Create runtime policies
Define runtime policies with rules for monitoring and securing running containers.
Go to Configurations > Runtime Policies, and then click the New Policy button.
Basic Details
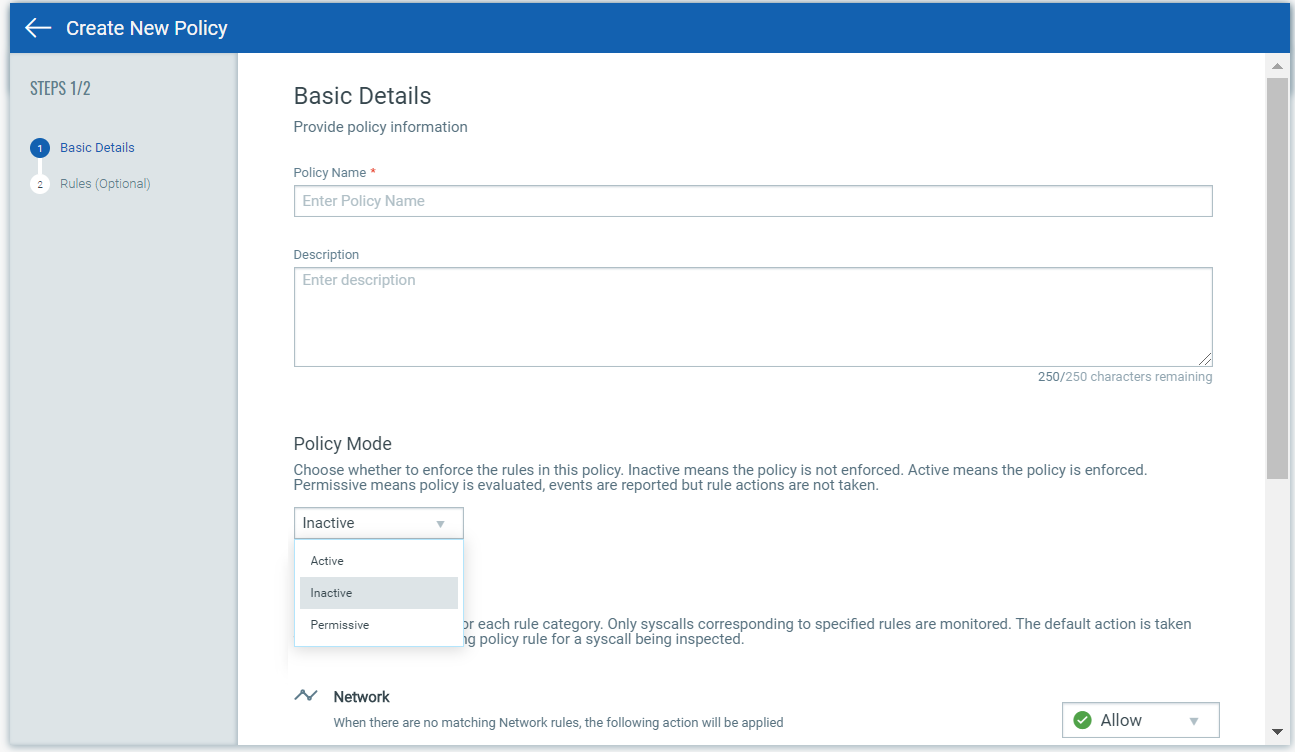
Under Basic Details, you’ll provide a policy name and description, and choose a policy enforcement mode (Active, Inactive, Permissive). The option you pick determines whether or not the policy rules will be enforced on the containers that are spawned from the image. The policy is enforced only when Active is selected. When Permissive is selected, the events are reported but actions are not enforced. Note that you can change this at any time after the policy is saved. See Set Policy Enforcement to learn more.
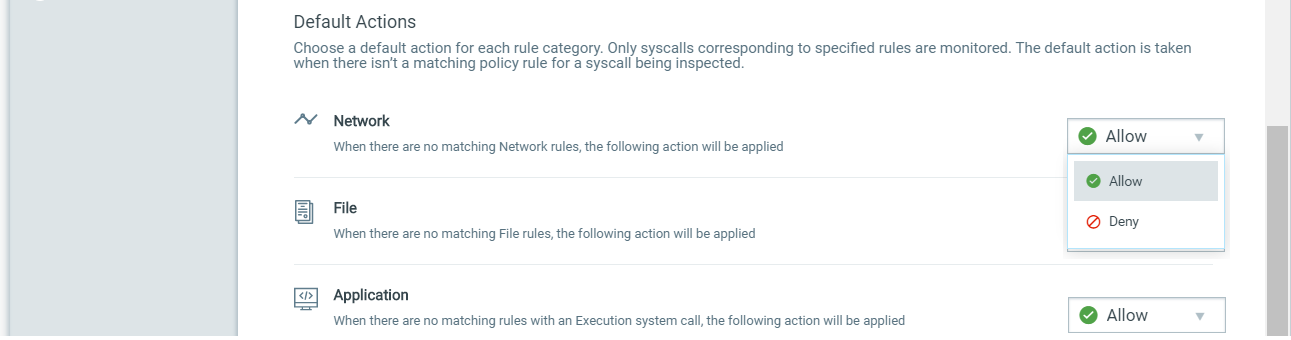
Next, choose default actions for Network, File and Application rule types. This is the default action that will be taken unless there is a policy rule that overwrites this action. For example, you can choose Allow as the default action for Network rules to allow all inbound and outbound traffic to/from the instrumented container and then set up specific Network rules to deny traffic to a particular IP address and port. For Application rules, the default action only applies to rules with an Execution system call selected.
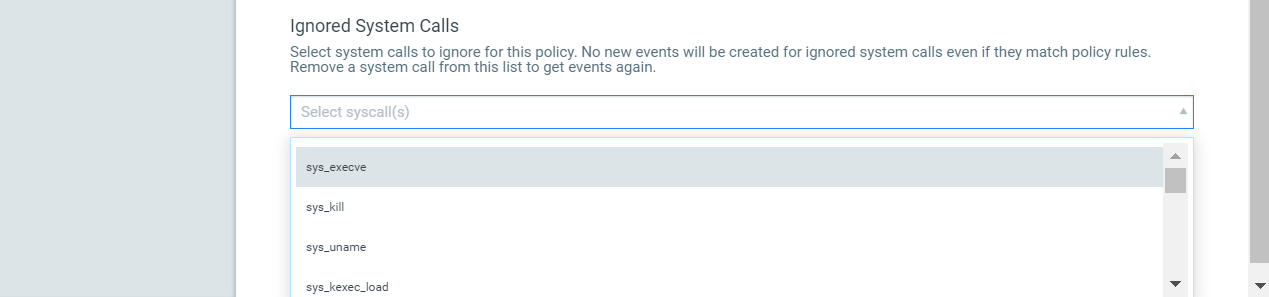
Scroll down further to define a list of system calls that you want to ignore for the policy. Add one or more system calls from the drop-down list. When a system call is ignored, no new events will be created for the system call even if it matches one of the policy rules. This will save you from having to modify all the rules that include a particular system call you want to ignore. If you want to start getting events for an ignored system call in the future, simply edit the policy to remove the system call from the ignored system calls list. You’ll be able to remove individual system calls or clear the entire list.
Rules
Go to the Rules tab to add policy rules. You can add as many rules as you like. Simply click the Add Rule button for Network Rule, File Rule or Application Rule. See Rule Types below to understand the parameters you'll set for each rule type.
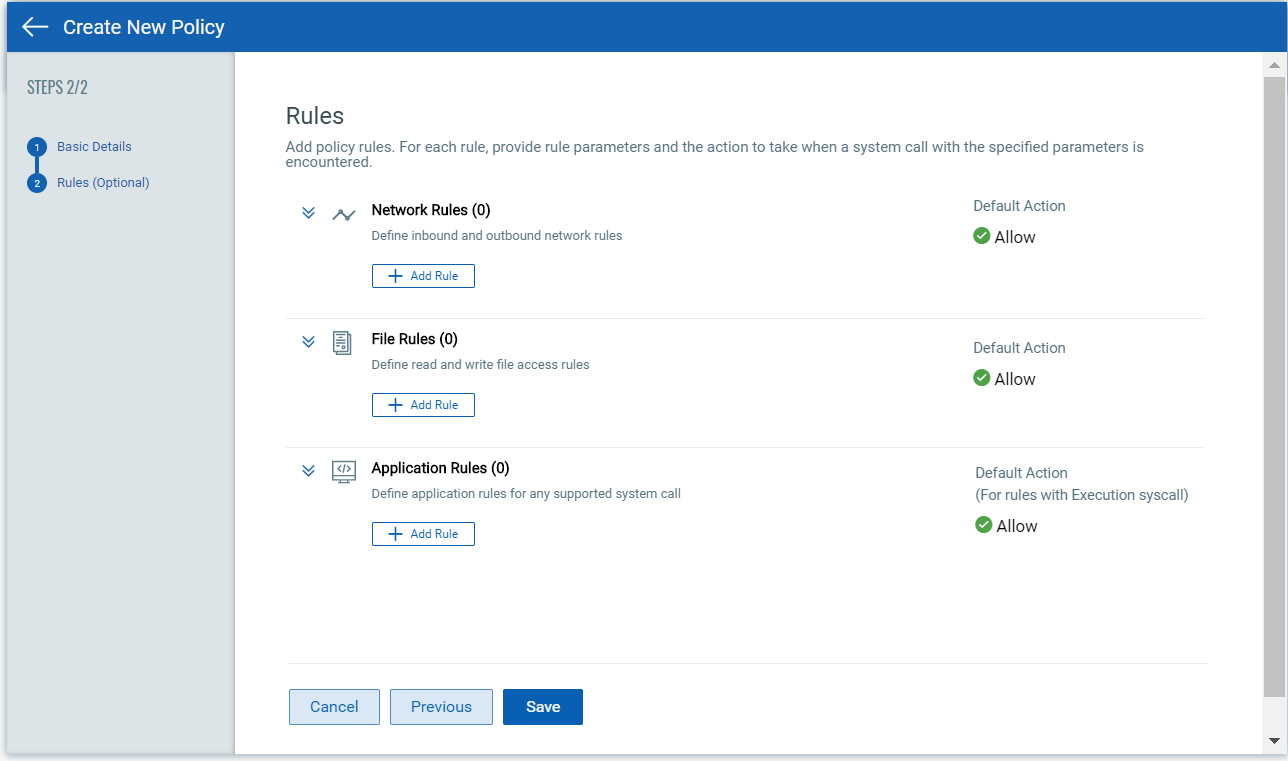
For each new rule, give the rule a name, choose the rule type, set a rule action, and choose whether the rule is enabled or disabled. When you’re done, click Add Rule to save it to your policy. Optionally, click Save and Add another to save the rule and create another rule of the same type.
When you’re done adding rules, click Save. Your new policy will appear on the Runtime Policies list where you can manage it.
Rule Types
Here’s a look at the types of rules you can add to your policies and the parameters you'll need to provide for each rule type. For Network and File rules, we watch particular system calls by default. For Application rules, you'll pick the system call the rule applies to.
Rule Category |
Rule Type |
Default System Call |
Rule Parameters |
Description |
Network |
Network Outbound |
sys_connect |
IP Address & Port |
Allow, deny or monitor outbound traffic. The IP & port refers to the destination IP and port to which the process in the instrumented container is either to be allowed, blocked or monitored. When port is left blank, it acts as a wildcard (*). |
Network |
Network Inbound |
sys_accept, sys_accept4 |
IP Address & Port |
Allow, deny or monitor inbound traffic. The IP refers to the source IP from where the request is made to the instrumented container. Port refers to the bind port or container port. When port is left blank, it acts as a wildcard (*). |
File |
Read |
sys_open |
Program & File |
Allow, deny or monitor read access to a particular file by a particular program |
File |
Write |
sys_write |
Program & File |
Allow, deny or monitor write access to a particular file by a particular program |
Application |
Syscall |
user selected system call |
Program, Argument 1, Argument 2, Argument 3 |
This is an advanced rule type. You must be familiar with the selected system call to know the arguments, if any, that must be defined for the system call. Note that a rule with an Execution syscall only applies to the parent program defined in the rule and not child programs spun up from the parent program. In other words, the child program may be allowed to execute a file that the parent program is prevented from executing. Use * to prevent all programs from executing a certain file. |
Using the API?
You can create and update policies using the Container Runtime Security API. Once saved, your policies will appear in the Container Security UI. Please refer to the Qualys Container Runtime Security API Guide for complete details on API endpoints, input parameters and API samples.