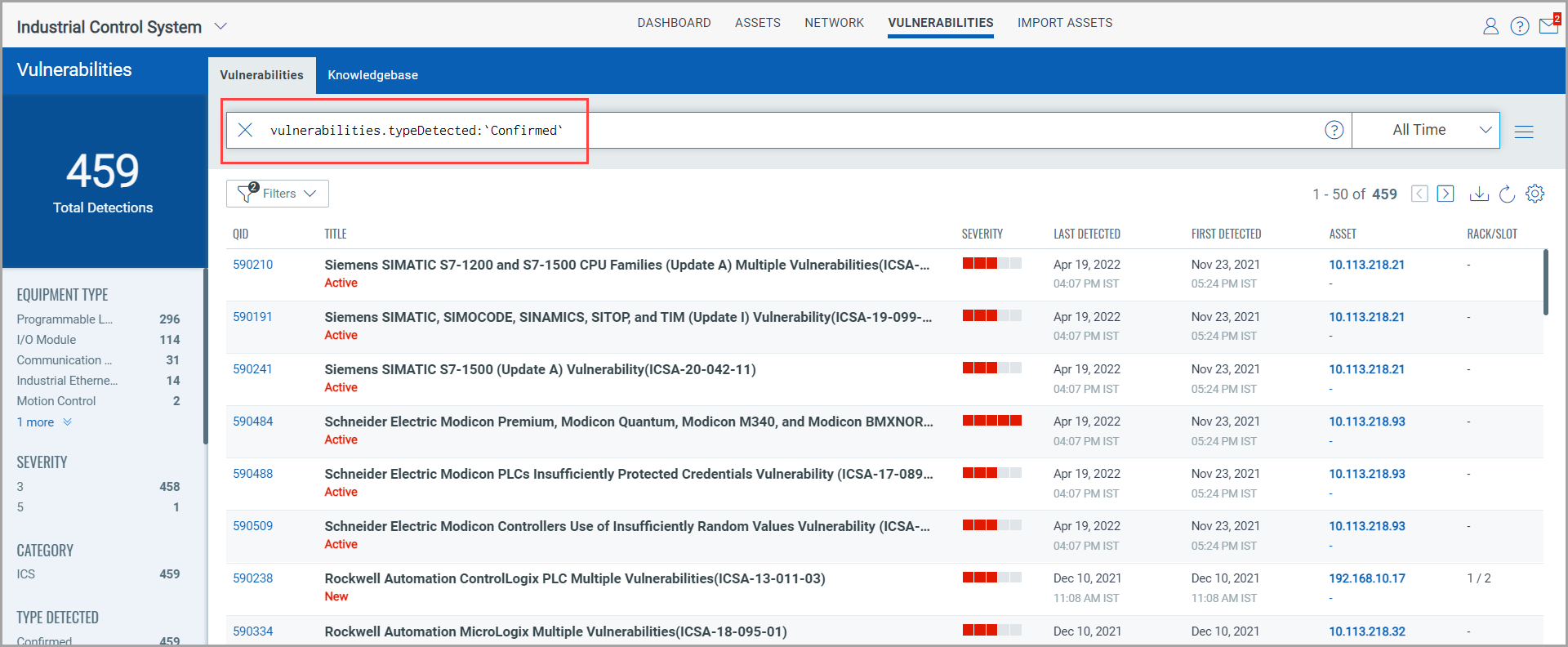
In the search bar, you can build QQL queries to narrow down the scope of your vulnerability search by using the supported search tokens. For more information, see Search Tokens for Industrial Control System.
Right below the total detections, you see vulnerabilities grouped into various categories. After you click a category in this list, your selection gets translated into a QQL query in the search bar and the vulnerabilities that fit into your selected category are displayed in the vulnerabilities table.
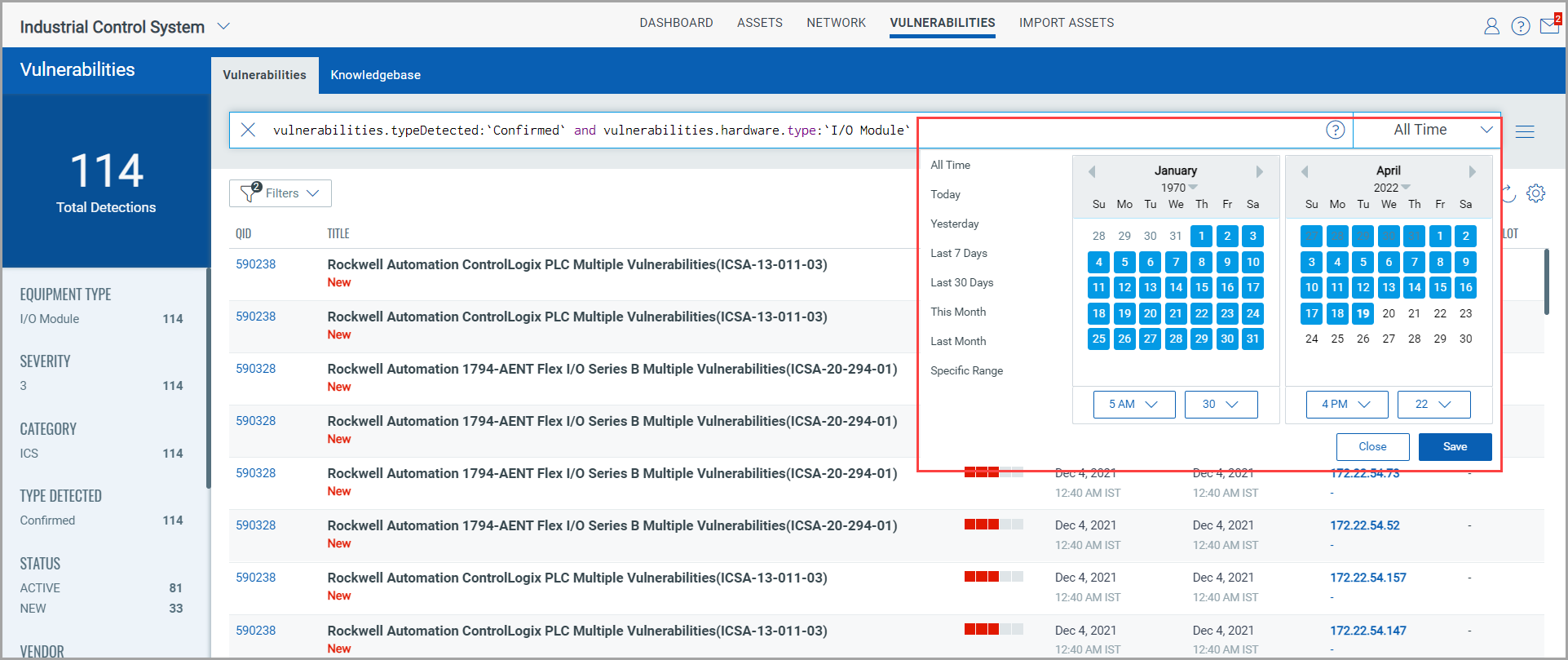
By using the date and time range picker next to the search bar, you can choose to view vulnerabilities detected within a specific time period.
The vulnerabilities table contains the list of detected vulnerabilities and their following details:
- QID, the unique Qualys ID assigned to the vulnerability - Vulnerability title - Severity level (1-5) determined by the security risk associated with its exploitation - When the vulnerability was last detected on the asset |
- When the vulnerability was first detected on the asset - Asset on which the vulnerability is detected - Rack/Slot details |
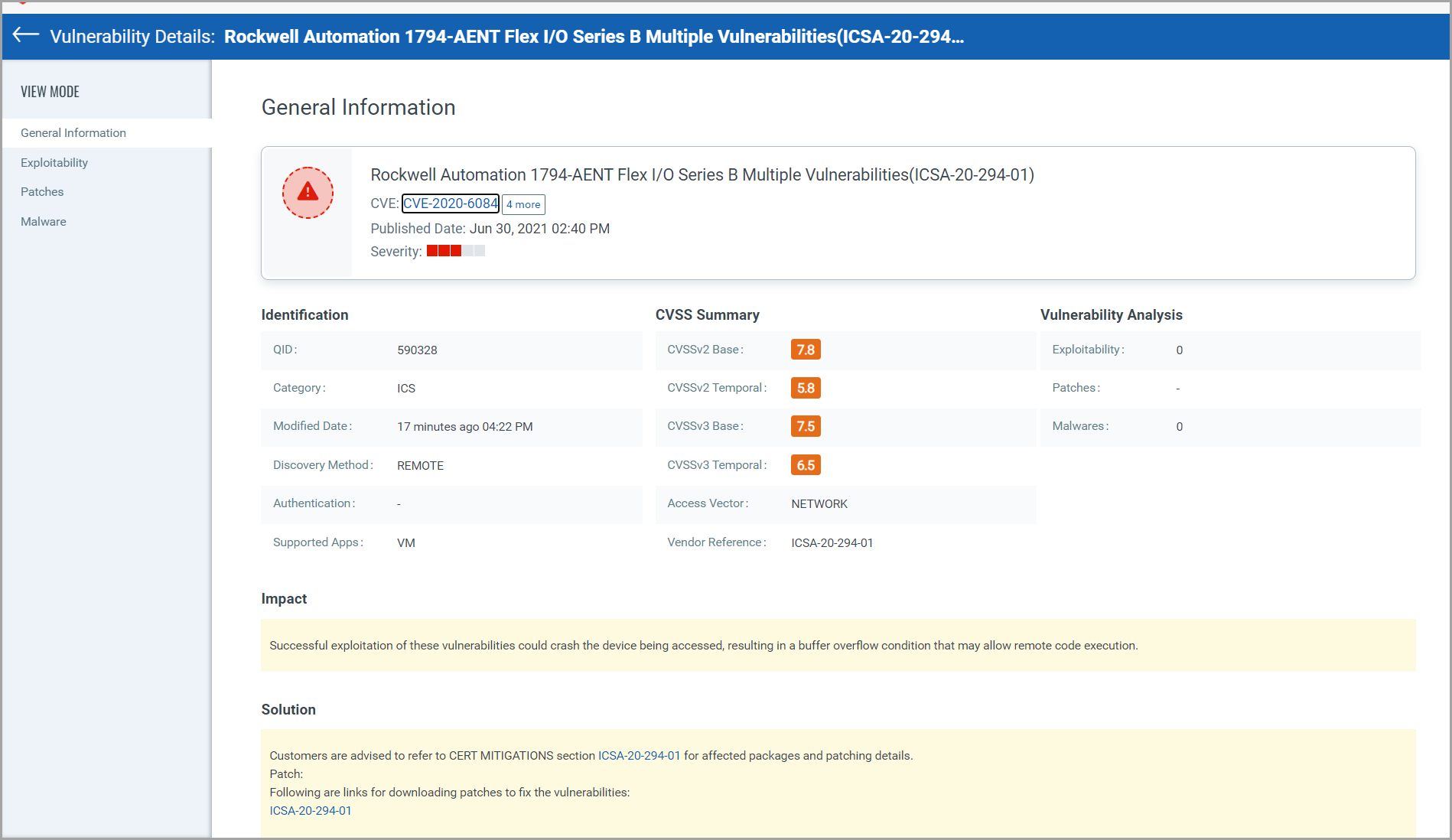
If you are interested in viewing granular details of a vulnerability, click the QID. On the Vulnerability Details page, you can view the detection summary, general information about the detected vulnerability, information about known exploits for the vulnerability available from third-party vendors and/or publicly available sources, available patches to fix the vulnerability and any published malware associated with the vulnerability.
To view details of a vulnerability, click the QID.
The detection summary and general information about the detected vulnerability are displayed on the Vulnerability details page. On the Vulnerability details page, information about known exploits for the vulnerability available from third-party vendors and/or publicly available sources, available patches to fix the vulnerability, and any published malware associated with the vulnerability is displayed.