You can set up rules to alert you and keep you aware of certificate or TLS related vulnerabilities and allow for quick remediation. Instead of having to actively monitor the system, these alerts ask for attention and intervention only when necessary, and make you aware of changes or significant findings as soon as the rules are met.
For example, you can set up alerts for
- Certificates expiring in 30/60/90 days
- Self-signed certificates
- Certificates from unapproved CAs
- Certificate instances with low grades
- Certificates with weak key lengths or hashing algorithms
Just tell us what you consider to be a significant finding or event and the mechanism in which you want to be alerted.
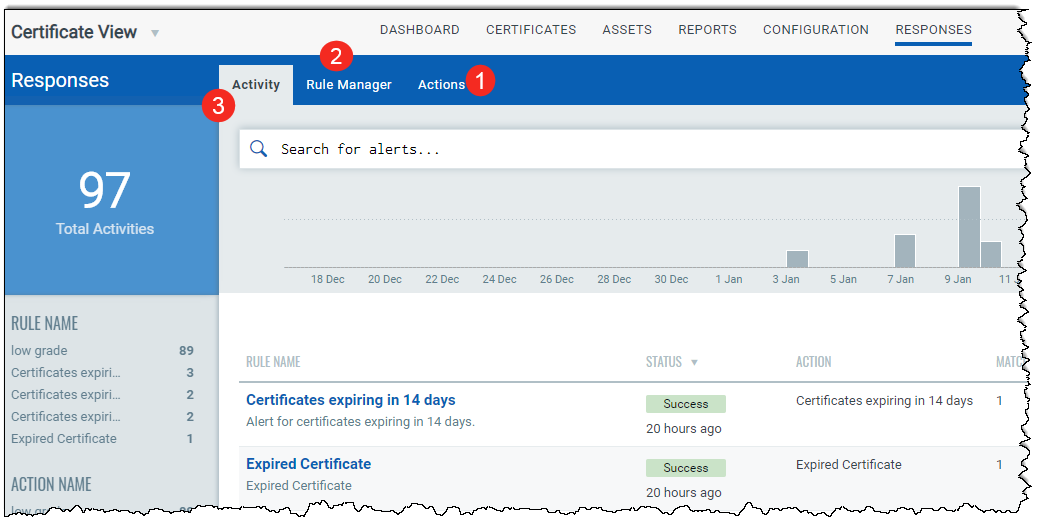
Step 1 - Define actions that the rule must take in response to the alert
Step 2 - Set up your rules in the Rule Manager tab
Step 3 - Monitor all the alerts that were sent after the rules were triggered

That's it! You are all set to start being alerted about your certificate findings!
Assign permissions related to alerting to your user. Depending on the permissions assigned, the user can perform actions like creating, editing, or deleting rules and actions.
Using the Administration module, the Manager user for that subscription can assign these permissions to other users.
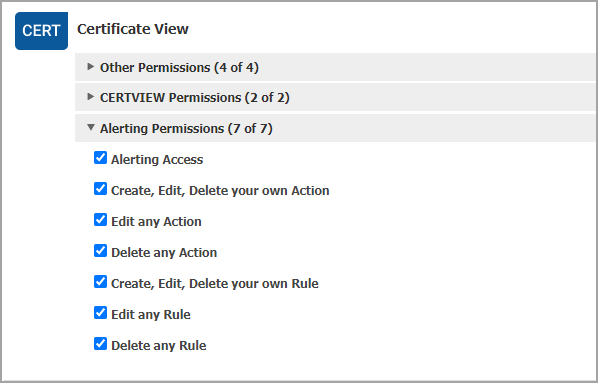
Only the user having the Alerting Access permission can view the Responses tab on the Certificate View UI.