Container Security Users and Permissions
The Qualys Container Security application uses a Role Based Access Control (RBAC) model to control access to Container Security features. With RBAC, each user is assigned a pre-defined user role which determines which actions the user can take in the UI and API.
About User Roles
A Manager user (superuser with full permissions and scope) can access the Administration utility, has all roles assigned, can add and manage users, can create custom roles and assign roles to users. The first user in a new customer subscription is a Manager user.
We have the following pre-defined roles for Container Security. These roles are exclusive to the Container Security module. The roles defined in other modules have NO correlation with those defined in Container Security.
CS Manager: A CS Manager has all Container Security permissions and can perform all actions in the Container Security UI and API. All Container Security users existing prior to the Container Security 1.17 release will be assigned the CS Manager role automatically, which means they can perform all actions.
CS User: The CS User role only has permission to access the Container Security UI, and has no other permissions assigned. Note: This role will not be available in new customer subscriptions created after Container Security 1.17.
How to View Roles and Permissions
Managers can view user roles and permissions from the Administration utility. If you need help at any time, please refer to the Qualys Administration Utility Help.
1) Choose Administration under Utilities from the application picker.
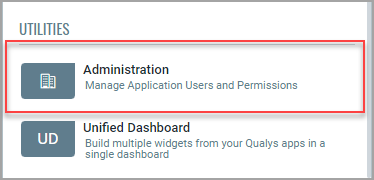
2) Go to the Users > Role Management tab. This is where you’ll find roles and their related permissions. You can search for the module “container security” to view the Container Security roles.
Note: The Role Management tab is only visible if you have a) full permissions and scope, or b) a role with the “Access Role Management Section” permission enabled.
3) Select View from the Quick Actions menu for any role in the list to see the permissions associated with the role, or Edit to make changes to the permissions.
Note: When you change the permissions for a role, all users with the role will be affected by the changes.
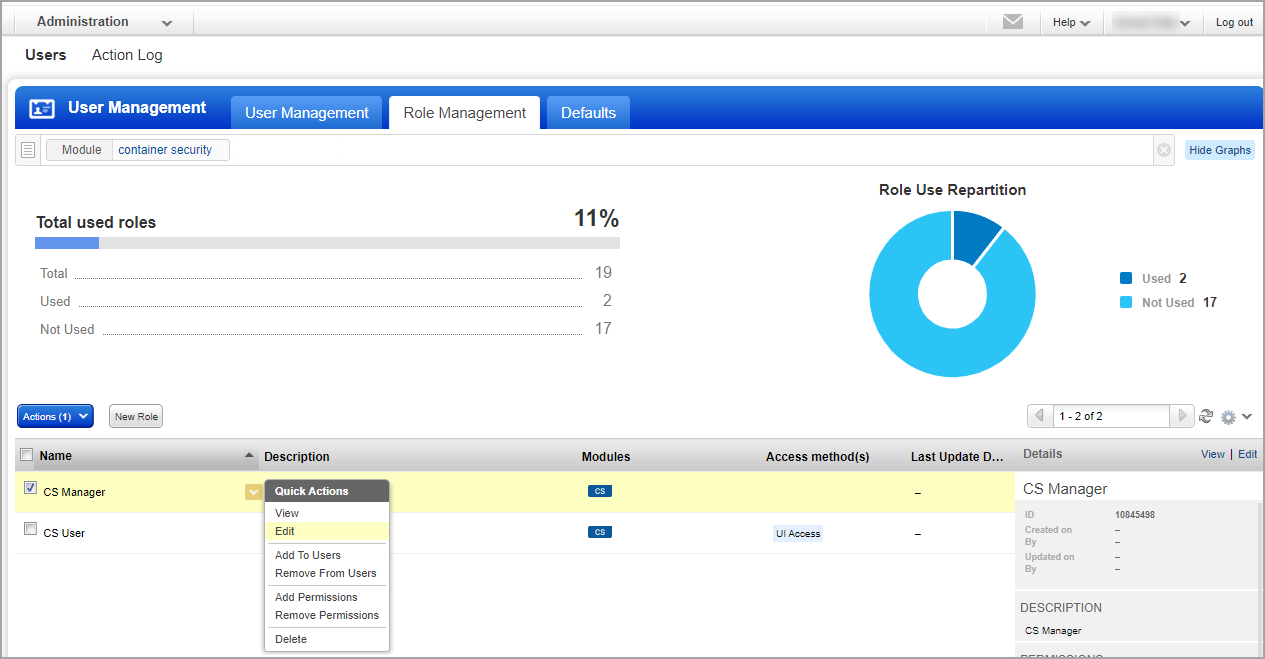
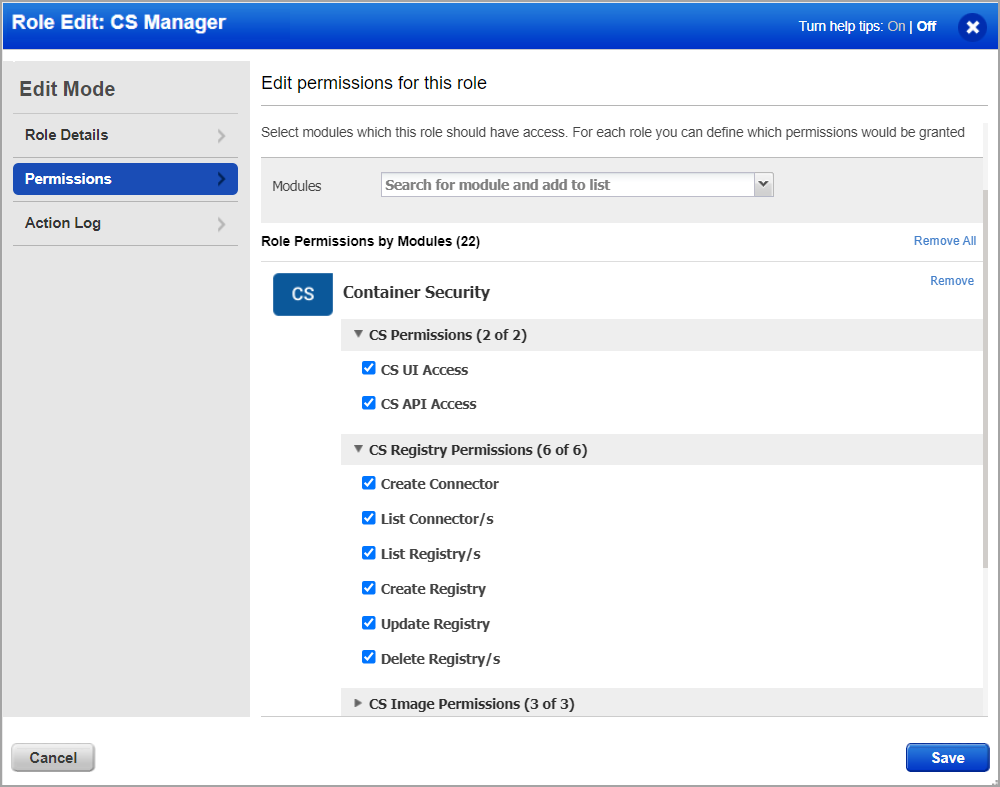
4) Go to the Permissions tab to view permissions for the selected role. At the top, you’ll see Global UI and API access permissions. For Container Security module access and permissions, click the Change link under Role Permissions by Modules.
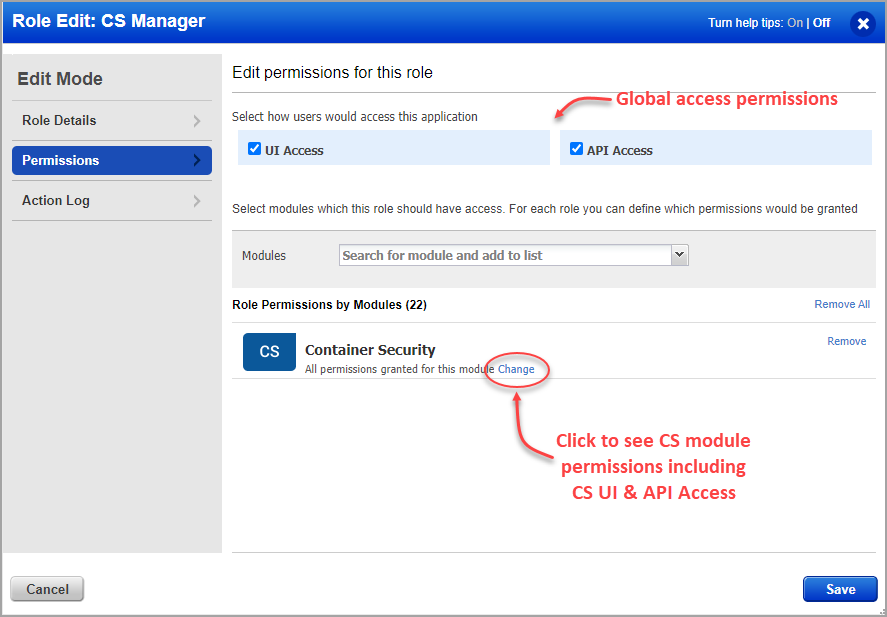
Permissions are grouped by object like registry, image, container, host, etc.
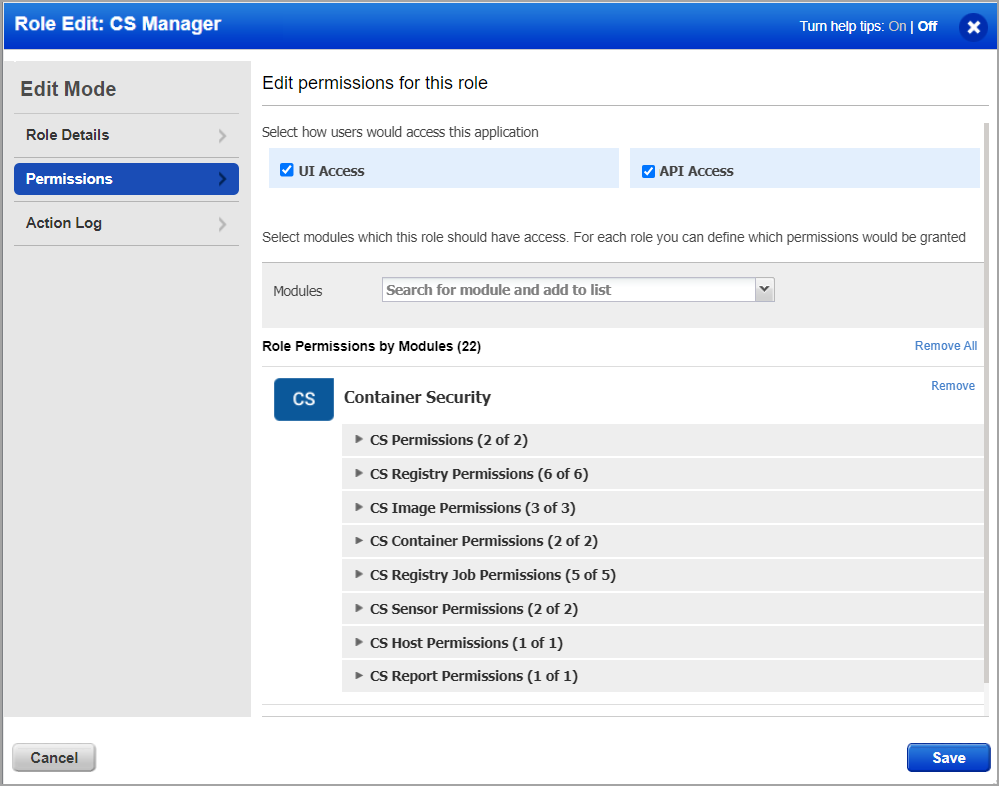
5) Expand any group of permissions to see the individual permissions within the group. Note the CS UI Access and CS API Access permissions. You’ll need to assign these permissions to give users the ability to log into the Container Security UI and API. Click Save after making any changes to the role permissions.
How to Remove Permissions from an Existing User
All users existing prior to the Container Security 1.17 release will automatically get the “CS Manager” role which gives them all Container Security permissions. If you want to limit the permissions for a particular user, then you’ll need to create a custom role and select only the permissions the user should be granted.
Edit the user account from the Users > User Management tab in the Administration utility. Remove the “CS Manager” role from the user since this gives the user all permissions, and assign the new custom role to the user.
How to Add New Users
Any Manager can add new users and assign them roles and permissions. See How to Add Users for more information.
When a User Does Not Have Permission to Perform an Action
If a user is not granted a particular permission then the user will not be able to perform the related action from the UI or API.
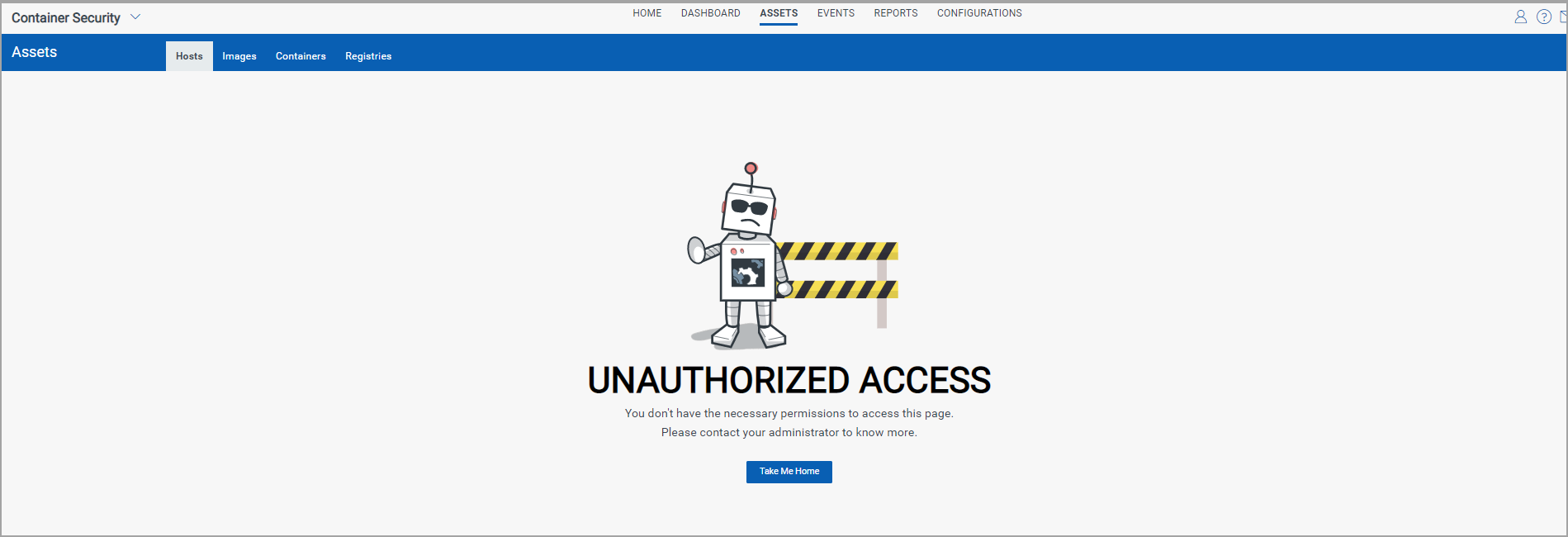
When a user does not have the List permission for an object, then the user will not be able to view the related data list in the UI or fetch the list from the API. In the UI, you’ll see an UNAUTHORIZED ACCESS message when you do not have permission to view the list. In the example below, the user does not have the List Hosts permission.
If the user has the List permission but does not have other permissions like Create, Update, and Delete, then the list will be visible to the user, but the button or menu option for the action will not be visible. For example, if the user does not have the Create Registry permission then the user will not see the New Registry button and will not be able to create registries from the API.